Cybercriminals Exploit AI-Powered Gamma Platform in Sophisticated Microsoft Phishing Scheme
Threat actors are now abusing Gamma, an AI-driven presentation platform, to carry out phishing attacks that trick users into visiting fake Microsoft login pages, according to researchers at Abnormal Security.
In a detailed analysis released Tuesday, researchers Hinman Baron and Piotr Wojtyla explained how attackers are leveraging Gamma to host deceptive presentations that guide users through multiple redirections, ultimately leading to credential-harvesting pages.
The Attack Chain
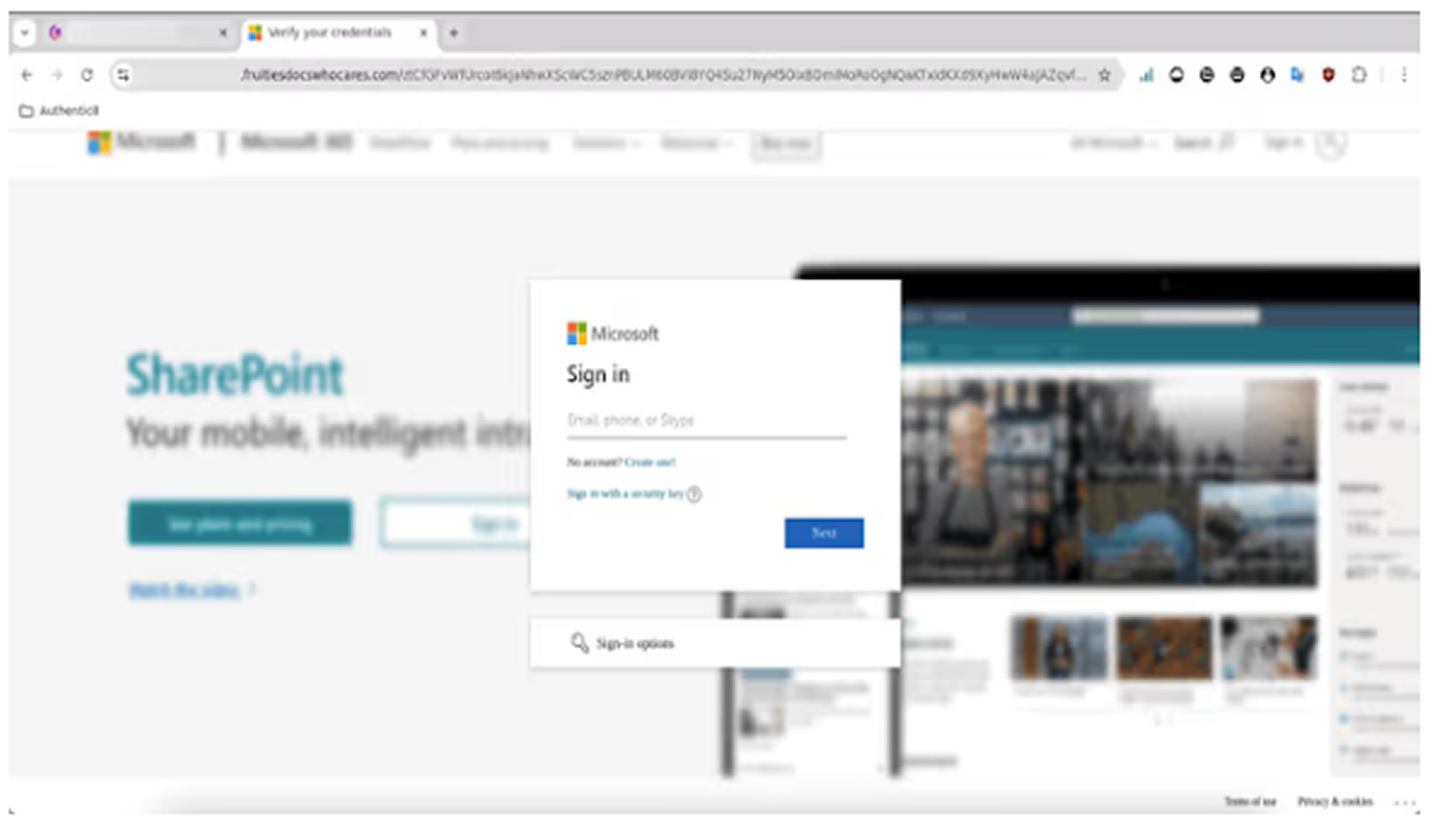
The phishing campaign begins with emails—sometimes sent from legitimate, compromised accounts—containing PDF attachments. These PDFs are actually hyperlinks, redirecting users to a Gamma-hosted presentation that invites them to click a button labeled “Review Secure Documents.”
From there, users are sent to a spoofed Microsoft-branded page that includes a Cloudflare Turnstile CAPTCHA, designed to both build trust and evade detection by automated security tools. Upon completion, the user is directed to a fake Microsoft SharePoint login page intended to steal credentials.
If the user enters incorrect login details, an "Incorrect password" prompt appears, suggesting that attackers are using Adversary-in-the-Middle (AiTM) tactics to verify credentials in real time.
Exploiting Trust to Evade Detection
This campaign is part of a broader trend where cybercriminals exploit legitimate platforms to host malicious content, bypassing traditional email security checks like SPF, DKIM, and DMARC—a tactic known as Living Off Trusted Sites (LOTS).
“Rather than linking directly to phishing pages, attackers cleverly route victims through several layers,” the researchers noted. “Starting with Gamma-hosted presentations, followed by Cloudflare-guarded splash pages, and finally leading to spoofed login portals—this layered redirection conceals the real destination and helps bypass link analysis tools.”
Microsoft’s Broader Warning on AI-Powered Fraud
The disclosure comes alongside Microsoft’s Cyber Signals report, which highlights a rise in AI-powered fraud. Cybercriminals are using AI tools to create deepfakes, cloned voices, phishing emails, fake websites, and even fraudulent job listings, all designed to manipulate users at scale.
“AI allows attackers to collect detailed information on targets, enabling more convincing social engineering lures,” Microsoft stated.
They also described elaborate scams using AI-generated storefronts, complete with fake reviews and brand histories to sell non-existent products.
Evolution of Storm-1811
The threat group known as Storm-1811 (a.k.a. STAC5777) has been observed evolving its tactics. Previously known for abusing Microsoft Quick Assist in voice phishing schemes, the group has shifted to using a stealthy persistence method: TypeLib COM hijacking combined with a new PowerShell backdoor to evade detection and maintain access to breached systems.
According to ReliaQuest, the PowerShell malware was first developed in January 2025, with initial infections spread through malicious Bing ads. The attackers appear to have targeted executives in the finance, scientific, and technical services sectors, particularly those with female-sounding names.
The phishing messages were timed between 2:00 and 3:00 p.m., aligning with the post-lunch hours when employees may be less vigilant.
While it remains unclear if Storm-1811 is still behind the Microsoft Teams-based phishing campaign, analysts agree that this attack vector remains active. Phishing via Teams continues to be a threat as adversaries adopt increasingly clever techniques to bypass defenses and maintain persistence inside organizations.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.


