Cybersecurity researchers have identified a new phishing campaign delivering a malware
known as Horabot, which is targeting Windows users in Latin American countries such as Mexico, Guatemala, Colombia, Peru, Chile, and Argentina.
According to Cara Lin, a researcher at Fortinet FortiGuard Labs, the campaign uses deceptive emails that appear to be invoices or financial documents. These emails trick recipients into opening malicious attachments capable of stealing email credentials, harvesting contact lists, and installing banking trojans.
The campaign was detected by the network security company in April 2025 and has primarily targeted Spanish-speaking users. The attackers have also been observed sending phishing emails directly from compromised users' mailboxes using Outlook COM automation, allowing the malware to spread across both personal and corporate networks. The attackers use a combination of VBScript, AutoIt, and PowerShell scripts to perform system reconnaissance, collect credentials, and deploy additional malicious components.
Cisco Talos first reported on Horabot in June 2023 and found that it had been active since at least November 2020. Evidence suggests that a Brazilian threat actor is responsible for the attacks.
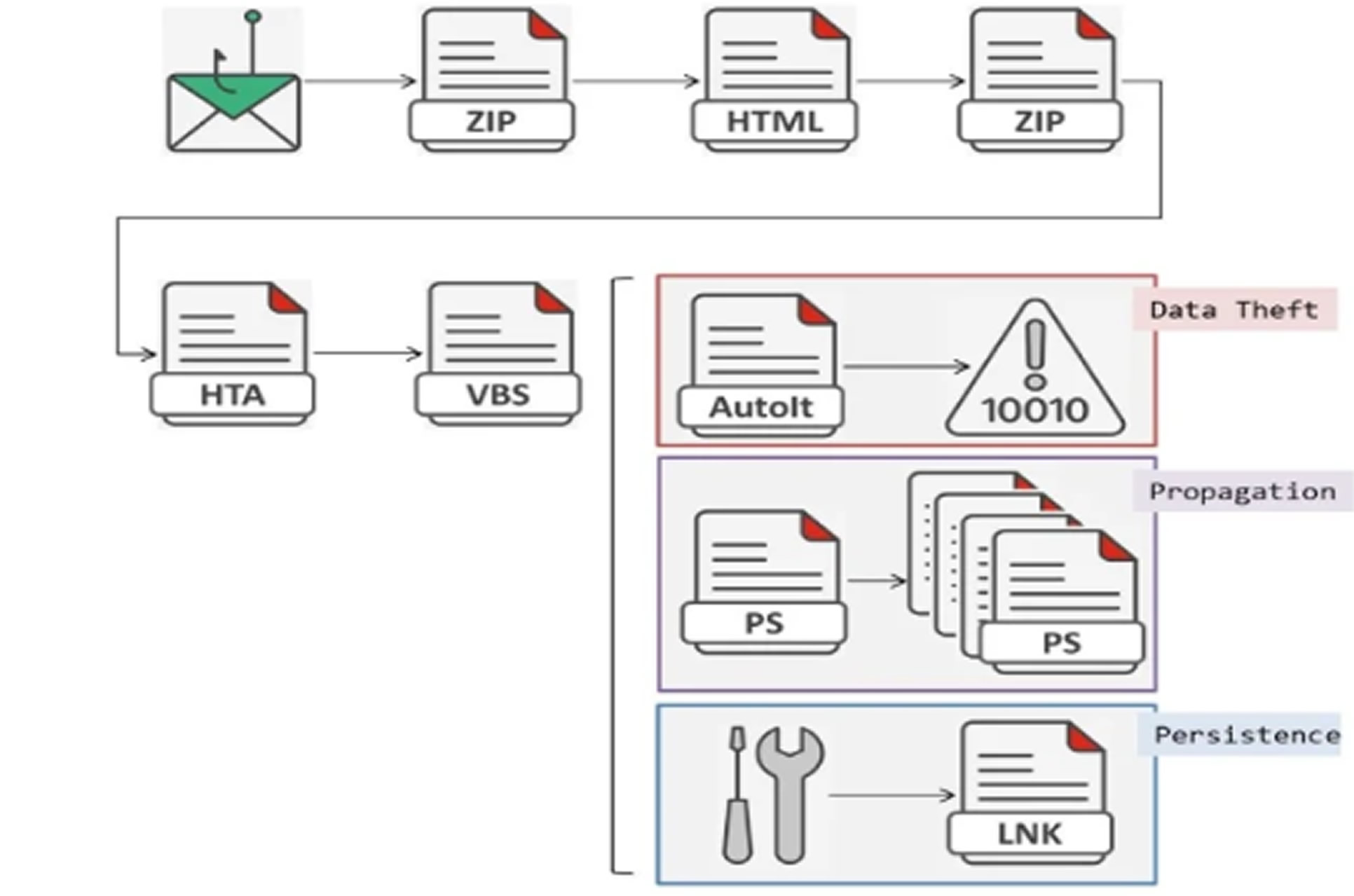
In a separate investigation, Trustwave SpiderLabs disclosed another phishing campaign in the same region last year. This campaign shared characteristics with the Horabot malware. The recent attacks begin with an email that uses an invoice theme to entice recipients into opening a ZIP archive. While it appears to contain a PDF file, the archive actually holds a malicious HTML file encoded in Base64, which connects to a remote server to download further payloads.
This next-stage payload is another ZIP file containing an HTML Application (HTA) file. The HTA file loads a script from a remote server, which in turn injects a Visual Basic Script (VBScript). This script performs several system checks and terminates its process if Avast antivirus is detected or if the system is running in a virtual machine.
Once the VBScript passes the checks, it collects basic system data and sends it to a remote server. It also downloads additional malware, including an AutoIt script that uses a malicious DLL to install the banking trojan. A PowerShell script is used to distribute phishing emails by compiling a list of target addresses from Outlook contacts.
Lin noted that the malware also targets browser data from several web browsers, including Brave, Yandex, Epic Privacy Browser, Comodo Dragon, Cent Browser, Opera, Microsoft Edge, and Google Chrome. Alongside stealing data, Horabot tracks user activity and displays fake pop-up windows to capture sensitive login information.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.


