Cybercriminals are increasingly leveraging a tool called Atlantis AIO Multi-Checker to automate credential stuffing attacks
according to research from Abnormal Security. This tool has become a significant asset in the cybercriminal ecosystem, enabling attackers to test millions of stolen credentials rapidly.
Credential stuffing is a cyber attack method where hackers use lists of stolen usernames and passwords to gain unauthorized access to user accounts across various platforms. These credentials are often obtained from data breaches or sold on underground forums. Unlike brute-force attacks, which attempt to guess passwords through trial and error, credential stuffing relies on previously compromised login details.
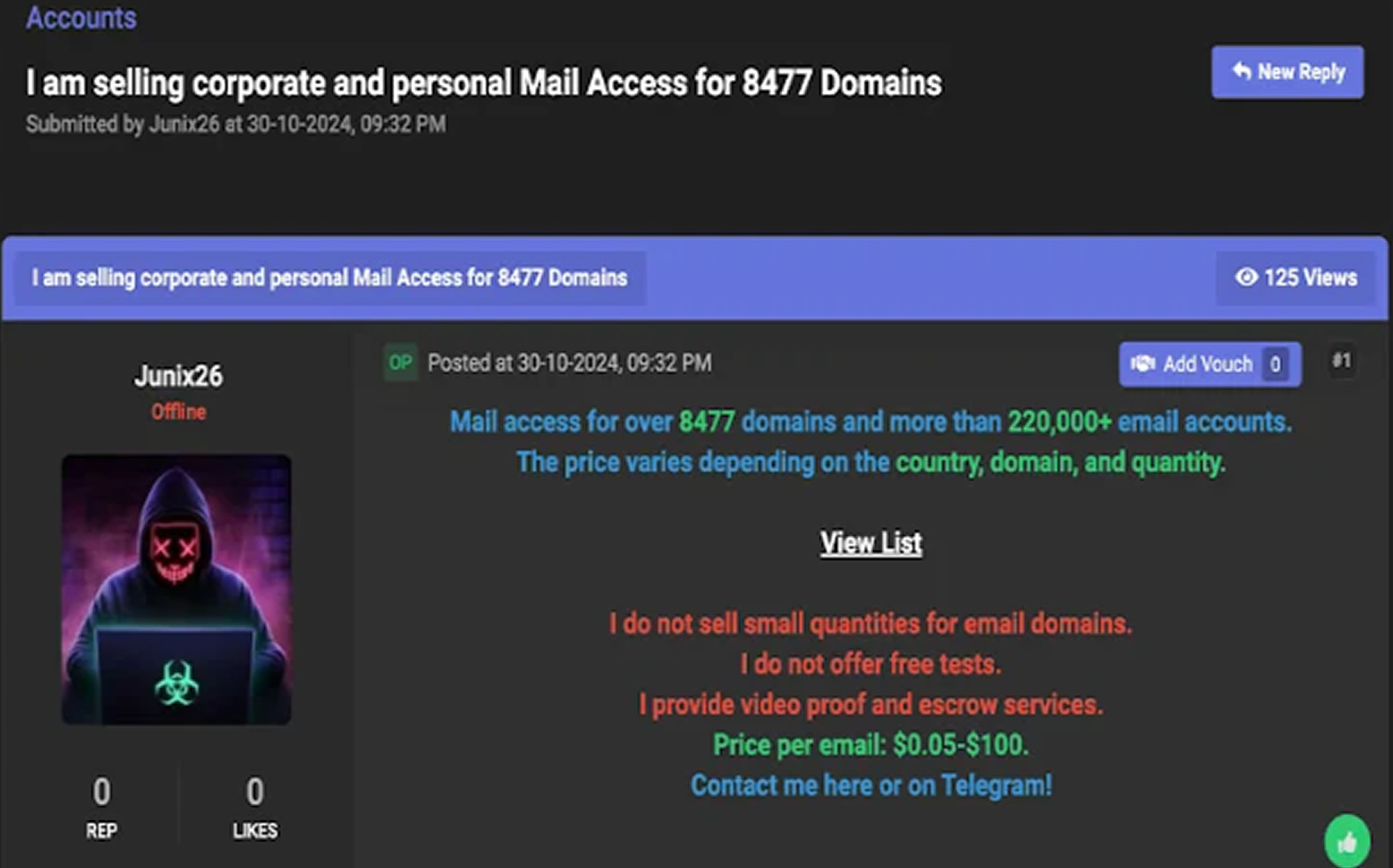
Abnormal Security's analysis reveals that Atlantis AIO is designed to launch large-scale credential stuffing attacks using pre-configured modules targeting multiple platforms and cloud services. This allows cybercriminals to commit fraud, steal data, and take over accounts efficiently. The tool's creators claim it is built on a "foundation of proven success," boasting thousands of satisfied users while offering security measures to keep purchases anonymous.
The targets of Atlantis AIO include major email providers like Hotmail, Yahoo, AOL, GMX, and Web.de, as well as e-commerce platforms, streaming services, VPNs, financial institutions, and food delivery services. Additionally, the tool is capable of brute-force attacks on email platforms and automates account recovery processes for services like eBay and Yahoo.
According to Abnormal Security, tools like Atlantis AIO provide cybercriminals with a direct path to monetizing stolen credentials. Attackers can sell compromised login details on dark web marketplaces, commit fraud, or use hijacked accounts to distribute spam and phishing campaigns.
To reduce the risk of account takeovers, organizations and users should enforce strong password policies and implement phishing-resistant multi-factor authentication (MFA) to safeguard against these automated attacks.
Found this article interesting? Follow us on X(Twitter) and FaceBook to read more exclusive content we post.


