CyberArk researchers have uncovered a new malware campaign targeting users searching for pirated software.
This campaign deploys a previously undocumented clipper malware named MassJacker.
Clipper malware, categorized as cryware by Microsoft, is designed to monitor clipboard activity and facilitate cryptocurrency theft. It does so by replacing copied cryptocurrency wallet addresses with attacker-controlled ones, diverting funds to cybercriminals instead of the intended recipients.
According to security researcher Ari Novick, the infection process begins on a website called pesktop[.]com, which masquerades as a source for pirated software but actually spreads various forms of malware.
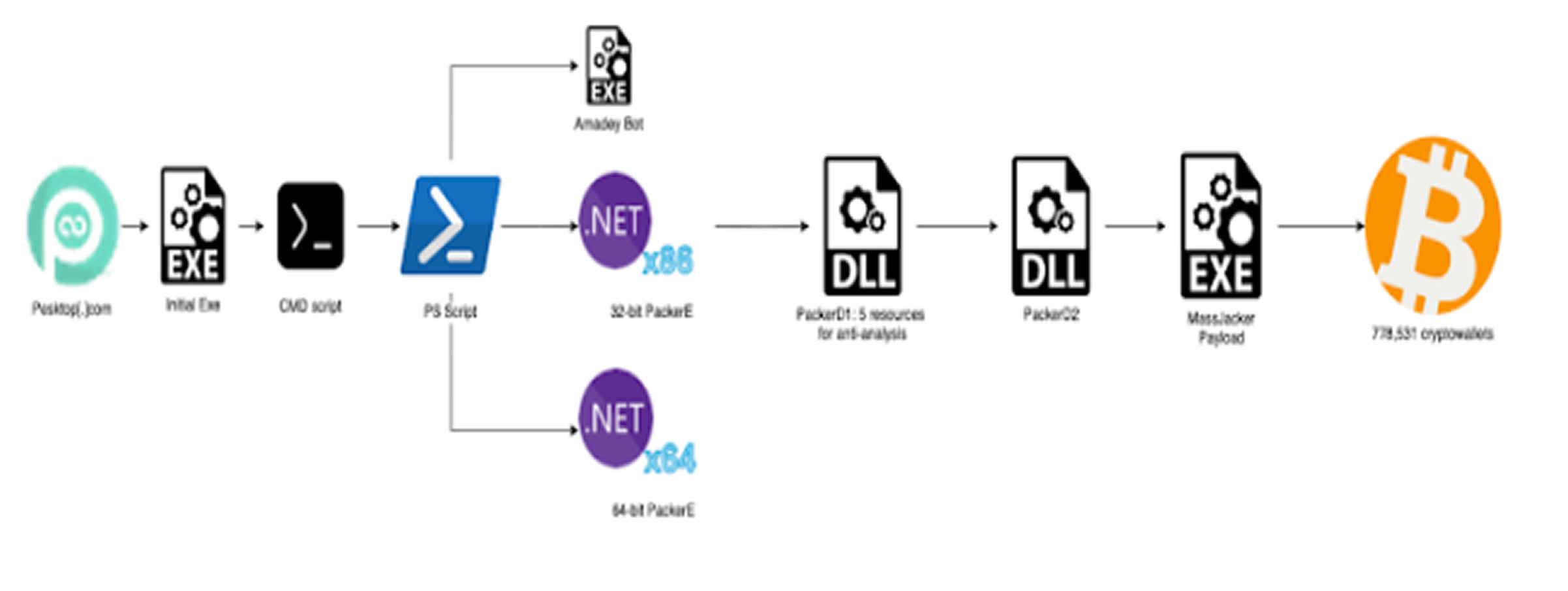
Once executed, the initial file triggers a PowerShell script that installs Amadey botnet malware along with two .NET binaries compiled for both 32-bit and 64-bit architectures.
One of these binaries, dubbed PackerE, downloads an encrypted DLL, which then loads a secondary DLL. This secondary DLL injects the MassJacker payload into a legitimate Windows process, "InstalUtil.exe." To evade detection and analysis, the encrypted DLL employs advanced techniques such as Just-In-Time (JIT) hooking, metadata token mapping to obscure function calls, and a custom virtual machine to interpret commands instead of executing standard .NET code.
MassJacker includes its own anti-debugging mechanisms and scans clipboard content for cryptocurrency wallet addresses using predefined regular expressions. It communicates with a remote server to retrieve a list of wallet addresses under the attacker’s control.
"MassJacker creates an event handler that activates whenever the victim copies something," Novick explained. "If it detects a cryptocurrency wallet address, it replaces the copied content with one of the attacker’s wallets from the downloaded list."
CyberArk identified more than 778,531 unique wallet addresses linked to the attackers. However, only 423 of these contained funds, totaling approximately $95,300. The total cryptocurrency amount that passed through these wallets before being moved elsewhere is estimated at $336,700.
Additionally, a single wallet linked to the operation holds approximately $87,000 (600 SOL), with over 350 transactions funneling funds from various sources into it.
The identity of the group behind MassJacker remains unknown. However, researchers have found code similarities with another malware strain, MassLogger, which also employs JIT hooking to evade analysis.


