Threat actors are actively abusing LinkedIn posts by posting fraudulent reply comments that impersonate the platform and falsely warn users of policy violations. These messages attempt to pressure users into clicking external links under the pretense of restoring restricted accounts.
The phishing comments closely mimic LinkedIn branding and in some cases leverage the company’s official lnkd.in URL shortener. This tactic makes malicious links more difficult to distinguish from legitimate ones.
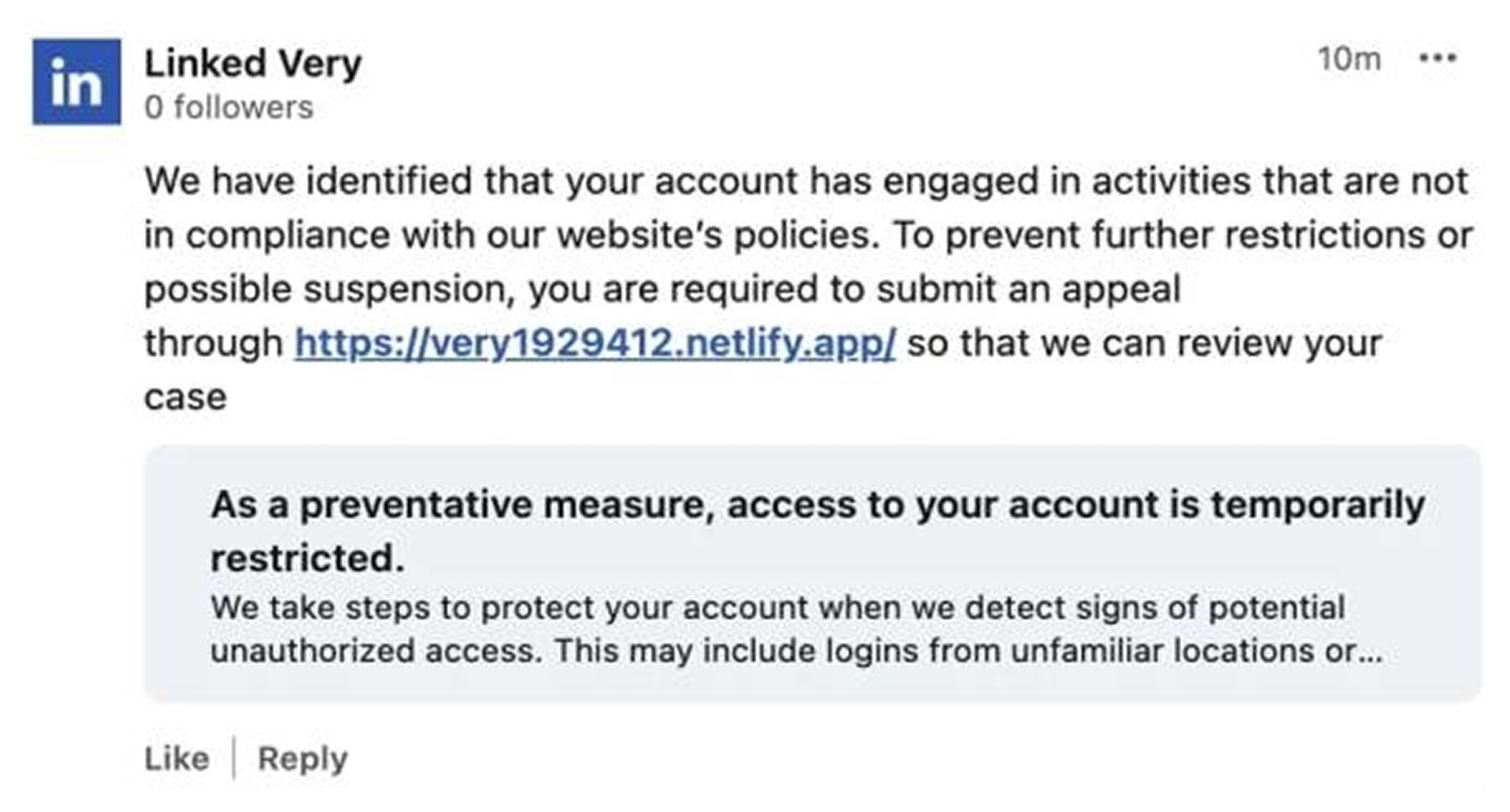
Fake account restriction notices
In recent days, LinkedIn users have reported coordinated activity from multiple LinkedIn-themed profiles commenting on their posts. The messages claim that the user has violated platform policies and that account access has been temporarily restricted until the recipient visits a provided link.
The fraudulent replies display the LinkedIn logo and include language suggesting that suspicious activity was detected on the account. Depending on the device and how comments are viewed, the messages can appear credible. Some link previews reference security-related actions such as detecting logins from unfamiliar locations.
While some phishing links point to unfamiliar domains that may raise suspicion, others conceal the final destination using the lnkd.in shortener. This approach reduces visibility into the true URL and increases the likelihood of user interaction, particularly on mobile devices where previews may be limited.
Several LinkedIn members have publicly shared examples of these deceptive comments. In one observed case, users were redirected to a phishing page that expanded on the false restriction notice and prompted identity verification. Clicking the verification button led to a secondary site where credential harvesting occurred.
Abuse of fake company pages
The campaign also involves the use of fraudulent company pages that display LinkedIn’s logo and variations of its name. Multiple such pages appeared over a short period before being removed. These accounts were used to post phishing replies that appeared to originate from official LinkedIn entities.
LinkedIn has acknowledged awareness of the activity and confirmed that internal teams are taking steps to address the abuse. A company spokesperson stated that LinkedIn does not communicate policy violations through public comments and encouraged users to report suspicious behavior for review.
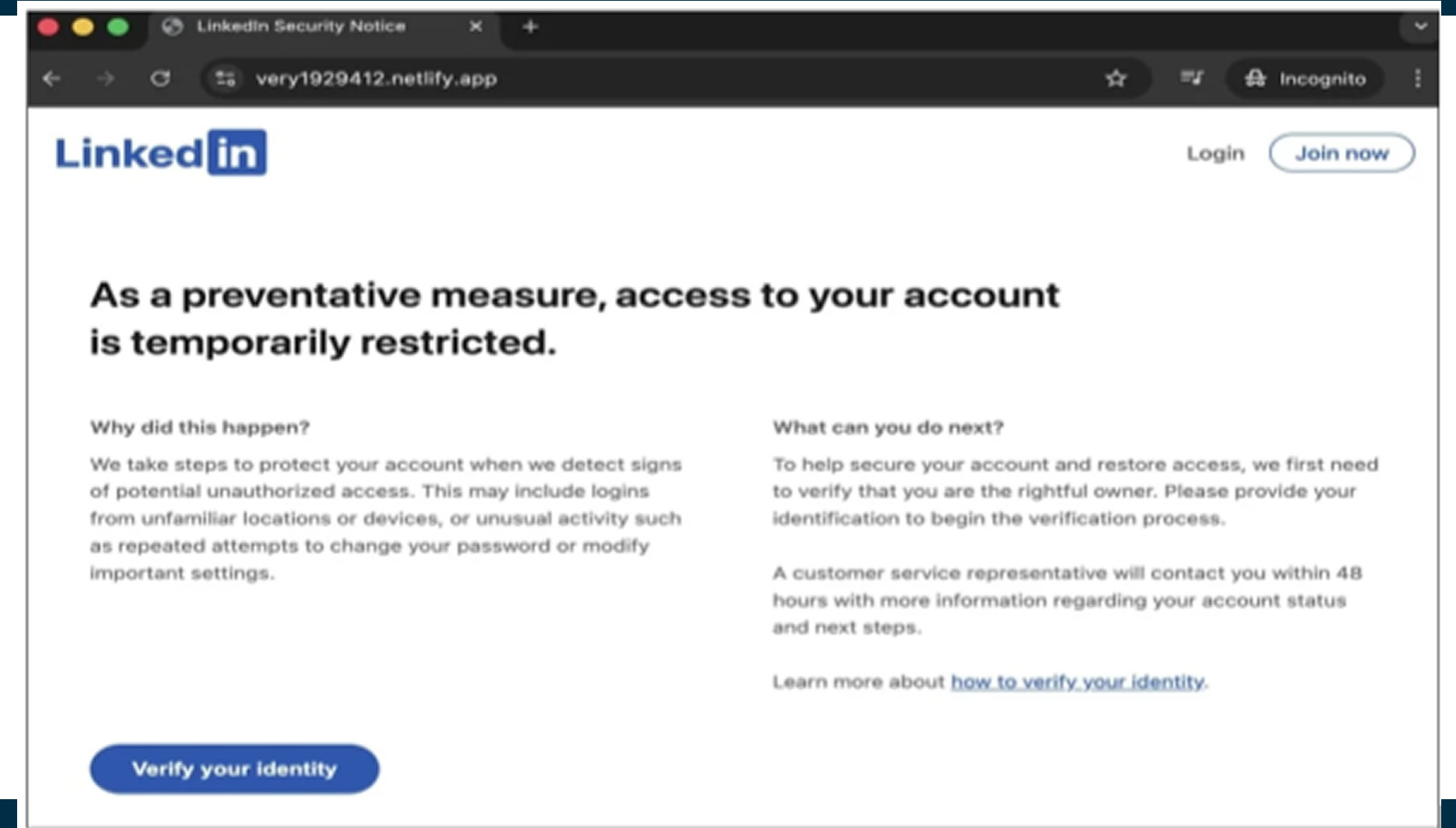
Ongoing risk of impersonation scams
This activity reflects a broader trend of impersonation-based phishing campaigns on social platforms. Similar tactics were previously observed on other networks where attackers posed as legitimate organizations to redirect victims to malicious channels.
Users are advised to remain cautious and avoid engaging with comments, replies, or direct messages that claim to represent LinkedIn and request interaction with external links. Any suspected impersonation should be reported through the platform’s official reporting mechanisms.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



