Proton has introduced Proton Authenticator, a free standalone two-factor authentication (2FA) app available on Windows, macOS, Linux, Android, and iOS.
2FA authenticator apps work offline to generate time-based one-time passwords (TOTPs) that refresh every 30 seconds. These codes serve as a second layer of verification during logins, enhancing account security.
Proton, a Swiss tech company known for its privacy-first services like Proton Mail, Proton VPN, Proton Drive, and Proton Pass, now adds this tool to its suite. The new authenticator emphasizes privacy and security, in contrast to many competitors that are closed-source, ad-supported, and rely on proprietary ecosystems.
Proton Authenticator avoids ads, trackers, and vendor lock-in, and does not require a Proton account. According to the launch announcement, it was developed with the same core values as the rest of Proton’s offerings: privacy, transparency, and user-centric security.
Proton aims to bring these principles into the 2FA space by offering a secure, easy-to-use, and encrypted alternative to mainstream options like Google Authenticator, which often tie users to Big Tech ecosystems. While the app is open-source, the company typically releases source code a few weeks after launch, so it is not yet available on GitHub.
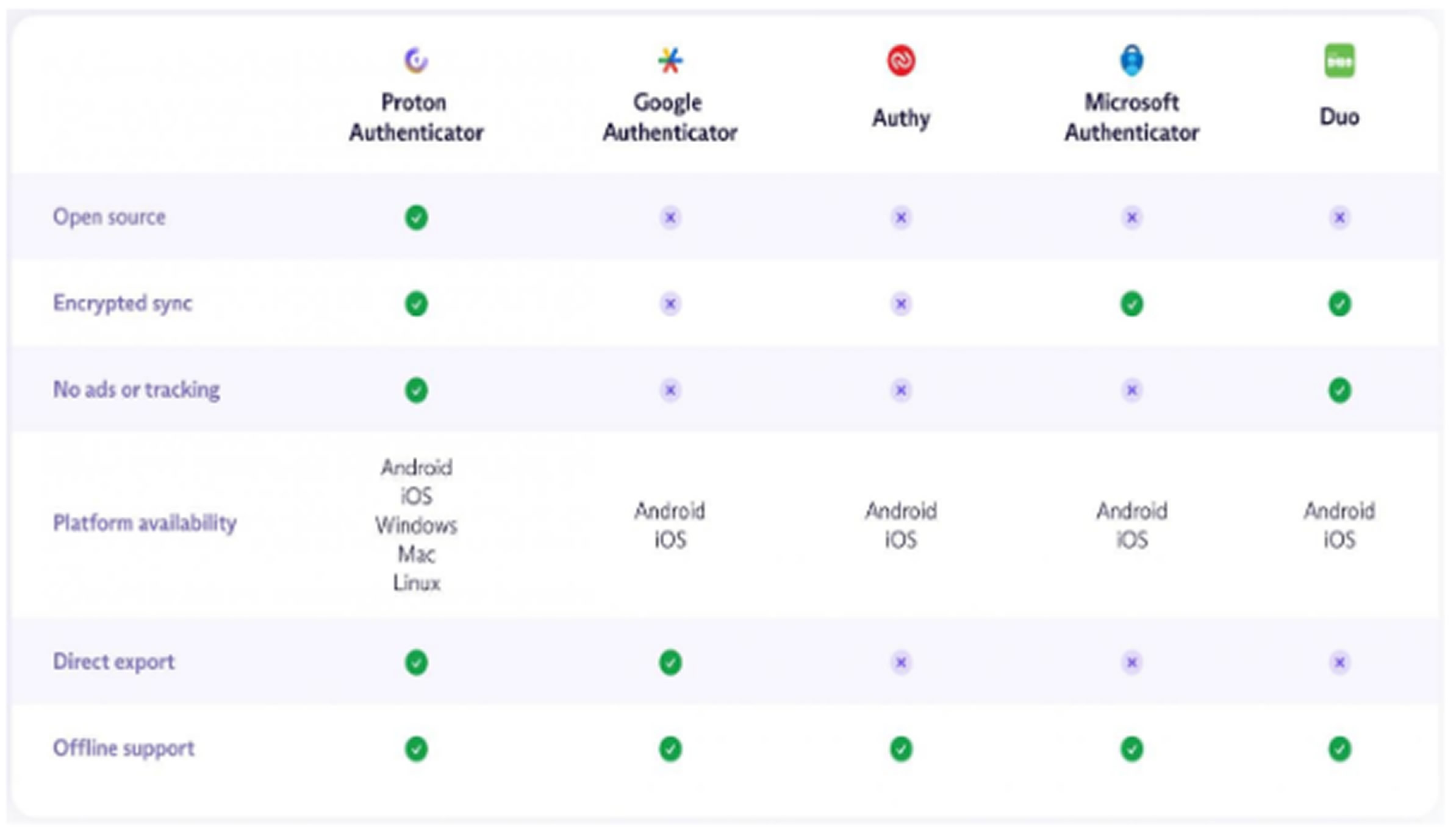
The authenticator supports end-to-end encryption, encrypted backups, and seamless syncing across devices. It also allows users to import and export their TOTP seeds with ease, a feature missing in many popular apps like Microsoft Authenticator and Authy.
Additional features include biometric or PIN-based app locking, which adds an extra layer of protection.
Authenticator apps are much safer than SMS or email-based 2FA methods since they generate codes directly on the device. These time-sensitive codes are short-lived and useless if stolen. The technology also resists phishing, SIM swapping, and man-in-the-middle attacks, as no third party is involved in code delivery.
For those not yet using one, setting up an authenticator app is a highly recommended step for securing any account that supports 2FA.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



