Security Experts Discover Sophisticated Malware Campaign Targeting Android Users via Fake Chrome Install Pages
Cybersecurity researchers have identified a highly advanced malware operation aimed at Android users by luring them through counterfeit Google Chrome installation pages.
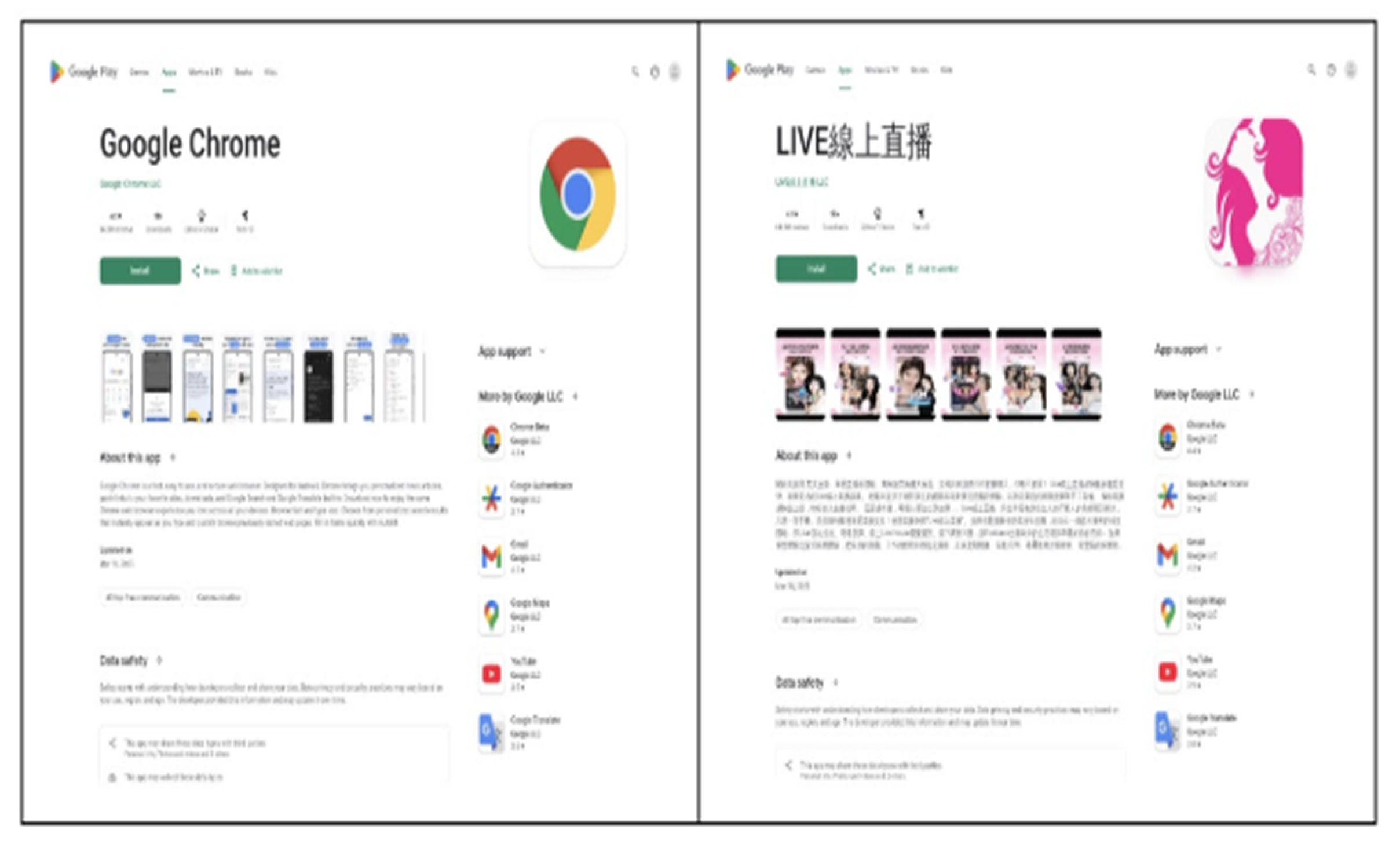
These attackers have developed deceptive websites hosted on newly registered domains that closely imitate the official Google Chrome install page found on the Google Play Store. These fake websites are being used to distribute SpyNote, a potent Android remote access trojan (RAT) that enables cybercriminals to spy on victims, steal sensitive data, and remotely control affected devices. The high visual resemblance to authentic Google Play pages makes it easy to deceive users into believing they are downloading legitimate apps directly from Google.
SpyNote stands out as a serious mobile security threat due to its wide range of intrusive capabilities.
Once the malware is installed, it can access critical data such as text messages, contacts, call logs, location details, and files stored on the device.
More concerning, SpyNote can activate the device’s camera and microphone, make and receive calls, execute remote commands, and log keystrokes to capture sensitive login credentials.
Investigations have linked SpyNote to known advanced persistent threat (APT) groups such as OilRig (APT34), APT-C-37 (Pat-Bear), and OilAlpha, highlighting its dual use for both cyber espionage and broader criminal exploitation.
Researchers at DomainTools noted recurring patterns in the campaign’s infrastructure. Many of the malicious domains were registered via NameSilo, LLC and XinNet Technology Corporation, and were hosted on servers associated with providers like Lightnode Limited and Vultr Holdings LLC. The fake sites shared nearly identical layouts, with only slight differences in malware setup and command-and-control (C2) configurations.
Interestingly, the malicious websites and the malware code often feature both English and Chinese, including Chinese-language comments, suggesting a potential link to threat actors based in or affiliated with China.
This malware campaign is especially dangerous to organizations that allow employees to use personal devices for work (BYOD environments), as infected devices could serve as gateways into secure corporate networks.
Because SpyNote is difficult to remove—often requiring a full factory reset—infected devices can pose long-term security risks. Its use of Android Accessibility Services allows it to intercept two-factor authentication codes and capture login credentials, making it a powerful tool for account takeovers and deeper intrusions into networks.
How the Attack Works
The fake websites use advanced visual tricks to appear credible. For example, they feature image sliders displaying fake screenshots of the Google Play interface, sourced from suspicious domains such as “bafanglaicai888[.]top” believed to be operated by the attackers. These visuals help build trust and reduce user skepticism.
When a user interacts with the fake interface, a JavaScript function named download() is triggered. This downloads a malicious .apk file from a pre-configured URL. That initial file acts as a dropper, installing a secondary embedded .apk containing the actual SpyNote payload.
SpyNote’s command and control functionality is implemented via a base.dex file hidden in the assets folder, which defines how it communicates with remote servers. The C2 servers typically use port 8282, and some versions of the malware directly include the IP address “66.42.63.74” in their code.
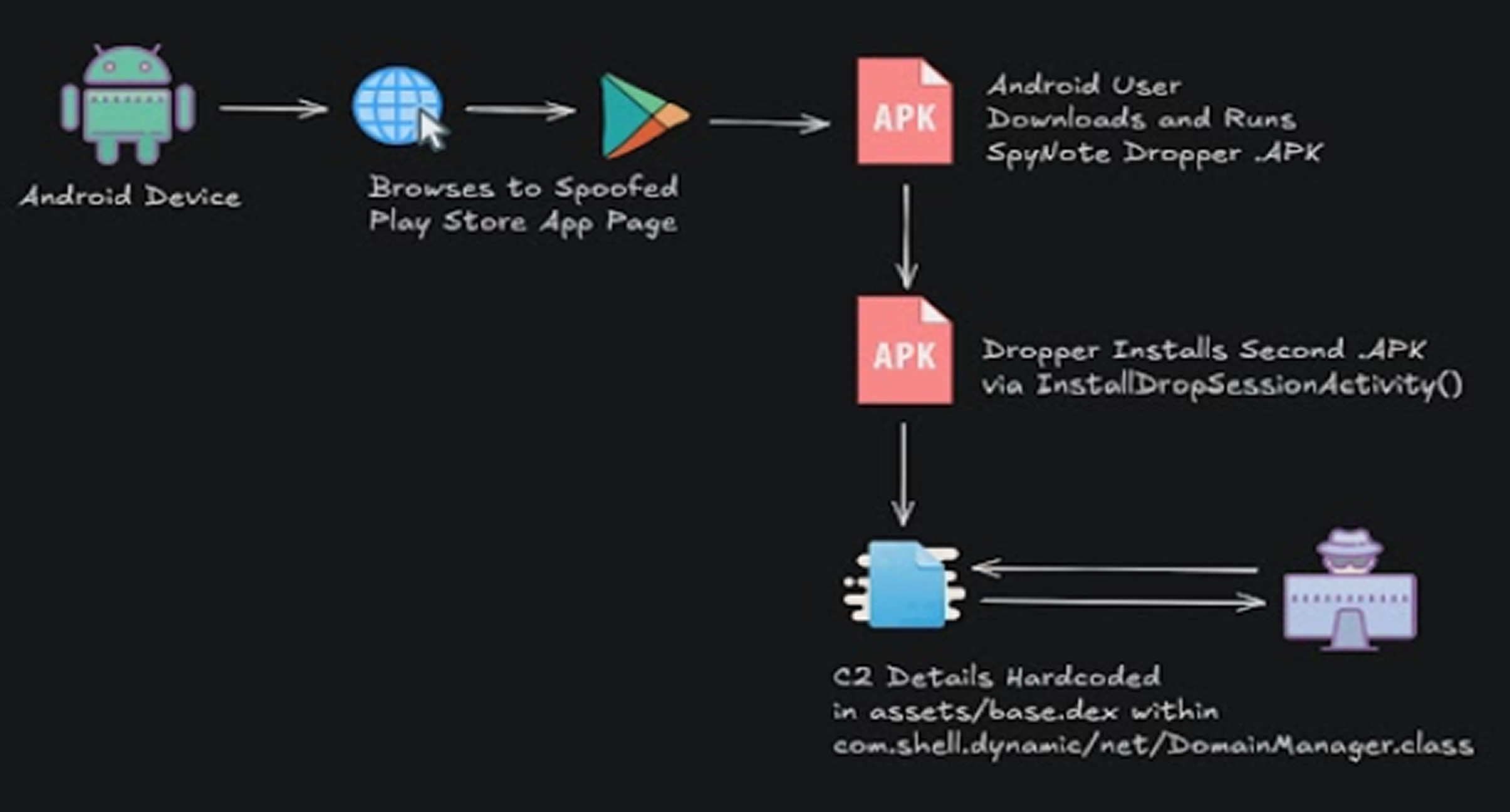
The infection process concludes with the malware requesting a broad range of permissions to take full control of the compromised device and maintain a persistent link to attacker-controlled infrastructure.
This campaign showcases the growing complexity of mobile threats and reinforces the importance of verifying the source of any app before installation—even if a site seems legitimate.
Found this article interesting? Follow us on X(Twitter) and FaceBook to read more exclusive content we post.


