A hacking group known as Elusive Comet is targeting cryptocurrency users through a sophisticated social engineering scheme that leverages Zoom’s
remote control feature to gain unauthorized access to victims’ devices.
This feature, commonly used for collaboration, allows one Zoom participant to take control of another’s computer. In this attack, it becomes a tool for cybercriminals.
Cybersecurity firm Trail of Bits uncovered the campaign and reported that it closely resembles the strategy used by the Lazarus Group in the $1.5 billion Bybit crypto theft. Unlike typical cyberattacks that exploit software vulnerabilities, this campaign manipulates legitimate workflows to deceive users.
Fake Bloomberg Interviews via Zoom
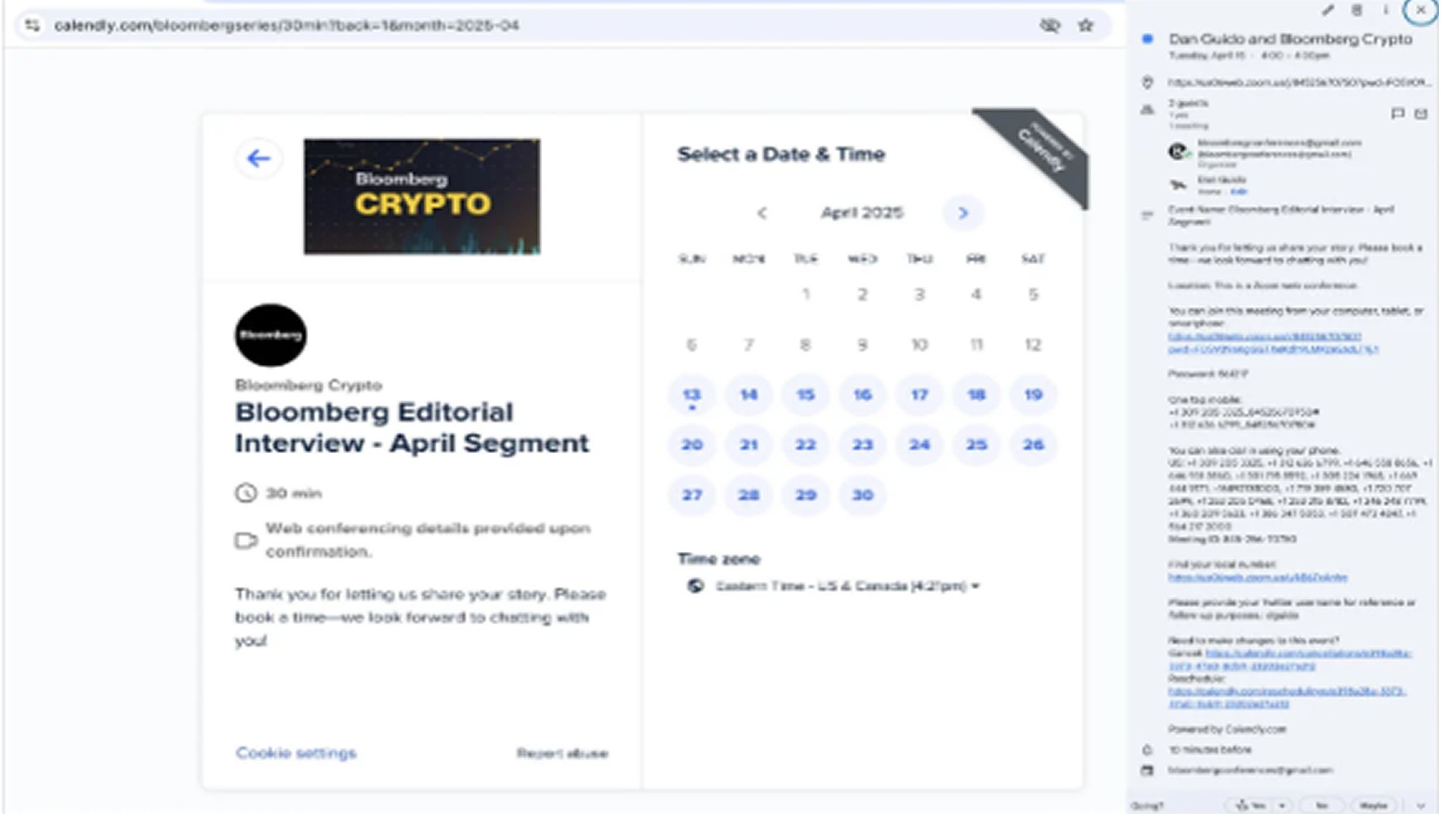
The attack begins with a fraudulent invitation to a supposed “Bloomberg Crypto” interview. These invites are sent to high-profile crypto users through social media platform X (formerly Twitter) or email (e.g., bloombergconferences[@]gmail.com), using fake accounts that impersonate crypto journalists or Bloomberg-affiliated entities.
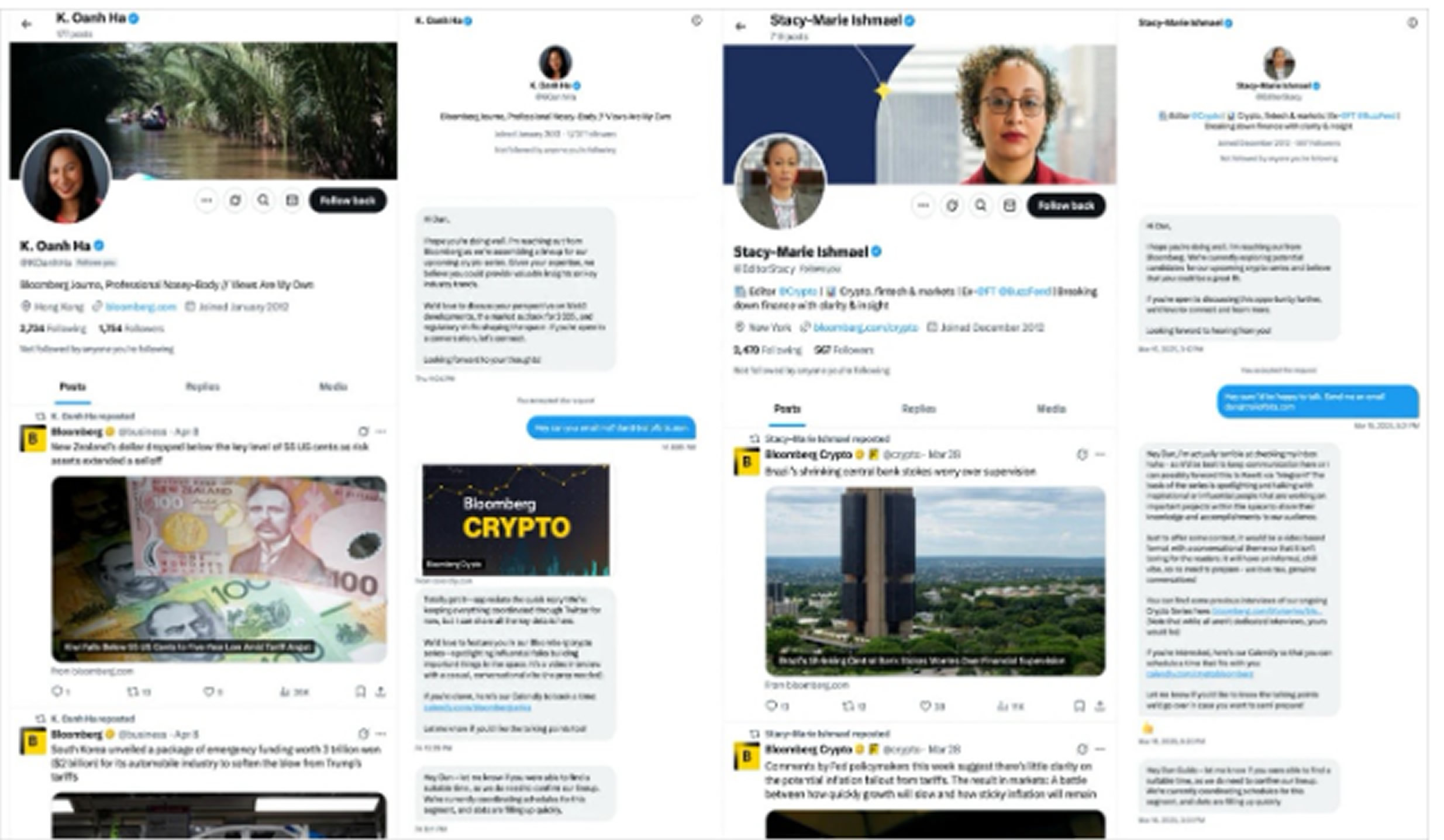
Victims receive legitimate-looking Calendly links to schedule Zoom interviews, which builds credibility. Once in the Zoom call, the attacker initiates screen sharing and sends a request for remote control access.
To further mislead the victim, the attacker changes their Zoom display name to “Zoom”, so the access request reads: “Zoom is requesting remote control of your screen.” This tactic causes users to believe the prompt is from the Zoom platform itself.
Granting access gives the attacker full control over the target's machine—allowing them to steal data, install malware, manipulate crypto transactions, or plant backdoors for future exploitation.
Trail of Bits warns, “This attack is especially dangerous because the request looks like a routine Zoom notification. Users accustomed to clicking ‘Approve’ might unintentionally surrender full control of their systems.”
Mitigation Strategies
To combat this threat, Trail of Bits advises organizations to enforce system-wide Privacy Preferences Policy Control (PPPC) settings to block unauthorized accessibility access. In high-security environments, especially those handling sensitive data or cryptocurrency, they recommend removing the Zoom client altogether and switching to browser-based alternatives.
“For organizations dealing with digital assets, the slight inconvenience of avoiding Zoom’s desktop app is worth the significant reduction in security risk,” the report concludes.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.


