Cybersecurity researchers have uncovered a sophisticated phishing campaign that exploited the legitimate infrastructure of Nifty[.]com, a well-known project management platform, to
target organizations globally. This campaign remained active for several months before detection and highlights a growing trend where threat actors misuse trusted web services to bypass security defenses and gain victims' trust.
The attackers manipulated Nifty[.]com’s URL shortening and redirect features to create seemingly legitimate links that directed users to credential harvesting sites. These phishing attempts primarily targeted corporate email accounts, with messages crafted to appear as authentic business communications. Using Nifty[.]com’s trusted domain name helped the attackers bypass email security filters and increase user confidence in the links.
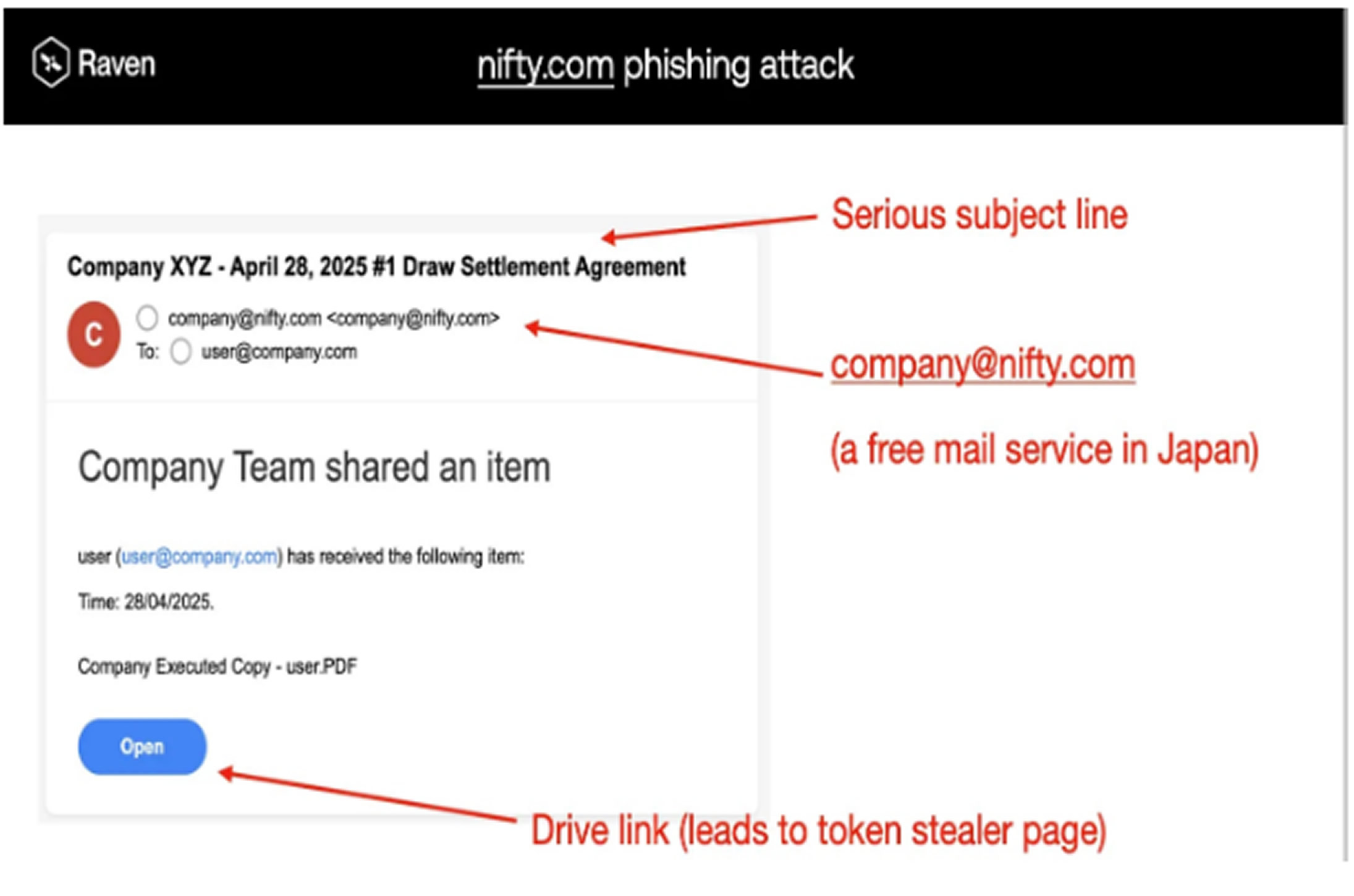
Analysts from Raven noted that the campaign showed signs typical of advanced persistent threat groups, such as thorough reconnaissance and highly personalized phishing messages. The attackers conducted extensive research on their victims, including company-specific terminology and references to ongoing projects, to increase the chance of stealing credentials. This level of social engineering sophistication suggests the involvement of well-resourced and experienced threat actors.
The campaign impacted multiple sectors, particularly financial services, healthcare, and technology. Initial estimates indicate that hundreds of organizations were targeted, with some suffering successful breaches leading to unauthorized access to sensitive data and potential lateral movement within networks. The attackers displayed patience by maintaining access to compromised accounts for weeks before escalating their activities.
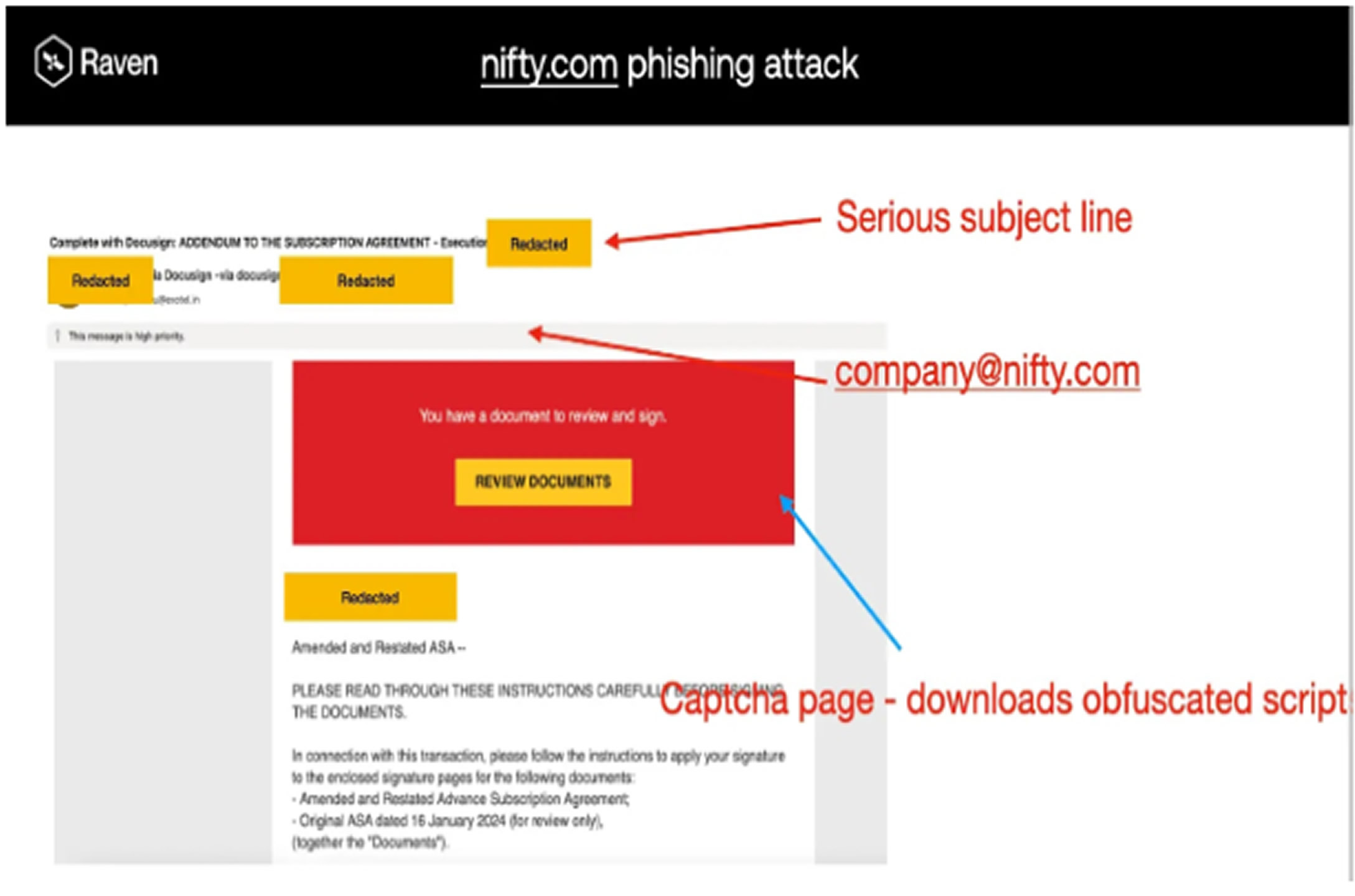
The phishing infrastructure demonstrated advanced evasion techniques designed to evade modern security controls. Attackers used multiple layers of redirection through Nifty[.]com’s legitimate redirect functionality. The redirection chain began with shortened URLs embedded in phishing emails, passing through several intermediate domains that performed device fingerprinting and geolocation checks before delivering victims to the final credential harvesting sites.
This multi-step redirection served to hide the true destination from security scanners, gather victim intelligence, and deliver tailored malicious payloads based on the victim’s device. The intermediate pages used JavaScript-based browser fingerprinting to identify security researchers and automated tools, redirecting suspicious traffic to harmless pages while showing malicious content only to real targets. The infrastructure also employed time-based delays and virtual machine artifact detection to thwart automated analysis.
These complex evasion methods allowed the campaign to operate undetected for an extended time. The final credential harvesting pages were carefully designed to mimic legitimate login portals, complete with valid SSL certificates and authentic visual elements to deceive even security-aware users effectively.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.


