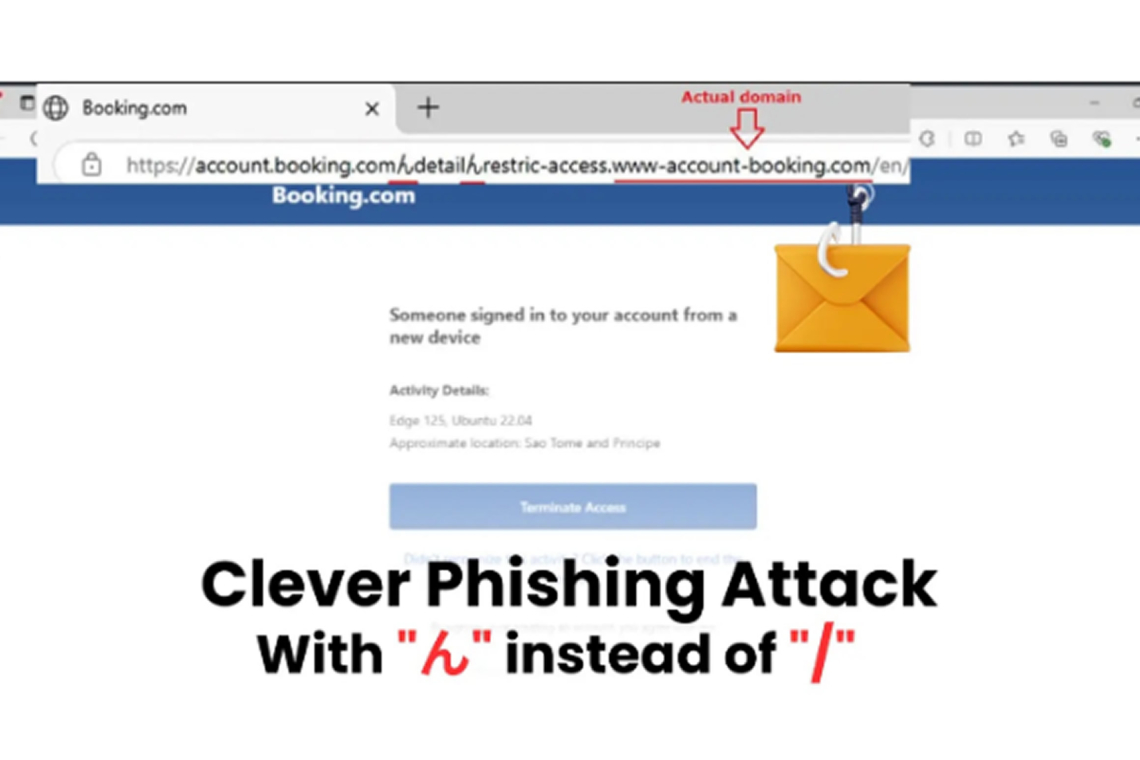
Security researchers have discovered a sophisticated phishing campaign that uses the Japanese character "ん" to create deceptive URLs that look like real website addresses.
The attack, identified by security researcher JAMESWT, targets customers of Booking.com. It exploits the visual similarity between the Japanese character "ん" (Unicode U+3093) and the forward slash "/" in some fonts. When viewed in a browser, a URL containing this character can appear identical to a legitimate one.
The phishing emails use URLs that seem to be valid Booking.com addresses. When a user clicks the link, they are redirected to a malicious site that downloads malware, such as information stealers and remote access trojans. This technique is an example of a homograph attack, where cybercriminals use visually similar characters to trick users.
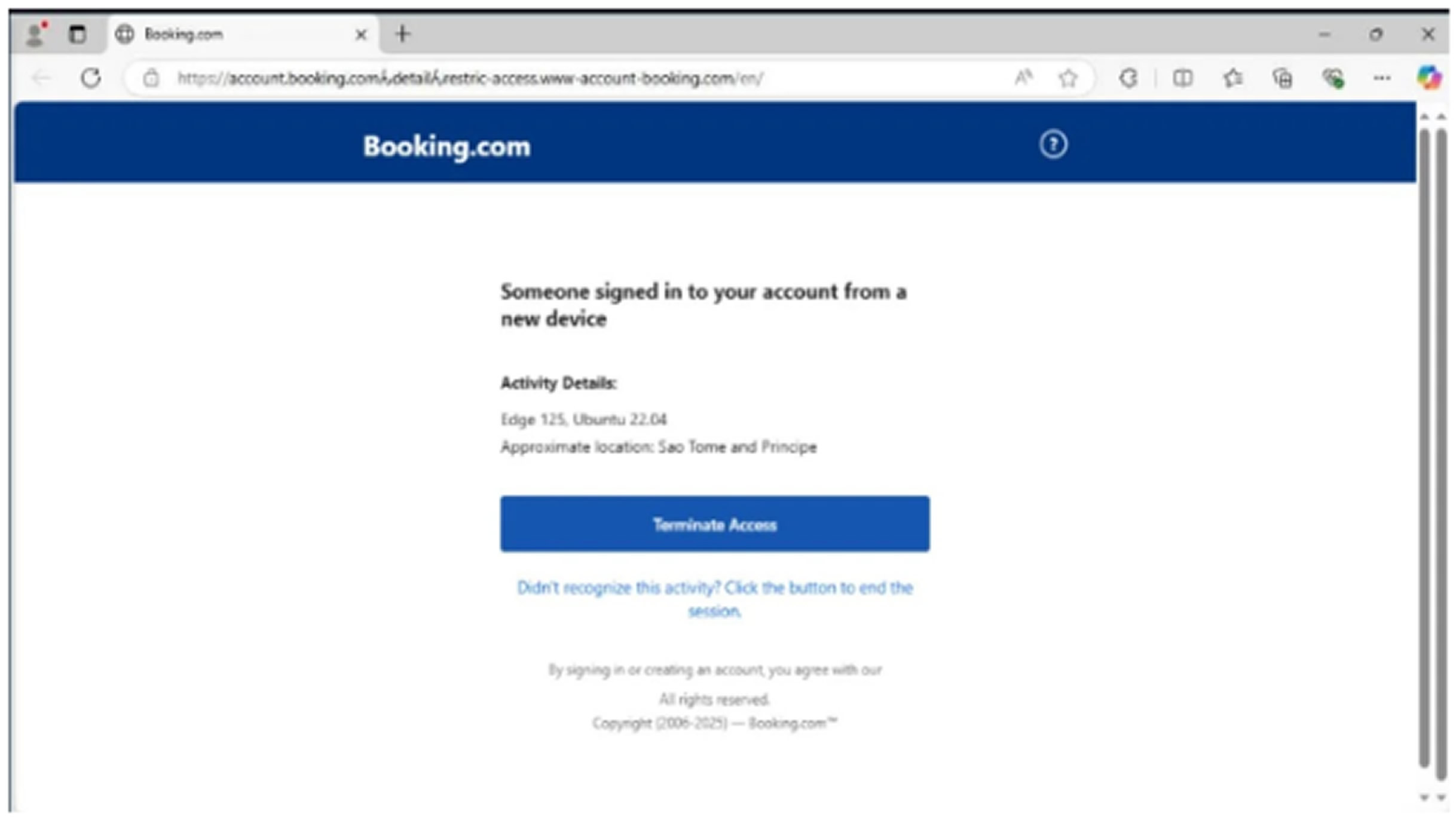
According to a 2025 report, these types of attacks are becoming more sophisticated to bypass email filters and security tools. The use of the "ん" character is particularly effective because it looks like a standard slash while evading many existing detection systems.
Experts recommend that users hover over links before clicking to see the true destination. They also stress that relying on visual URL inspection alone is no longer foolproof. The best defense is a combination of updated security software, email filtering, and user education about these evolving threats. This campaign demonstrates how cybercriminals are adapting to exploit even the smallest visual ambiguities in digital communication.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.