The financially motivated threat group UNC2891 has been found targeting ATM infrastructure using a 4G-enabled Raspberry Pi in a stealth cyber-physical operation.
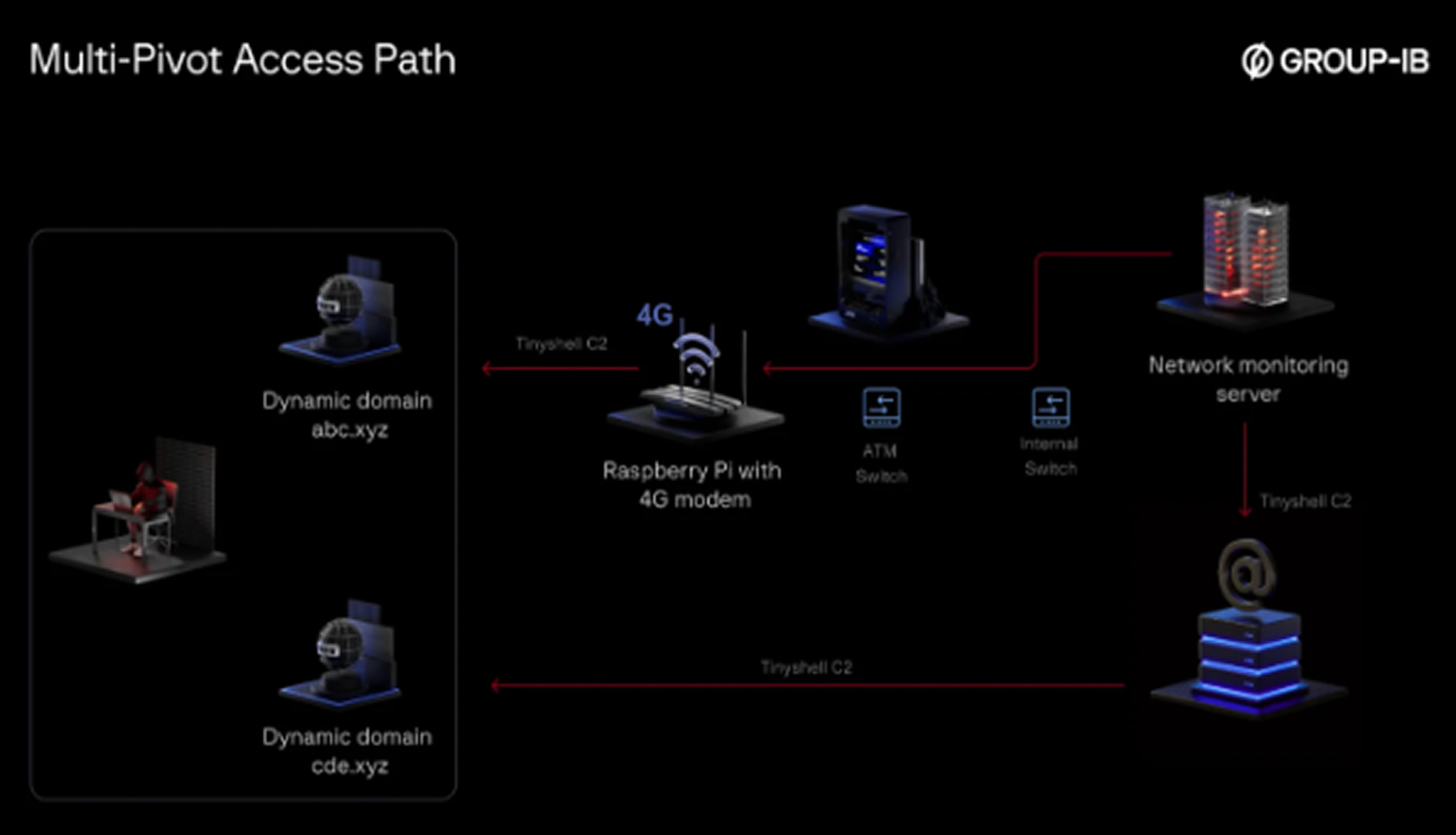
According to Group-IB, the attackers exploited physical access to install the Raspberry Pi, connecting it to the same network switch as the ATM, effectively placing it inside the bank's internal network. The method used to gain this physical access remains unknown.
Security researcher Nam Le Phuong explained in a report that the Raspberry Pi was fitted with a 4G modem, which allowed remote access via mobile data. The attackers used the TINYSHELL backdoor to establish an outbound command-and-control (C2) connection through a Dynamic DNS domain. This tactic allowed persistent remote access, bypassing firewalls and standard network defenses.
First profiled by Mandiant in March 2022, UNC2891 has been linked to ATM switching network attacks that enable unauthorized cash withdrawals using fraudulent cards. A key component of these attacks is a kernel module rootkit called CAKETAP. This tool hides connections, processes, and files, while spoofing card and PIN verification messages from hardware security modules (HSMs), enabling financial fraud.
There are tactical similarities between UNC2891 and another group known as UNC1945 or LightBasin, previously tied to breaches in managed service providers and organizations in finance and consulting.
Group-IB found that UNC2891 demonstrated strong knowledge of Linux and Unix systems. On the victim’s network monitoring server, researchers uncovered backdoors named "lightdm" designed to create active links with both the Raspberry Pi and the internal mail server. The attackers used bind mounts to conceal the backdoor from process listings, helping evade detection.
The attack aimed to deploy the CAKETAP rootkit on the ATM switching server to execute fraudulent cash withdrawals. However, the operation was intercepted before any major damage occurred.
Even after the Raspberry Pi was discovered and removed, the attacker retained internal access through a backdoor on the mail server, using a Dynamic DNS domain for ongoing command-and-control communication.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



