Threat hunters have uncovered a new campaign that uses search engine optimization (SEO) poisoning techniques to target employee mobile devices and carry out payroll fraud.
ReliaQuest first identified this activity in May 2025 when an unnamed customer in the manufacturing sector was targeted. The attackers created fake login pages to access the company's payroll portal and redirected employee paychecks into accounts they controlled.
According to ReliaQuest, the attackers used compromised home office routers and mobile networks to mask their activity. This tactic helped them evade detection and bypass standard security defenses.
The attackers focused specifically on employee mobile devices, deploying a fake website that mimicked the company’s login page. With the stolen credentials, they accessed the payroll portal, altered direct deposit information, and rerouted employees' paychecks to their own accounts.
While no specific hacking group has been linked to the attacks, ReliaQuest believes the activity is part of a wider campaign. The company investigated two similar incidents in late 2024.
The attack often begins when an employee searches for their company’s payroll portal online. Malicious websites that look like the real portal appear at the top of search results through sponsored links. Clicking on one of these leads to a WordPress site that redirects mobile users to a phishing page disguised as a Microsoft login portal.
Once credentials are entered on the fake page, they are sent to a site controlled by the attackers. A two-way WebSocket connection is also established to alert the threat actor in real time, using a push notification service powered by Pusher. This allows the attackers to act quickly before the credentials are changed.
Targeting mobile devices gives the attackers two key advantages. First, mobile devices often lack the enterprise-level security features found on desktop computers. Second, they typically operate outside the corporate network, reducing visibility and making it harder to investigate the attacks.
ReliaQuest noted that by focusing on unprotected mobile devices, the attackers not only avoid detection but also make it difficult for security teams to analyze phishing websites. This disruption delays the process of identifying and blacklisting malicious sites.
In addition, the login attempts appear to come from residential IP addresses linked to home office routers, including those from brands like ASUS and Pakedge. This suggests the attackers exploit common vulnerabilities such as default passwords or misconfigurations in these devices to carry out brute-force attacks. Once compromised, the routers are infected with malware and added to proxy botnets that are rented out to other cybercriminals.
ReliaQuest emphasized that proxy networks using residential or mobile IPs make it much harder for organizations to detect or investigate the activity. These IP addresses are less likely to be flagged as suspicious compared to VPNs, which are often blacklisted. Proxy networks also help attackers mimic the geographic location of the target, avoiding detection by location-based security measures.
Meanwhile, Hunt.io recently reported a phishing campaign using a fake Adobe Shared File service page to steal Microsoft Outlook credentials. The phishing pages are created using the W3LL phishing kit.
This disclosure comes alongside the identification of a new phishing kit called CoGUI, which is actively being used to target Japanese organizations. The kit impersonates well-known brands such as Amazon, PayPay, MyJCB, Apple, Orico, and Rakuten. Between January and April 2025, around 580 million emails were sent as part of campaigns using this kit.
According to Proofpoint, CoGUI uses advanced evasion methods like geofencing, header filtering, and fingerprinting to avoid detection. The aim is to steal usernames, passwords, and payment details. The phishing emails contain links that lead to fake login pages, although CoGUI does not have the capability to capture multi-factor authentication (MFA) codes.
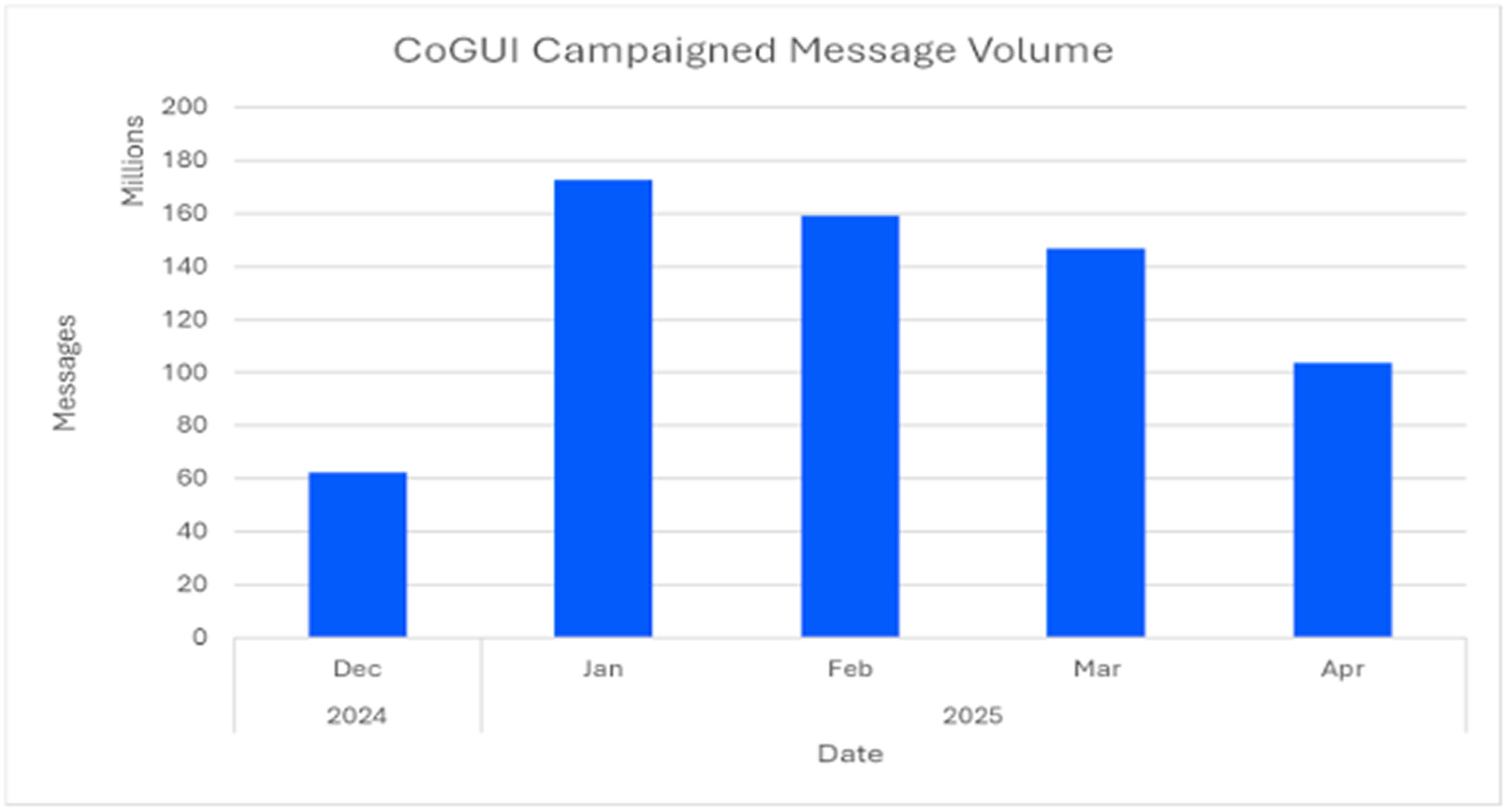
CoGUI has been in use since at least October 2024 and appears to be related to the Darcula phishing toolkit. Both may belong to the same Chinese phishing-as-a-service (PhaaS) ecosystem known as the Smishing Triad, which also includes Lucid and Lighthouse. Unlike CoGUI, Darcula focuses more on mobile phishing and credit card theft.
PRODAFT noted that Darcula is becoming increasingly accessible and may pose a growing threat. Lucid, on the other hand, remains more discreet. Identifying phishing kits like Lucid is difficult because the messages and links they use often rely on common delivery platforms.
Another emerging smishing kit, Panda Shop, was discovered by Resecurity in March 2025. This kit uses Telegram channels and automated bots to deliver its phishing services. The phishing pages imitate major brands and government platforms to steal personal data. Stolen credit card details are sent to underground carding markets where they are sold to other criminals.
Resecurity noted that Chinese cybercriminal groups behind smishing campaigns show little concern for law enforcement. Operating from within China, they carry out various illegal activities without restraint. The group behind Panda Shop offers a crime-as-a-service platform that allows customers to distribute smishing messages through iMessage and Android RCS using hacked Apple and Gmail accounts purchased in bulk.
Based on the similarities in the phishing kits, Resecurity believes Panda Shop is likely operated by members of the Smishing Triad. The kit is widely used for fraud involving Google Wallet and Apple Pay.
According to Resecurity, those involved in smishing campaigns are closely tied to groups responsible for merchant fraud and money laundering. Smishing plays a key role in these operations by collecting large volumes of compromised data from unsuspecting victims.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



