Fake AI Tool Installers Spreading Ransomware and Destructive Malware
Cybercriminals are increasingly exploiting the popularity of artificial intelligence (AI) tools by using fake installers for platforms like OpenAI ChatGPT and InVideo AI to distribute a range of malicious threats. These include CyberLock and Lucky_Gh0$t ransomware families, as well as a new malware strain named Numero.
According to a new report from Cisco Talos, CyberLock ransomware is developed using PowerShell and targets specific file types for encryption. Lucky_Gh0$t, a variant of the Yashma ransomware, marks the sixth iteration in the Chaos ransomware family and features only minor modifications.
Numero, the newly identified malware takes a more destructive approach. It manipulates the graphical user interface (GUI) elements in Windows to render infected systems unusable.
Targeted Victims and Attack Vector
The legitimate versions of these AI tools are widely used in B2B sales and marketing sectors, making individuals and companies in these industries a prime target for threat actors.
One such attack involves a counterfeit website, novaleadsai[.]com, which mimics a lead monetization platform called NovaLeads. This site is likely promoted using SEO poisoning to push it higher in search engine results. Users are enticed with an offer of free access for one year, followed by a $95 monthly subscription. What actually downloads is a ZIP file containing a .NET executable named "NovaLeadsAI.exe," compiled on February 2, 2025 the same day the fake domain was registered.
Once launched, the executable acts as a loader for CyberLock ransomware, escalating privileges and encrypting files across the "C:", "D:", and "E:" partitions. Victims are presented with a ransom demand of $50,000 in Monero, with payment required within three days.
The ransom note takes an unusual moral stance, claiming the money will support women and children in Palestine, Ukraine, Africa, and Asia. It states, "This amount is small in comparison to the innocent lives that are being lost," framing the cyberattack as a form of forced charity.
To prevent forensic recovery, the ransomware uses "cipher.exe" with the "/w" switch to wipe free disk space.
Lucky_Gh0$t Disguised as ChatGPT
Cisco Talos also found Lucky_Gh0$t ransomware being spread through a fake installer for a premium version of ChatGPT. The malicious SFX (self-extracting) installer includes:
- A ransomware executable labeled "dwn.exe" (to mimic Microsoft’s "dwm.exe")
- Legitimate Microsoft open-source AI tools from GitHub
When executed, the SFX script runs the ransomware. Lucky_Gh0$t encrypts files smaller than 1.2GB and deletes volume shadow copies and backups. Victims receive a ransom note with a unique decryption ID and are instructed to communicate via the Session messaging app for payment instructions.
InVideo AI Installer Spreads Numero Malware
Threat actors are also leveraging a fake InVideo AI installer to spread Numero, a destructive malware. The installer contains:
- A Windows batch file
- A Visual Basic script
- The Numero executable
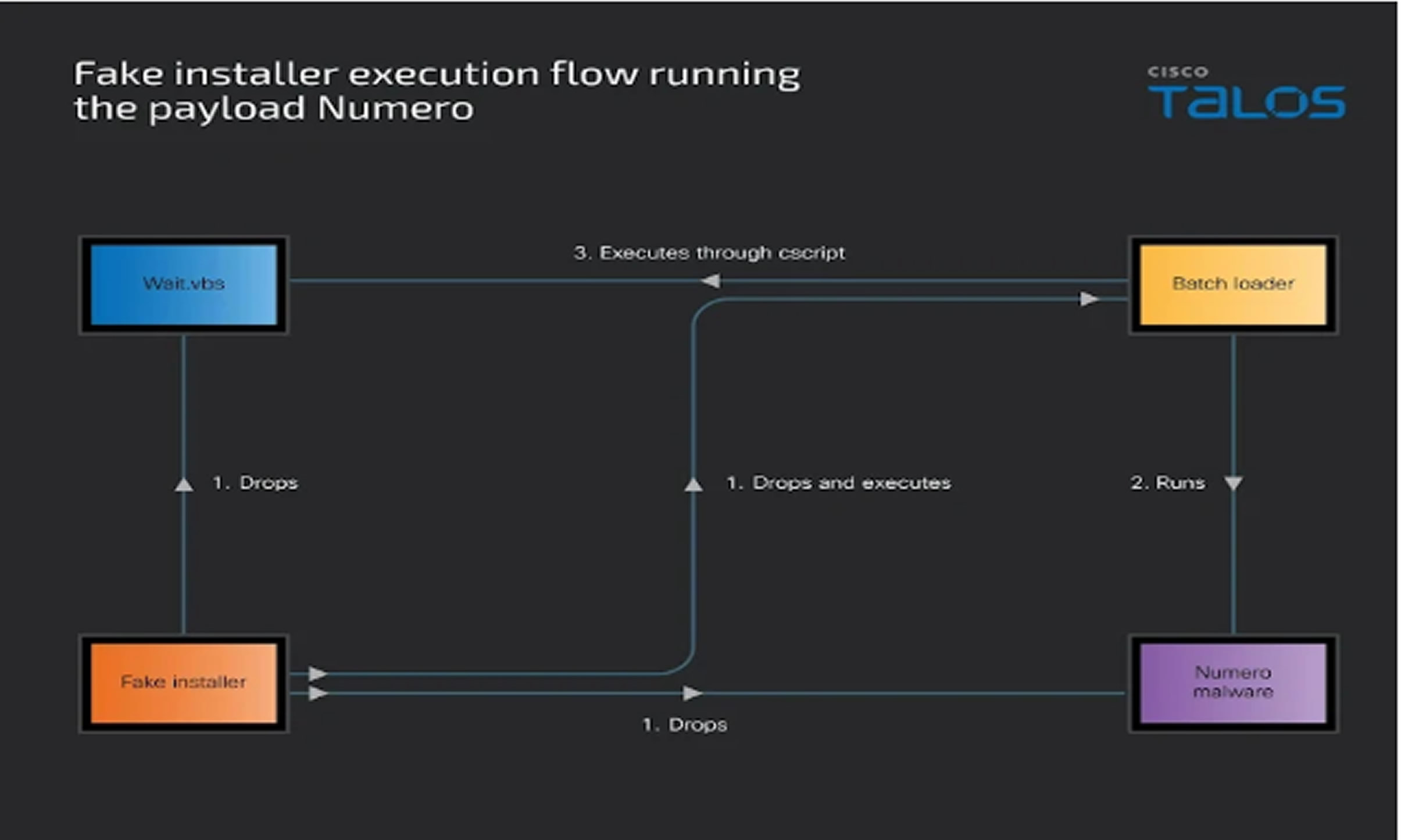
The batch file launches an infinite loop through Windows shell, triggering Numero repeatedly. It pauses execution for 60 seconds using the VB script, then terminates and restarts the malware process.
Compiled on January 24, 2025, Numero checks for debugging tools and malware analysis software. It corrupts the Windows desktop by overwriting the title bar, buttons, and content with the string "1234567890" effectively crippling the user interface.
Broader Campaign via Fake AI Tools and Malvertising
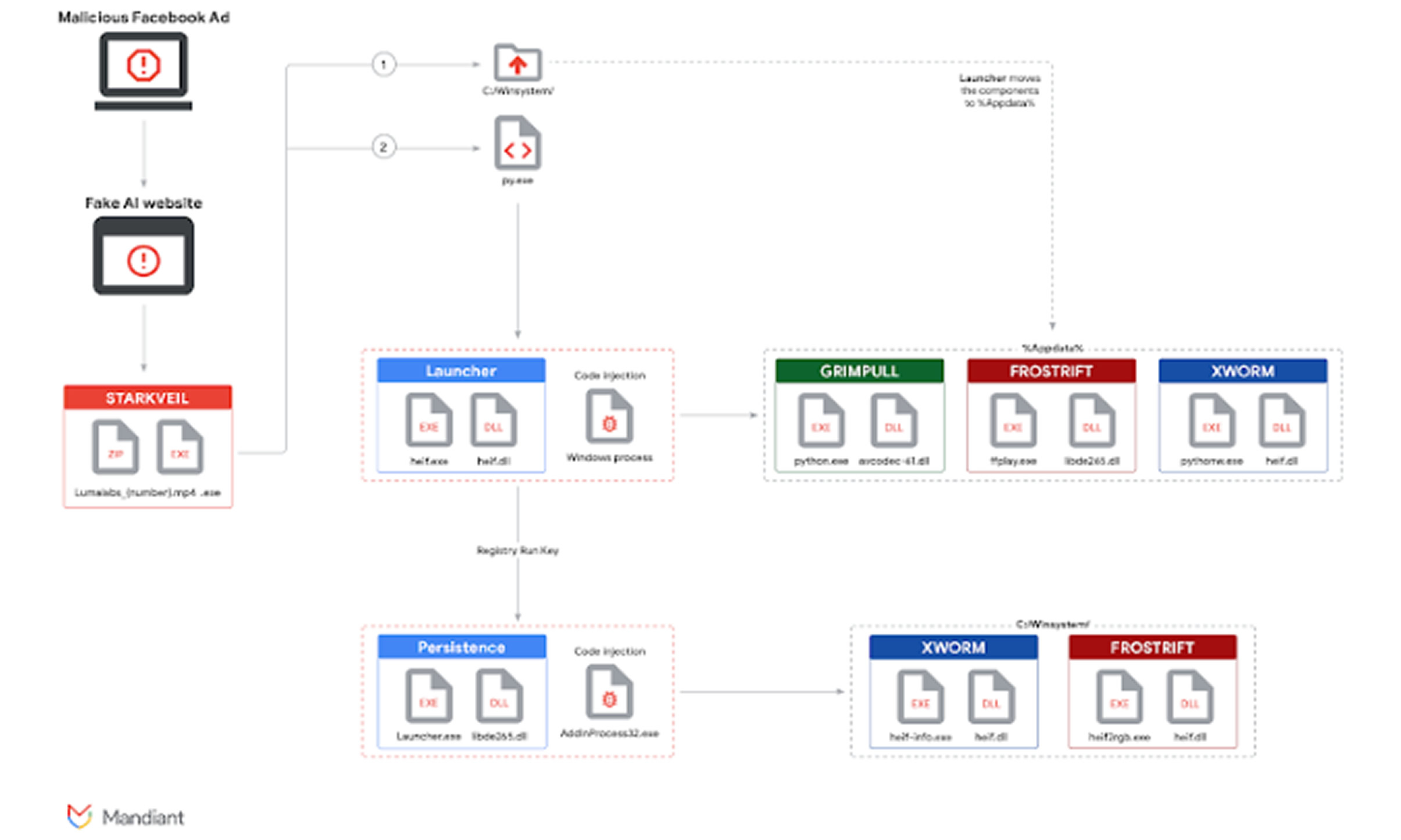
In a related disclosure, Google’s Mandiant reported a malvertising campaign using platforms like Facebook and LinkedIn to distribute fake AI video generators such as Luma AI, Canva Dream Lab, and Kling AI. The operation is linked to a threat cluster tracked as UNC6032, believed to be based in Vietnam. The campaign has been active since mid-2024.
Users lured to these fake sites are prompted to generate a video. Regardless of input, a Rust-based dropper named STARKVEIL is downloaded instead. This payload deploys three modular malware families:
- GRIMPULL – A downloader that uses TOR to retrieve .NET payloads, loading them directly into memory.
- FROSTRIFT – A backdoor that collects system info and scans for 48 password manager and cryptocurrency wallet extensions in Chromium browsers.
- XWorm – A remote access trojan (RAT) offering features like keylogging, screen capture, command execution, and data theft.
STARKVEIL also activates a Python-based dropper, COILHATCH, which uses DLL side-loading to execute these three malware types.
Security researchers warn that the growing adoption of AI tools across industries makes everyone a potential target, not just developers or designers. As Mandiant noted, "The temptation to try the latest AI tool can lead to anyone becoming a victim."
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.


