IOCONTROL Malware Poses Major Threat to OT and IoT Systems, Targeting Fuel Infrastructure
A newly discovered malware strain, dubbed "IOCONTROL," has emerged as a significant cyber threat, specifically targeting operational technology (OT) and Internet of Things (IoT) systems. The malware has been observed infiltrating fuel-management infrastructure in both the United States and Israel.
First detected in December 2024, IOCONTROL has been linked to the pro-Iranian hacktivist group Cyber Av3ngers, which has a history of launching cyberattacks against Israeli entities.
Attack Methodology and Impact
The initial wave of attacks was facilitated by compromised credentials, reflecting a 33% year-over-year increase in credential theft. By leveraging stolen login information, attackers gained persistent remote access to critical systems, enabling them to manipulate industrial processes and steal sensitive operational data.
Cybersecurity analysts at Flashpoint identified IOCONTROL’s modular architecture, which includes:
- UPX-packed binaries for obfuscation
- Encrypted command-and-control (C2) communications for stealth
- Surveillance functionalities designed for low-resource IoT environments
The malware exploits internet-exposed industrial control systems (ICS), taking advantage of vulnerabilities within these systems. It also utilizes the MQTT protocol, a lightweight messaging standard commonly used in IoT networks, to evade traditional network monitoring solutions.
Geopolitical and Infrastructure Risks
IOCONTROL’s deployment in attacks on fuel distribution networks underscores growing cybersecurity risks to critical infrastructure, especially amid escalating geopolitical tensions in the Middle East.
Technical Details and Evasion Techniques
To avoid detection, IOCONTROL employs advanced evasion mechanisms, including:
- A modified UPX packer that alters binary magic values to resist static analysis
- Techniques designed to bypass conventional security tools
Given the severity of the threat, organizations managing OT and IoT systems—particularly within fuel and energy sectors—are urged to strengthen access controls, implement robust network monitoring, and apply security patches to mitigate potential risks.
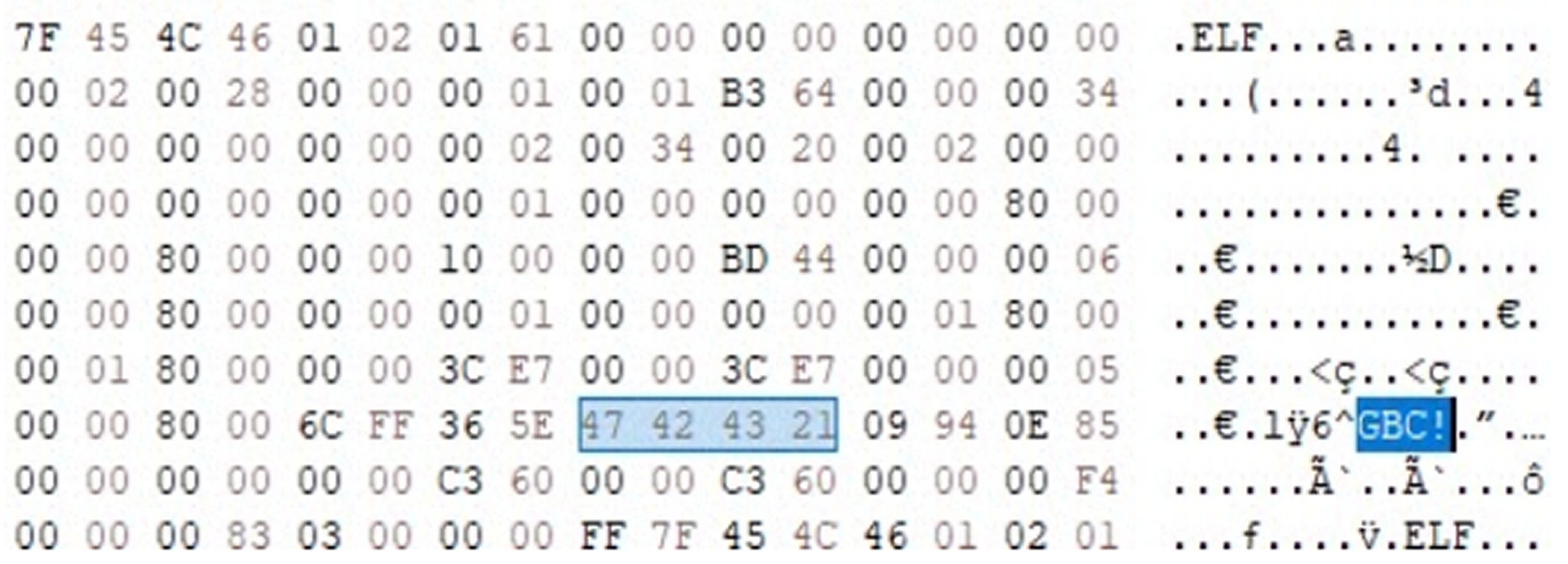
IOCONTROL Malware: Evasion Tactics and Persistence Mechanisms
Due to its modifications, standard UPX utilities are unable to unpack the IOCONTROL malware. However, cybersecurity researchers at Flashpoint discovered that restoring specific magic bytes (00 00 00 00 00 00 00 02 00 34 00 20 00 02 00 34) allows for successful decompression.
Execution and Persistence Strategy
Once executed, IOCONTROL unpacks itself directly into memory and establishes persistence using a multi-stage approach:
Directory Creation – The malware creates two directories:
- /tmp/iocontrol/
- /etc/rc3.d/
Both directories are given full read, write, and execute permissions, enabling the malware to stage payloads and maintain persistence across system reboots.
Startup Script Injection – A bash script is written to /etc/rc3.d/S99iocontrol, ensuring that the malware automatically executes at system startup. This script also includes a watchdog function, designed to restart the malware if it is terminated, further reinforcing persistence.
#!/bin/sh
/usr/bin/iocontrol >/dev/null 2>&1 &
while true; do
if ! pgrep -x "iocontrol" >/dev/null; then
/usr/bin/iocontrol >/dev/null 2>&1 &
fi
sleep 60
done
This approach guarantees uninterrupted operation, even if security tools attempt to halt the initial execution.
C2 Communication
The malware determines the IP address of its command-and-control (C2) server by performing a DNS query through CloudFlare. It extracts the relevant data from the response’s Answer[data] field. Once the IP is resolved, it initiates an MQTT connection with the broker, sending beacon packets that contain system metadata such as the kernel version, hostname, and time zone. These packets are encrypted using AES-256-CBC, with the encryption key derived from two environment variables, 0_0 and 0_1. These variables, assigned during execution, store hashed GUID values, which are then split into a key and an initialization vector (IV).
Security Challenges
The IOCONTROL malware employs a combination of IoT-focused protocols and credential-based initial access techniques, posing significant challenges for cybersecurity defenders. Its unique attack vectors make detection and mitigation more complex, especially in environments reliant on IoT systems.
Flashpoint’s research uncovered evidence that the malware’s developer attempted to sell it on underground forums, including BreachForums. This suggests a high likelihood of the malware being adopted by multiple threat actor groups, further increasing the potential risk of widespread exploitation.
Mitigation Strategies
Organizations responsible for operational technology (OT) environments must take proactive security measures to defend against this threat. Key mitigation strategies include regular firmware patching, network segmentation, and anomaly detection for MQTT traffic. Implementing these defenses can help reduce the risks associated with the evolving capabilities of IOCONTROL malware.


