GitHub Action Compromised, Exposing Secrets from CI/CD Repositories
Cybersecurity researchers have raised concerns over a security breach involving the widely used GitHub Action tj-actions/changed-files, which was tampered with to expose sensitive secrets from repositories utilizing CI/CD workflows.
This action, used in over 23,000 repositories, is designed to track and retrieve modified files and directories. The supply chain attack has been assigned CVE-2025-30066, with a CVSS severity score of 8.6, and is believed to have occurred before March 14, 2025.
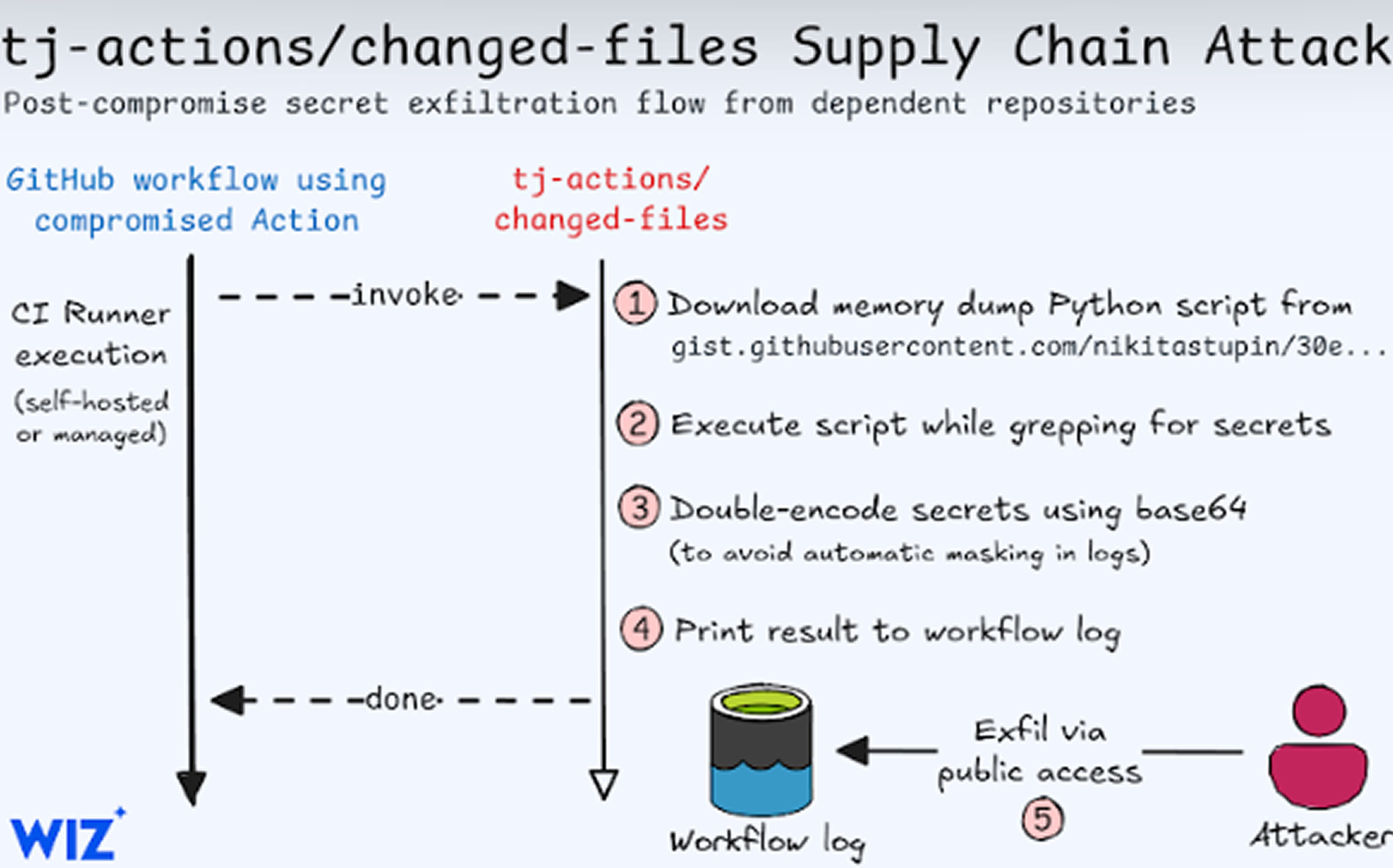
According to StepSecurity, attackers manipulated the action’s code and retroactively updated multiple version tags to reference a malicious commit, causing the action to print CI/CD secrets in GitHub build logs. If these logs were publicly accessible, sensitive credentials—including AWS access keys, GitHub Personal Access Tokens (PATs), npm tokens, and private RSA keys—could have been exposed. However, no evidence suggests the stolen secrets were transferred to an attacker-controlled server.
The attack involved injecting code that executed a Python script hosted on a GitHub Gist, extracting secrets from the Runner Worker process. The malicious script stemmed from an unverified source code commit, but the associated GitHub Gist has since been removed.
Dimitri Stiliadis, CTO of Endor Labs, emphasized that tj-actions/changed-files plays a key role in software development pipelines by detecting file modifications between commits, branches, or pull requests. The compromise affected thousands of CI pipelines, as the modified action secretly executed the script to extract secrets.
The attackers managed to breach a GitHub Personal Access Token (PAT) linked to @tj-actions-bot, a bot with privileged access to the compromised repository. In response, project maintainers have:
- Updated the account’s password
- Implemented passkey authentication
- Restricted permissions based on the principle of least privilege
- Revoked the compromised PAT
To prevent future attacks, the maintainers have confirmed that no PATs will be used for any project within the tj-actions organization going forward.
Users of tj-actions/changed-files are strongly advised to update to the latest version (46.0.1) immediately. Additionally, all workflows executed between March 14 and March 15 should be reviewed for unexpected output in the changed-files section.
This is not the first time tj-actions/changed-files has faced security scrutiny. In January 2024, researcher Adnan Khan identified a critical vulnerability (CVE-2023-49291, CVSS score: 9.8) that could allow arbitrary code execution.
This incident further highlights the security risks associated with open-source software, as supply chain attacks can impact multiple downstream users simultaneously.
As of March 15, 2025, all versions of tj-actions/changed-files were compromised, as attackers altered existing version tags to reference the malicious code. However, organizations using a hash-pinned version remained unaffected—unless they updated to an infected hash during the attack window, according to cloud security firm Wiz.
This event serves as another reminder of the vulnerabilities in open-source ecosystems, reinforcing the need for vigilant security practices and continuous monitoring to mitigate such threats.


