Microsoft Exposes ClickFix Phishing Campaign Targeting Hospitality Sector via Fake Booking.com Emails
Microsoft has uncovered a phishing campaign targeting the hospitality sector, where cybercriminals impersonate Booking.com to deploy credential-stealing malware using the ClickFix social engineering technique.
According to Microsoft, the campaign tracked as Storm-1865 began in December 2024 and aims to commit financial fraud. It primarily targets hospitality professionals in North America, Oceania, South and Southeast Asia, and various regions of Europe.
The attack starts with phishing emails claiming to be from Booking.com, alerting recipients to a negative review and requesting their feedback. These emails contain links or PDF attachments directing victims to what appears to be a legitimate Booking.com page. However, the link actually leads to a fake CAPTCHA page, subtly overlaid on a simulated Booking.com site to enhance credibility.
Using ClickFix, the attack tricks victims into copying and pasting a command into the Windows Run dialog, executing malware. The command leverages the legitimate mshta.exe binary to deploy malware strains such as XWorm, Lumma Stealer, VenomRAT, AsyncRAT, Danabot, and NetSupport RAT.
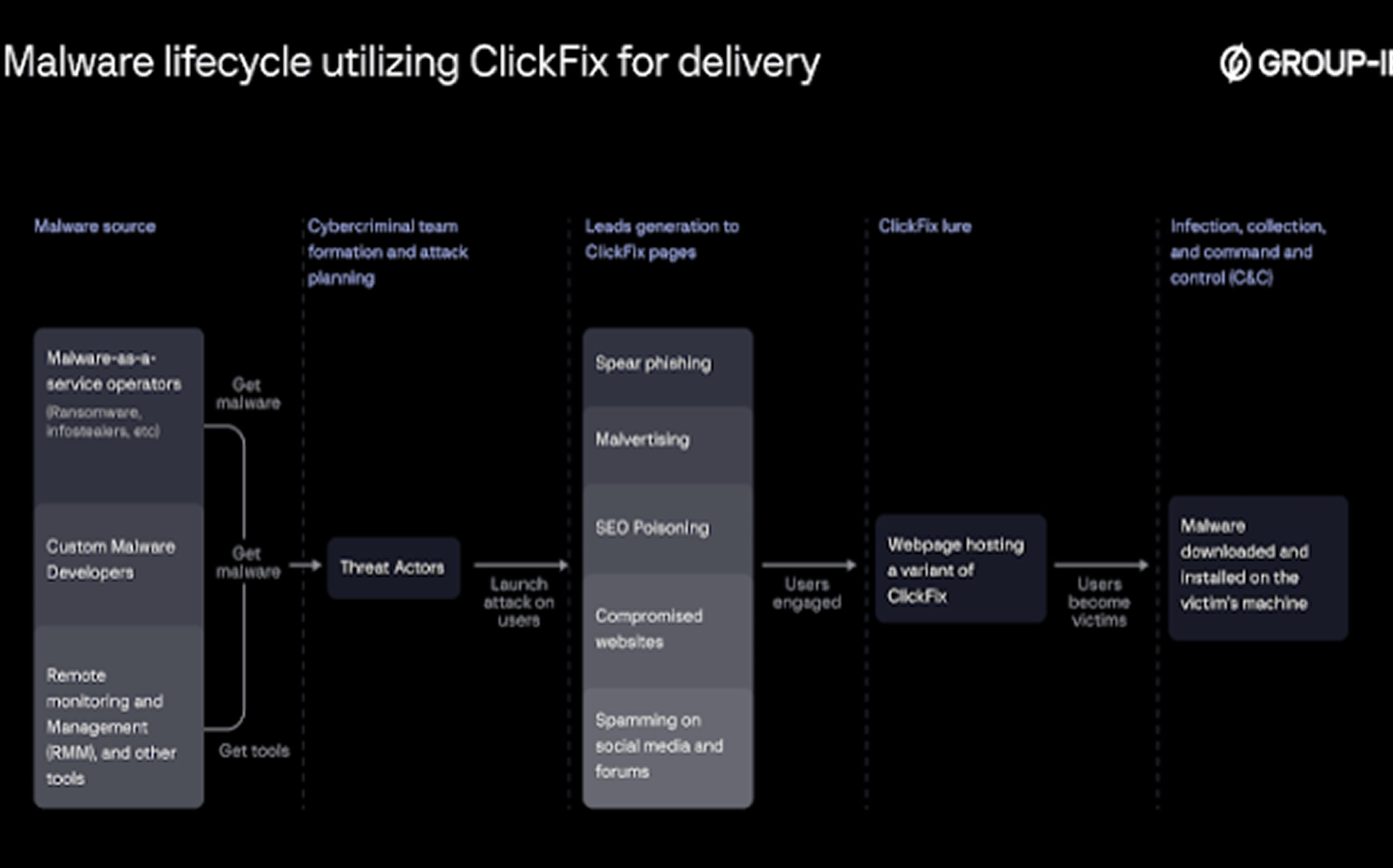
Microsoft previously observed Storm-1865 targeting e-commerce buyers with phishing messages leading to fraudulent payment pages. The use of ClickFix represents a strategic shift designed to evade traditional phishing defenses.
Cybersecurity firm Group-IB has highlighted the increasing adoption of ClickFix, even by advanced threat groups like Russia’s APT28 and Iran’s MuddyWater. Attackers exploit human behavior by presenting a “solution” to a fake problem, shifting execution responsibility onto the user and bypassing automated security measures.
Other recent ClickFix-based campaigns include:
- Fake CAPTCHA prompts leading to PowerShell execution of malware like Lumma and Vidar.
- Fraudulent Google reCAPTCHA challenges used by threat actor Blind Eagle.
- Fake booking confirmations redirecting users to malicious CAPTCHA pages.
- Fake Windows-themed websites designed to distribute Lumma Stealer.
Additionally, cybersecurity firm Trend Micro discovered attackers using AI-related GitHub repositories to spread Lumma Stealer via a loader called SmartLoader. These repositories masquerade as gaming cheats, cracked software, and cryptocurrency tools, enticing victims to download ZIP files containing malware.
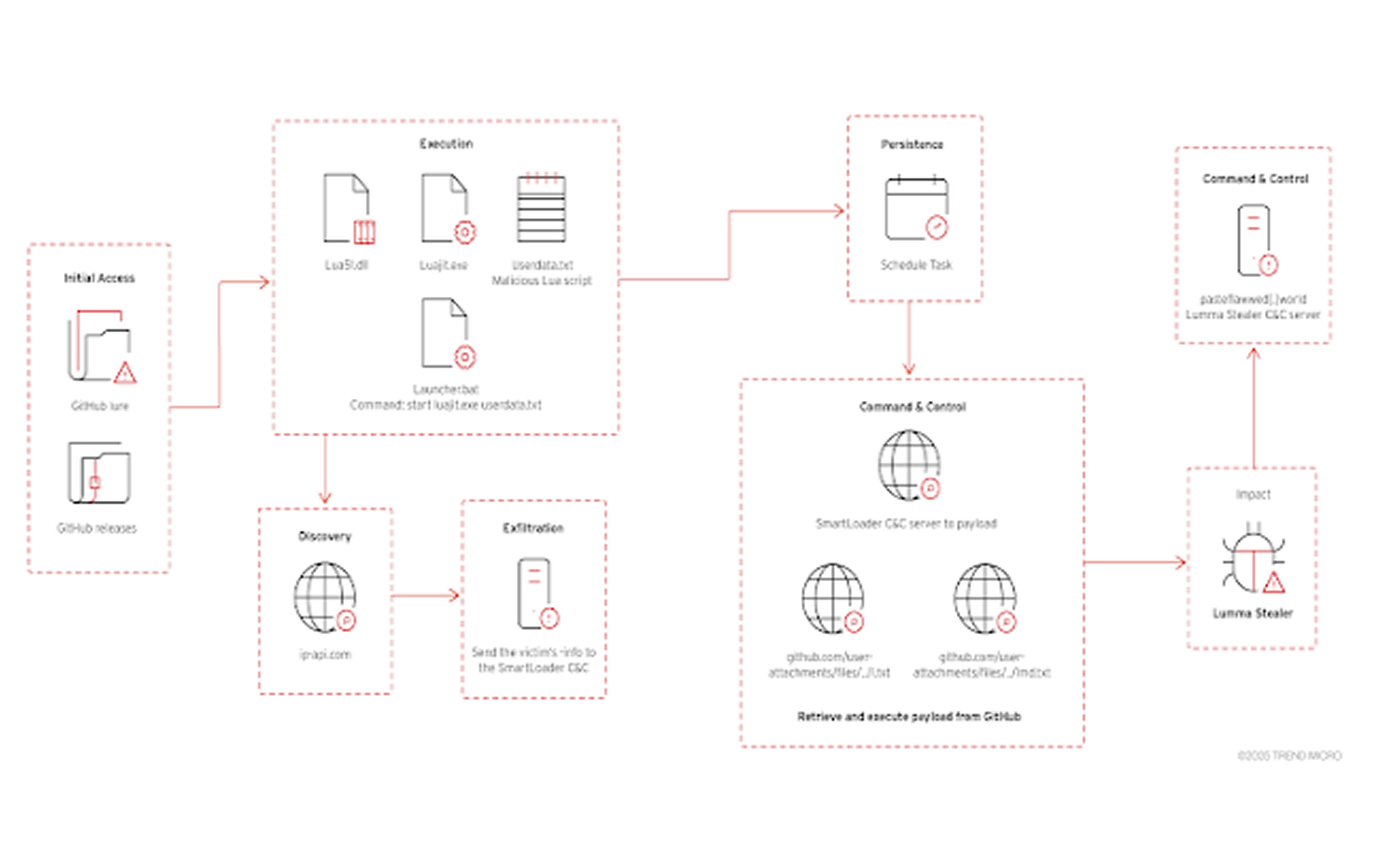
The findings underscore how cybercriminals exploit trusted platforms like GitHub and Booking.com for malware distribution. Meanwhile, Trustwave has detailed a separate phishing campaign using invoice-related decoys to spread StrelaStealer malware, employing custom obfuscation techniques to evade detection.
The growing use of ClickFix highlights the evolution of phishing tactics, emphasizing the need for heightened security awareness and proactive defenses.

![Microsoft Alerts Hospitality Sector to ClickFix Phishing Campaign Using Fake Booking[.]com Emails](/images/2025/03/13/hospital_large.jpg)
