Hackers recently targeted a U.S.-based chemicals company by exploiting a critical flaw in SAP NetWeaver, identified as CVE-2025-31324, to deploy an advanced version of the Auto-Color Linux malware, according to a report from cybersecurity firm Darktrace.
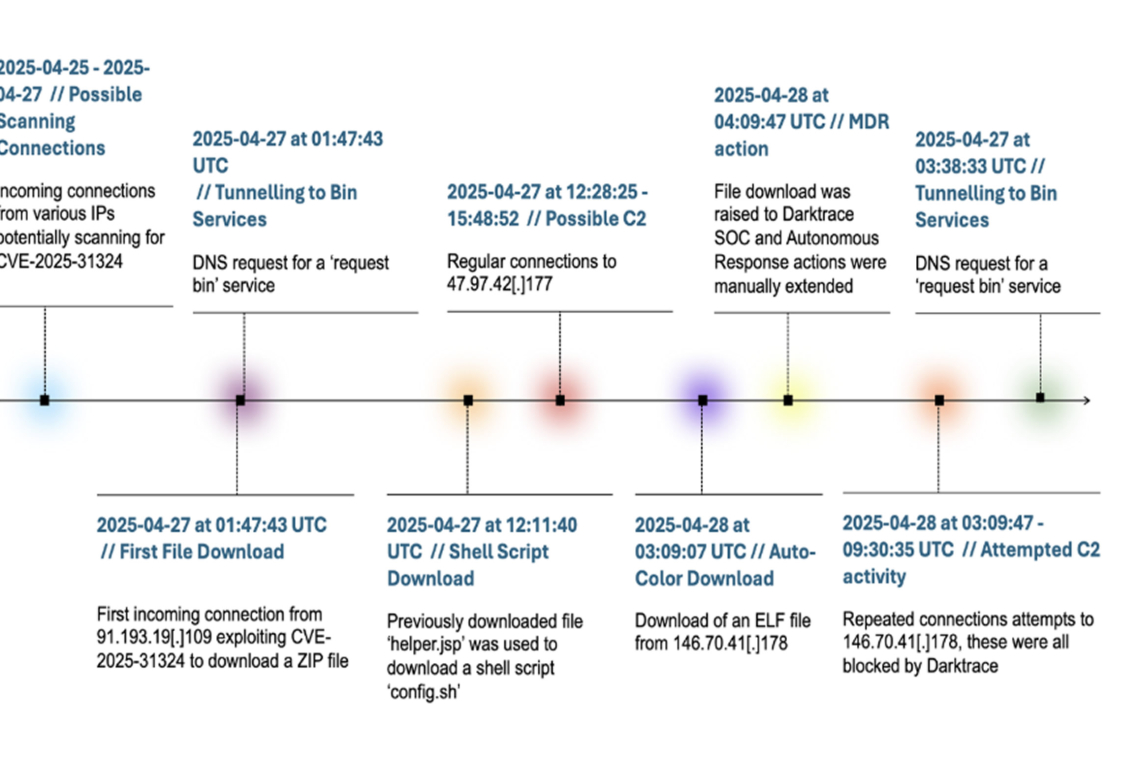
The incident, which occurred in April 2025, began when Darktrace detected unusual activity involving a backdoor malware attack. Over a three-day period, attackers accessed the company’s network, attempted to download suspicious files, and communicated with infrastructure linked to the Auto-Color malware.
The vulnerability in SAP NetWeaver Visual Composer Metadata Uploader allowed unauthenticated attackers to upload and execute malicious files, potentially leading to a full system compromise. Although SAP released a security patch in April 2025, researchers from ReliaQuest warned that the flaw was already being exploited, even on systems that had been patched.
During the attack, Darktrace observed ZIP file downloads, DNS queries to external domains, and a suspicious ELF file. The company’s autonomous defense system intervened, limiting the device's network access while preserving normal functionality. Despite containment efforts, the threat actors managed to download additional malicious tools, including a disguised script and commands that interacted with known cyber-espionage infrastructure.
Within 24 hours, the attackers deployed the Auto-Color malware, hiding it in a fake log file. The malware, especially dangerous when executed with root privileges, installs a covert system library for persistence and attempts to connect to a command-and-control server for instructions.
Darktrace's rapid response prevented the malware from activating fully. The defense measures were extended for 24 more hours, allowing the security team to assess and neutralize the threat. Auto-Color remained mostly inactive without a live connection to its server, highlighting its design to evade detection in restricted environments.
First observed in 2024, Auto-Color has targeted universities and government institutions across the U.S. and Asia. It leverages SAP vulnerabilities, uses system features like ld.so.preload for persistence, and hides in directories such as /var/log/cross/auto-color. The malware also supports functions like command execution, traffic proxying, and reverse shell access, while including a rootkit to stay undetected.
Darktrace concluded that the malware demonstrates a deep knowledge of Linux systems and employs advanced evasion strategies to avoid exposure when its operations are disrupted.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.