"mu-plugins" directory in WordPress sites to discreetly inject malicious code
Cybercriminals are exploiting the "mu-plugins" directory in WordPress sites to discreetly inject malicious code, allowing them to maintain long-term remote access and redirect visitors to fraudulent websites. This tactic enables hackers to operate undetected while compromising site security.
The "mu-plugins" directory, short for must-use plugins, is located in the wp-content/mu-plugins folder. Unlike regular plugins, these are automatically activated by WordPress without requiring manual enablement via the admin dashboard. This makes the directory an ideal hiding spot for malware, as must-use plugins do not appear in the standard WordPress plugin list, reducing the chances of detection. According to Sucuri researcher Puja Srivastava, this emerging threat is concerning because users often overlook must-use plugins during security audits.
Sucuri's investigation revealed three distinct types of malicious PHP scripts within compromised WordPress sites. The redirect.php script redirects visitors to external malicious websites, often masquerading as a browser update to trick users into downloading malware. The index.php file functions as a web shell, enabling attackers to execute arbitrary commands by fetching and running a remote PHP script from GitHub. Meanwhile, the custom-js-loader.php script injects spam content into websites, replacing images with explicit material and hijacking outbound links to scam sites, likely to manipulate SEO rankings.
A particularly deceptive feature of the redirect.php script is its ability to detect whether a visitor is a bot. By excluding search engine crawlers from its redirection mechanism, it prevents security systems from flagging the compromised site, allowing the attack to persist undetected.
In addition to hijacking WordPress sites, hackers are using them as malware distribution hubs. One prevalent attack method, known as ClickFix, deceives users into running malicious PowerShell commands on Windows devices under the guise of a Google reCAPTCHA or Cloudflare CAPTCHA verification. This technique has been linked to the distribution of Lumma Stealer, a malware designed to harvest sensitive data. Compromised WordPress sites are also being used to deploy malicious JavaScript, which can either redirect visitors to suspicious third-party domains or act as a skimmer to steal financial information entered on checkout pages.
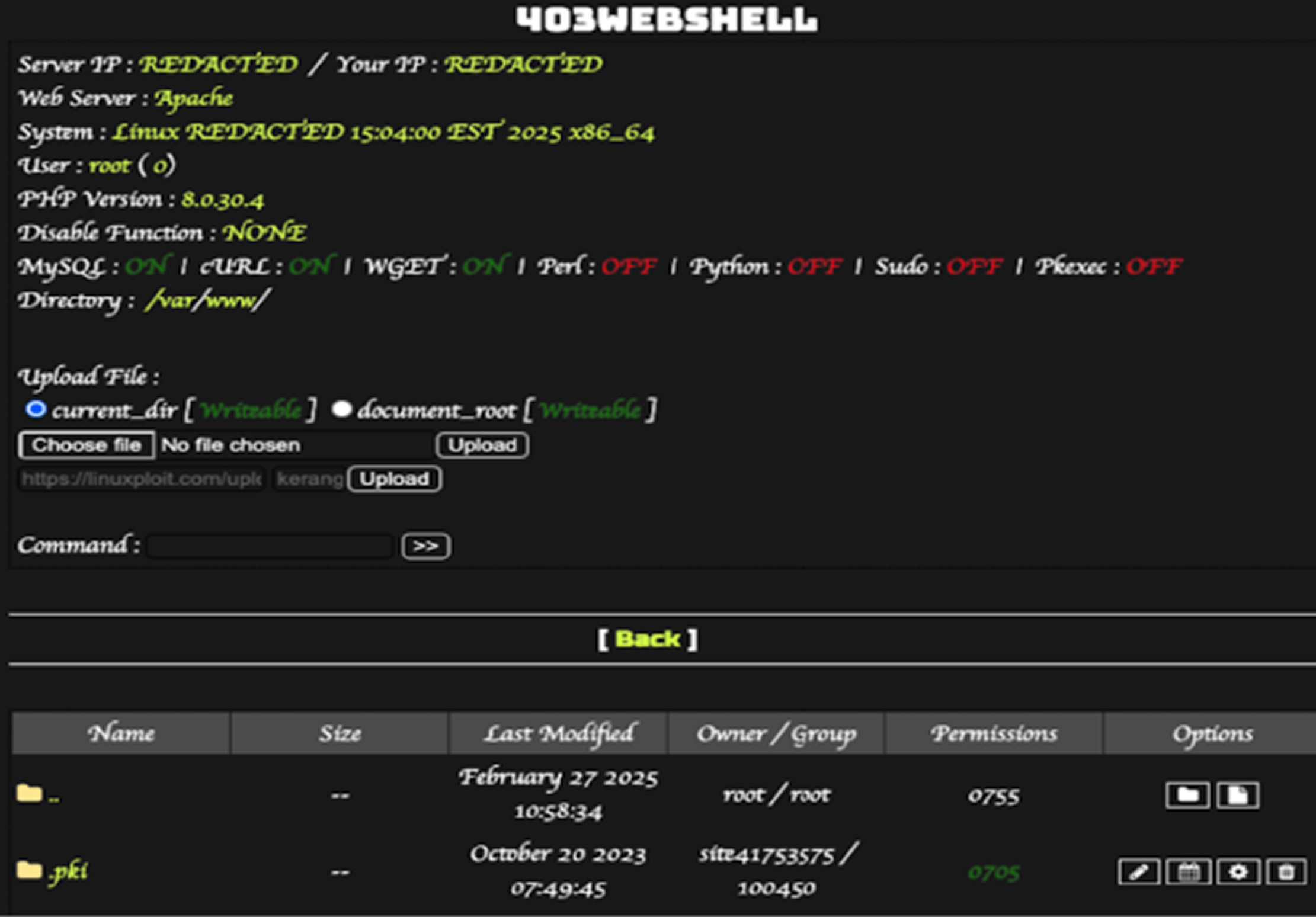
Although the exact method of these website breaches remains unclear, common attack vectors include vulnerabilities in plugins and themes, compromised admin credentials, and misconfigured servers. A report from Patchstack highlights four major WordPress security flaws that hackers have actively exploited this year. These include CVE-2024-27956, an SQL injection vulnerability in the WordPress Automatic Plugin, CVE-2024-25600, a remote code execution flaw in the Bricks theme, CVE-2024-8353, a PHP object injection vulnerability in the GiveWP plugin, and CVE-2024-4345, an arbitrary file upload flaw in Startklar Elementor Addons.
To protect WordPress sites from these threats, website owners should take proactive security measures. Keeping all plugins and themes up to date is essential to patch vulnerabilities before they can be exploited. Regular security audits should be conducted to identify and remove hidden malware. Strong passwords and two-factor authentication (2FA) should be enforced to prevent unauthorized access. Additionally, deploying a Web Application Firewall (WAF) can help block malicious requests and prevent code injection attacks.
By implementing these safeguards, WordPress site owners can significantly reduce the risk of cybercriminals using their platforms as a launchpad for malware and phishing campaigns.
Found this article interesting? Follow us on X(Twitter) and FaceBook to read more exclusive content we post.