In 2024, there were big changes in the world of ransomware. Cryptocurrency is still a key part of how attackers demand money, but the overall amount of ransom payments dropped by about 35%. This is due to more actions by law enforcement, better cooperation between countries, and more victims refusing to pay.
Because of this, attackers changed their methods. New types of ransomware appeared, often using code that was rebranded, leaked, or bought. Ransomware attacks are now happening faster, with negotiations starting just hours after data is stolen. The attackers vary, from government-backed groups to those running ransomware-as-a-service (RaaS), individual hackers, and groups that steal and extort data, like the one behind the Snowflake breach.
In this chapter, we’ll dive into these changes and look at different examples, like LockBit, Iranian ransomware, Akira/Fog, and INC/Lynx, to show the key trends of the year.
Ransomware activity shifts halfway through the year
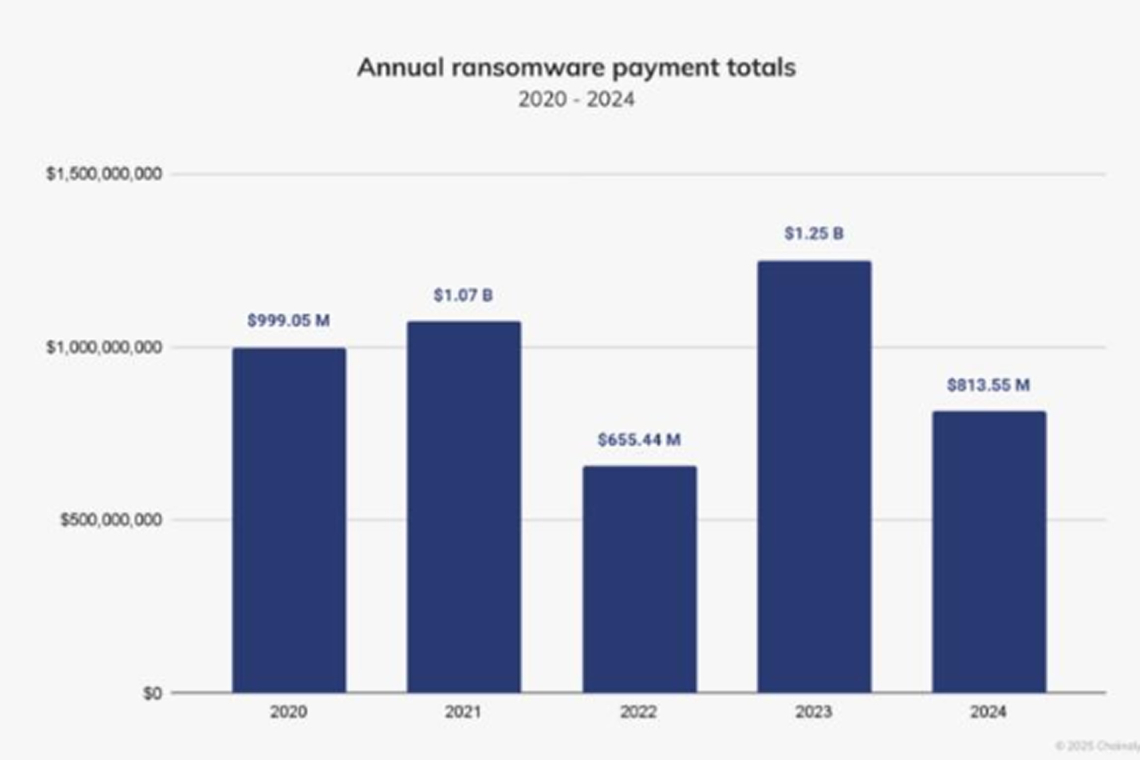
In 2024, ransomware attackers collected about $813.55 million in payments, which is a 35% drop compared to the record $1.25 billion they received in 2023. This marks the first decline in ransomware revenue since 2022.
As mentioned in the mid-year crime update, between January and June 2024, attackers extorted $459.8 million, which was about 2.38% more than the same period in 2023. During this time, there were also a few very large payments, including a $75 million payment to the Dark Angels group.
While the first half of 2024 showed a slight increase in extorted funds, we initially thought that 2024 would end up surpassing 2023’s total. However, after July 2024, ransom payments slowed down by around 34.9%. This slowdown is similar to what we’ve seen in previous years, particularly since 2021, and is even more noticeable than the decline in crypto-related crimes, like stolen funds, in the second half of 2024.
Looking closely at the top 10 ransomware strains based on first-half (H1) revenue, we can see important trends in the groups driving the changes. As shown in the chart, Akira, which has targeted over 250 entities since March 2023, is the only top 10 strain that increased its activity in the second half (H2) of 2024. In contrast, LockBit, which was disrupted by the UK’s National Crime Agency (NCA) and the U.S. FBI early in 2024, saw a sharp 79% drop in H2 payments, showing the success of international law enforcement collaboration. ALPHV/BlackCat, which had been one of the top earners in 2023, exit scammed in January 2024, leaving a gap in H2.
Lizzie Cookson, Senior Director of Incident Response at Coveware, explained that the ransomware landscape never fully returned to normal after the shutdown of LockBit and BlackCat/ALPHV. While there was a rise in lone operators, no group quickly took over the market share left behind. Instead, new smaller players emerged, often targeting small to mid-sized businesses with more modest ransom demands.
Looking deeper into the drop in ransomware payments in H2 2024, data leak sites provide useful insight, possibly indicating more ransomware incidents without matching payments. The number of ransomware events increased in H2, but on-chain payments declined, meaning more victims were targeted but fewer paid. In 2024, data leak sites listed more victims than ever before, and 56 new sites were added, double the number found in 2023. However, not all leaks are genuine. Corsin Camichel from eCrime explained that some leaks falsely claim to affect large organizations when only smaller subsidiaries were hit. There were also instances of old victim data being reposted, such as with LockBit, which reposted past claims to appear more active after facing law enforcement action.
Liska also highlighted how some data leak sites feature illegitimate victims, particularly LockBit, which, after facing law enforcement disruption, posted up to 68% repeat or completely fabricated victim data on its leak site to stay relevant within the underground community.
After the disruptions to LockBit and the exit scam by BlackCat, an interesting shift occurred with the rise of RansomHub RaaS. This group absorbed many of the operators who had been part of LockBit and BlackCat. RansomHub, which started in February 2024, posted the most victim data of any group in 2024, and despite being a newcomer, it quickly made it into the top 10 strains of the year based on on-chain data.
Incident response data also showed a growing gap between ransom demands and the amount actually paid. In the second half of 2024, the difference was significant — about 53% more was being demanded than what was actually paid, further indicating that fewer victims were paying up.
Incident response firms report that most victims choose not to pay ransoms, meaning the actual gap between ransom demands and payments is likely even larger than what the numbers show.
Dan Saunders, Director of Incident Response at Kivu Consulting, explained that only about 30% of ransomware negotiations actually result in payments. Victims tend to base their decision on how valuable the compromised data is. Lizzie Cookson added that thanks to improved cyber hygiene and greater overall resilience, more victims are able to resist ransom demands. They often explore different recovery options, such as using decryption tools to reduce the payment or, more commonly, restoring from recent backups, which tends to be faster and cheaper than paying. In most cases, final payments ranged from $150,000 to $250,000, regardless of the original ransom amount.
Looking at the figure below, we can see how ransomware payment distributions have evolved through 2024. In 2020, there was a single peak in ransom payments with a long tail. But by 2024, we observe three distinct clusters of payment amounts. One group, including actors like Phobos, sees average payments of less than $500 to $1,000. Another group has payments around $10,000, while the third group sees payments above $100,000, some even reaching $1 million. We also notice more events with higher payments, indicating that there are now more attacks resulting in ransom demands over $1 million.
This shift aligns with what Cookson observed: smaller groups are focusing on low- and mid-value payments, while a few high-end attacks, with ransoms in the 7- to 8-figure range, are pushing the overall distribution of ransom amounts toward larger sums.