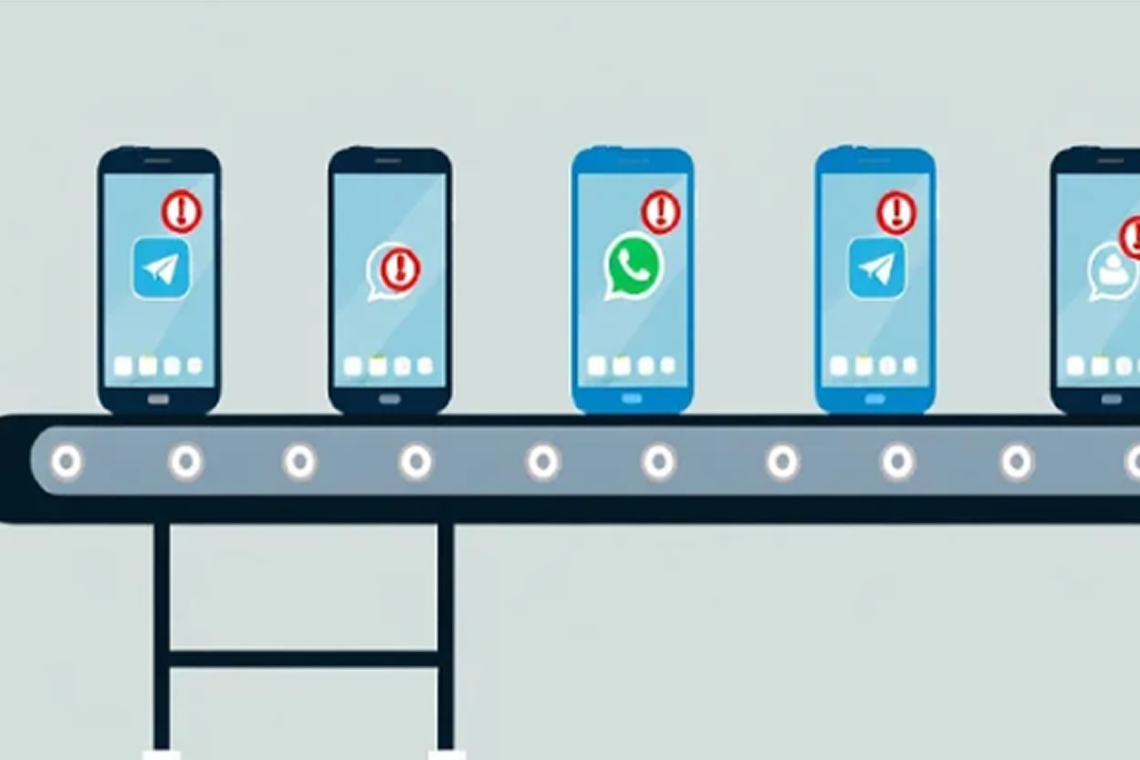
Chinese-Made Budget Smartphones Found with Trojanized WhatsApp and Telegram Apps
A new malware campaign has been discovered involving cheap Android smartphones manufactured by Chinese companies. Since June 2024, these devices have been preloaded with trojanized apps masquerading as popular messaging platforms like WhatsApp and Telegram, which contain functionality designed to steal cryptocurrency via clipper malware.
This approach marks a significant escalation in the use of malicious apps to steal financial information. According to Doctor Web, a Russian antivirus firm, attackers have directly targeted the supply chain of various Chinese manufacturers, loading these devices with malware before they even reach consumers.
How the Attack Works
The malicious apps were found to be pre-installed on low-end smartphones, often models that mimic premium phones from brands like Samsung and Huawei, with names such as S23 Ultra, S24 Ultra, Note 13 Pro, and P70 Ultra. Many of these phones are manufactured by the SHOWJI brand.
The attackers used a technique to spoof the technical specifications of the devices, altering the About Device page and fooling users into believing their phones were running the latest Android 14 version with better hardware.
The malware, known as Shibai, is injected into otherwise legitimate apps using an open-source project called LSPatch. About 40 different apps, including messengers and QR code scanners, are believed to have been modified this way.
The Trojan's Functionality
Once the trojanized apps are installed, they hijack the app update process, retrieving a malicious APK file from a server controlled by the attackers. The malware scans WhatsApp messages for cryptocurrency wallet addresses, specifically targeting patterns associated with Ethereum or Tron wallets. If a match is found, it replaces the victim's wallet address with the attackers' address, effectively rerouting the cryptocurrency transactions.
For outgoing messages, the victim's device shows the correct wallet address, but the recipient sees the fraudster’s address. Similarly, for incoming messages, the victim’s wallet address is swapped with the attackers.
In addition to this, the malware also collects sensitive data such as device information, all WhatsApp messages, and images stored in specific directories (DCIM, Pictures, Documents, Downloads). This includes scanning images for wallet recovery phrases (mnemonic phrases), which allow the attackers to gain unauthorized access to victims' wallets.
Scale of the Attack
The attackers are utilizing over 30 domains to distribute the malicious apps and manage the operation using more than 60 command-and-control servers. Over the past two years, the attackers have received more than $1.6 million through cryptocurrency wallets linked to the campaign, showing that the supply chain compromise has been highly profitable.
New Android Malware Family: Gorilla
In a related development, PRODAFT, a Swiss cybersecurity company, uncovered a new Android malware family named Gorilla. This malware is designed to collect sensitive device information, such as SIM card details, phone numbers, installed apps, and Android version. It maintains persistent access to the infected devices and can receive commands from a remote server.
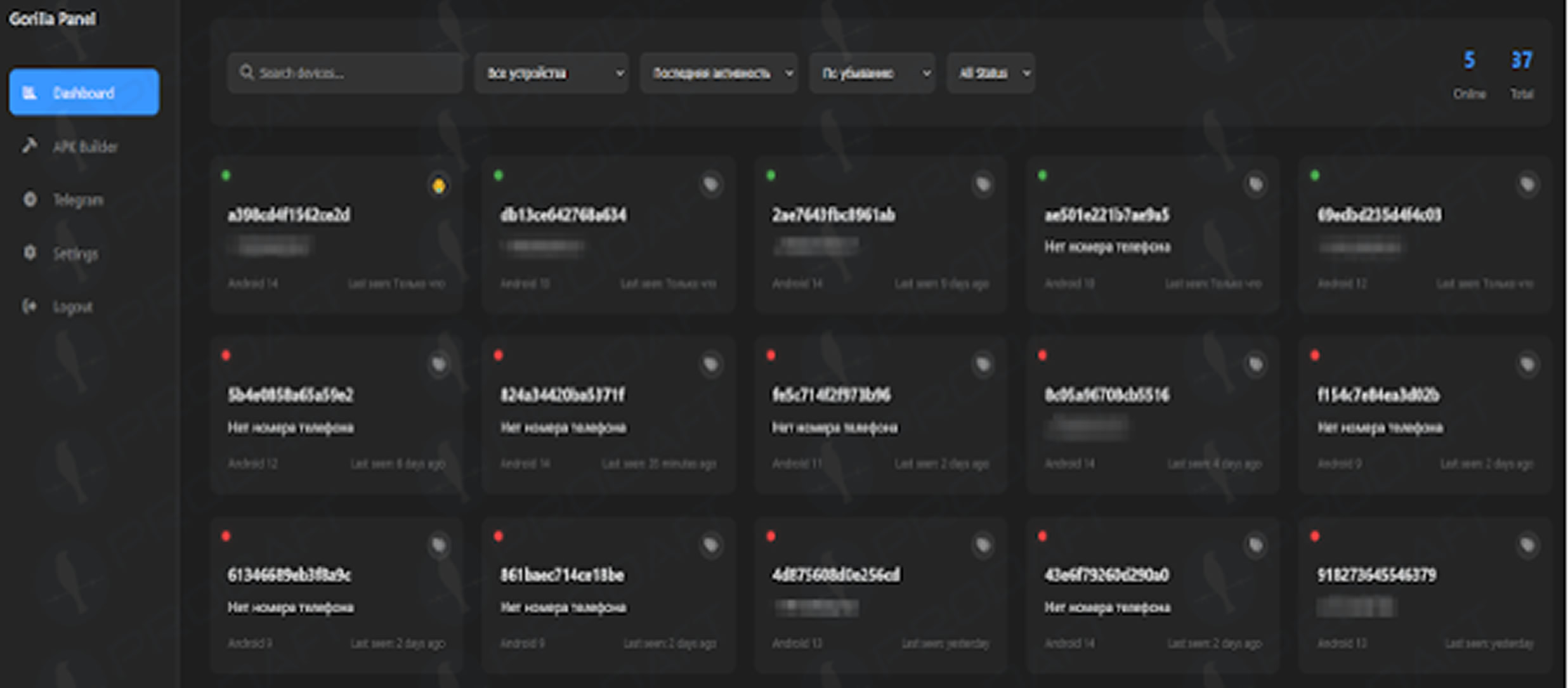
Unlike more sophisticated malware, Gorilla does not use obfuscation techniques, which suggests it may still be in development. Additionally, FakeApp, another trojan found in Android apps distributed via the Google Play Store, has been detected. These apps, which were impersonating popular games and apps, are equipped with the ability to receive external commands and perform malicious actions, such as redirecting users to phishing sites.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.