ClickFix: A Deceptive CAPTCHA Scam Exploiting User Trust to Deliver Malware
A new social engineering technique called ClickFix has surfaced, tricking users into executing malicious commands by mimicking CAPTCHA verification processes. This method manipulates users’ trust in CAPTCHA systems, which are typically used to differentiate humans from bots online.
Exploiting User Trust
The ClickFix attack begins with a fake pop-up on a compromised or malicious website, displaying a bogus bot verification message. Users are asked to follow three simple steps to "confirm" their identity.
First, they are instructed to press Windows Key + R to open the Run dialog box. Next, they press CTRL + V to paste malicious code that has been preloaded onto the website’s virtual clipboard. Finally, they press Enter, unknowingly executing the malicious command.
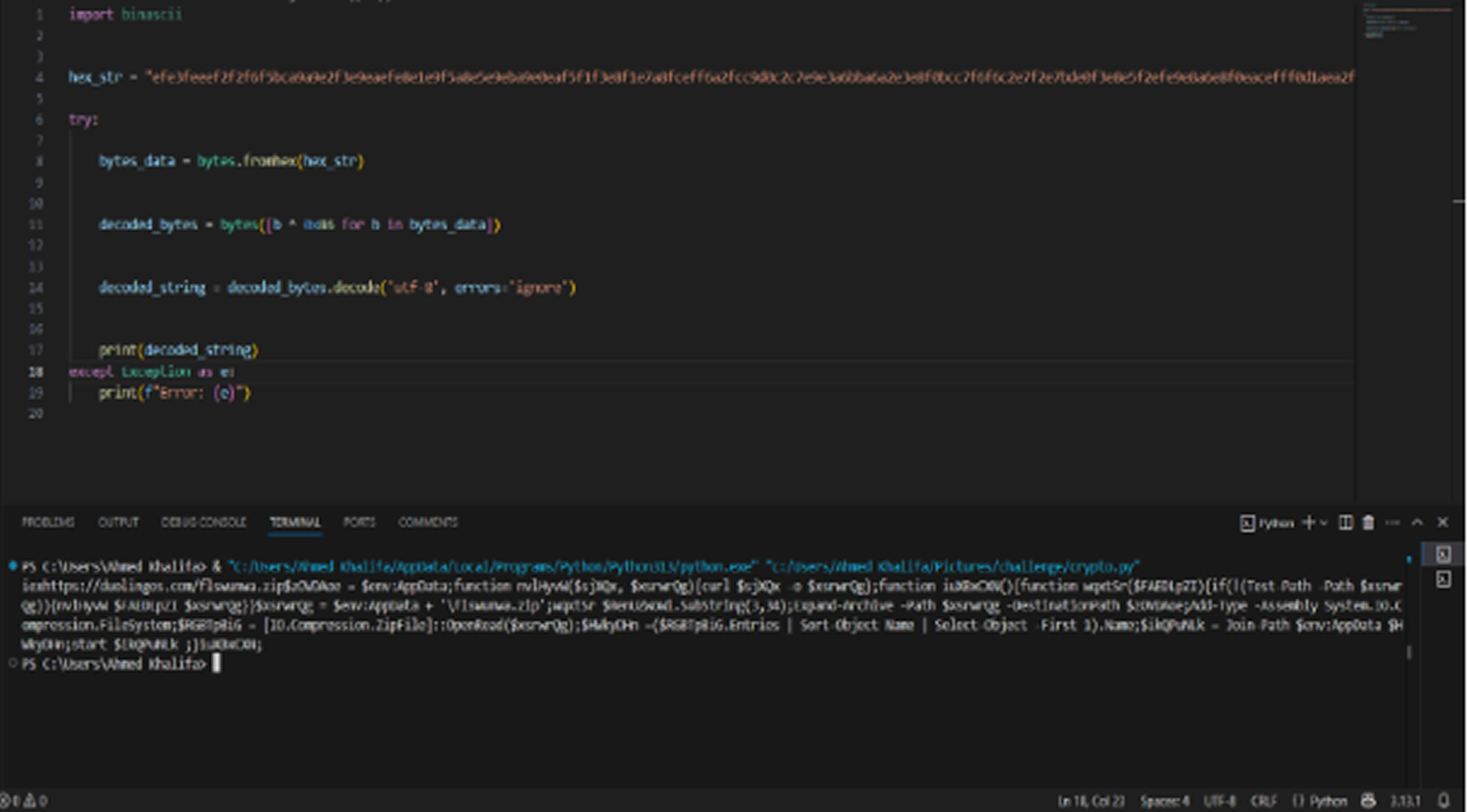
This process triggers malware downloads through Windows utilities like mshta.exe, allowing attackers to install infostealers, ransomware, and banking trojans such as Qakbot. According to DarkAtlas, this technique preys on human behavior, using familiar online interactions to spread malware without raising suspicion.
Qakbot and Other Malware Threats
Qakbot, a banking trojan first discovered in 2008, has evolved into a powerful malware capable of delivering additional threats, including ransomware. It enables attackers to gain initial access to systems, move laterally within networks, and deploy secondary infections.
By integrating Qakbot with the ClickFix technique, cybercriminals can bypass traditional security defenses, as the malware execution relies on user actions rather than automated exploits. This makes it harder for security solutions to detect and block the attack.
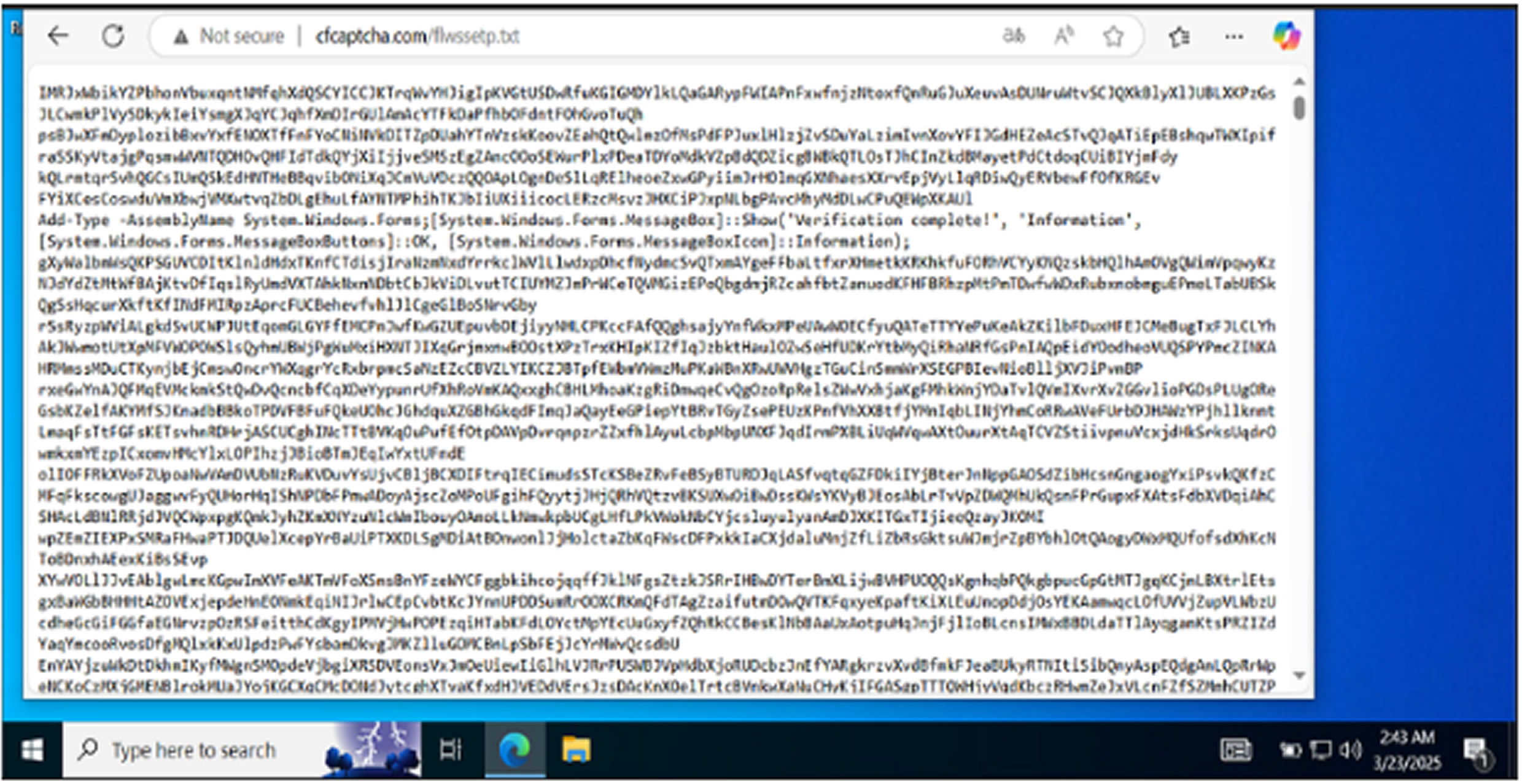
Obfuscation Tactics and Mitigation Efforts
To further evade detection, attackers employ obfuscation techniques, such as encrypting payloads and generating dynamic URLs to distribute malware. This allows them to create an unlimited number of unique download links, making it difficult for cybersecurity professionals to blacklist malicious sites.
Additionally, they use PHP scripts as intermediaries to conceal the true source of the attack, adding another layer of complexity for threat analysts trying to track and mitigate the campaign.
Currently, cybersecurity teams are working to dismantle the infrastructure behind these attacks by taking down associated domains and removing malicious content. However, users must remain vigilant and avoid executing unexpected commands prompted by online pop-ups to prevent falling victim to such deceptive tactics.