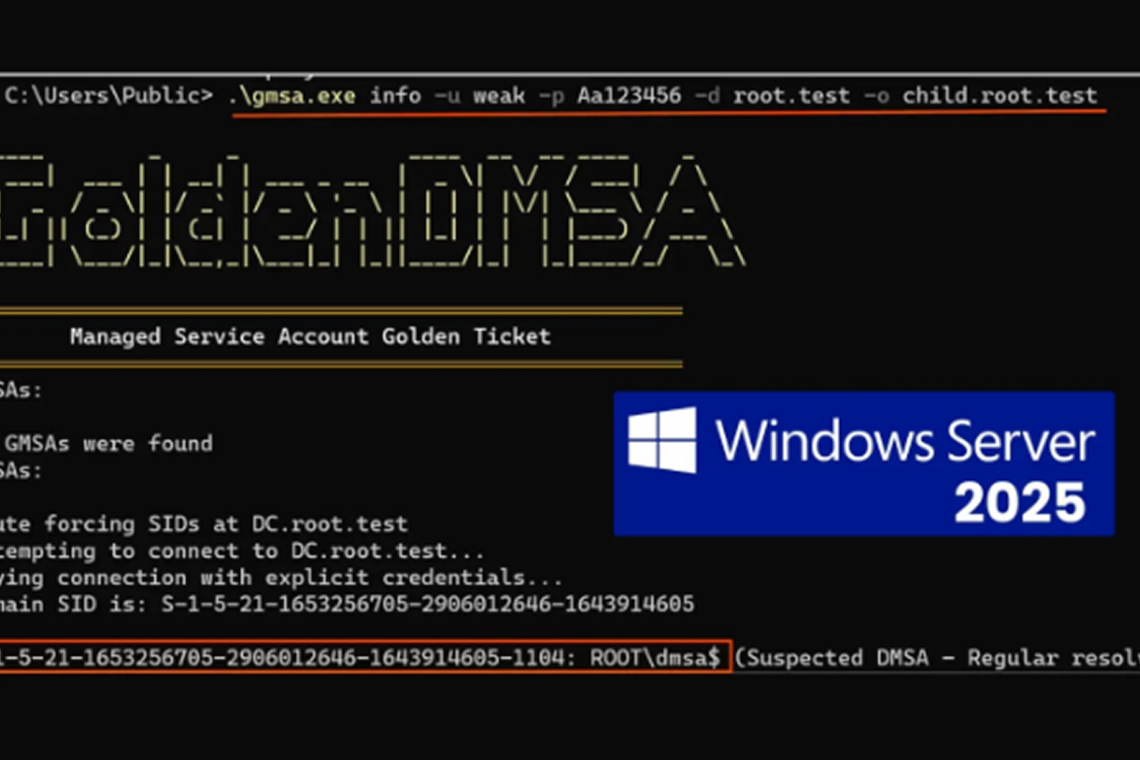
A critical vulnerability in Microsoft’s upcoming Windows Server 2025 allows attackers to bypass authentication controls and generate passwords for all managed service accounts across an enterprise network.
Named “Golden dMSA,” the flaw targets delegated Managed Service Accounts (dMSAs), a new security feature introduced to modernize service account management. The vulnerability reduces what should be strong cryptographic protections to a basic brute-force method requiring just 1,024 attempts.
Adi Malyanker, a researcher at Semperis, discovered the issue while analyzing dMSA architecture. These accounts were designed to eliminate traditional password-based attacks by linking authentication to device identity in Active Directory. Unlike standard service accounts that rely on static credentials, dMSAs aim to avoid common exploits like Kerberoasting.
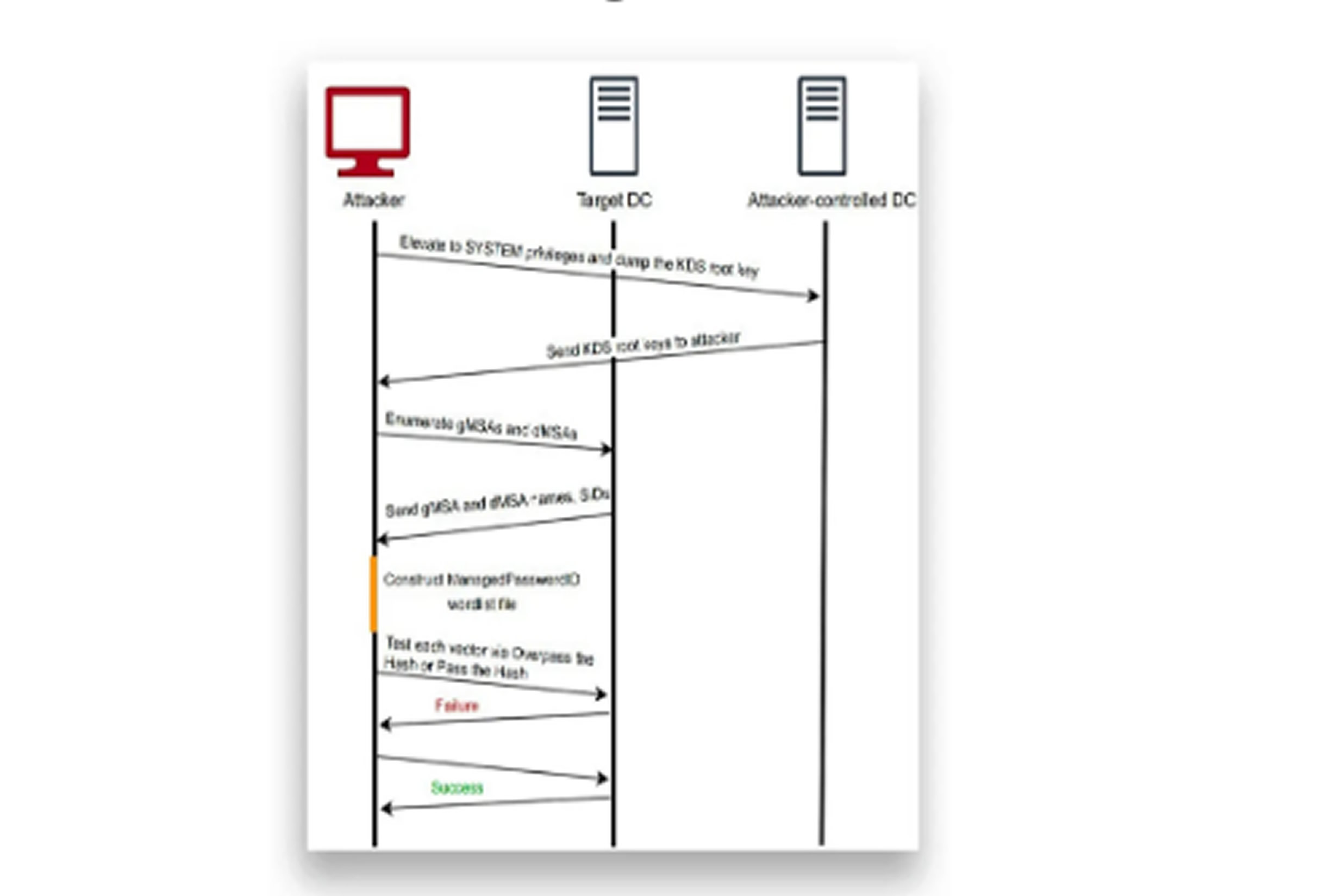
However, the Golden dMSA attack breaks this model by exploiting a flaw in the ManagedPasswordId structure, which includes predictable time-based elements. This allows attackers to guess the correct value in a relatively short amount of time and generate valid passwords.
The attack unfolds in four main stages. First, the attacker extracts the Key Distribution Services (KDS) root key from a compromised domain controller. Next, they scan the Active Directory forest to enumerate dMSA accounts, even bypassing restrictive permissions. In the third phase, they guess the correct ManagedPasswordId values and then use specialized tools to generate valid passwords.
What makes this attack particularly dangerous is its scope. Once the KDS root key is compromised, attackers can generate passwords for every dMSA account across all domains in the forest. Since KDS root keys do not expire, this access can persist indefinitely, even through routine security updates.
Semperis classifies this as a moderate-risk vulnerability because it requires high-level privileges to access the KDS root key, typically limited to Domain Admins, Enterprise Admins, or accounts with SYSTEM-level access. Still, the potential impact is severe. Attackers can evade modern protections like Credential Guard and compromise authentication systems by forging valid credentials without needing machine identity validation.
Detecting such activity is difficult. KDS root key access does not generate security logs by default. Administrators must manually configure System Access Control Lists (SACLs) to monitor access to these sensitive objects. Without these logs, identifying a compromise in real time is nearly impossible.
Microsoft confirmed receiving the vulnerability report on May 27, 2025. In a response dated July 8, the company stated that if an attacker has access to the cryptographic materials used to generate keys, they can authenticate as the associated user. Microsoft clarified that these features are not designed to withstand a full domain controller compromise.
The tool used to demonstrate this vulnerability is publicly available on GitHub. Organizations are encouraged to monitor for abnormal authentication attempts involving service accounts and look out for unusual Kerberos Ticket-Granting Ticket activity, although such indicators may be hard to separate from regular traffic.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.