Attackers Exploit COM Objects for Fileless Malware and Lateral Movement
Researchers have uncovered a sophisticated attack technique that abuses Component Object Model (COM) objects to execute fileless malware, enabling lateral movement across networks. This method allows attackers to maintain persistence and evade traditional security defenses by leveraging legitimate Windows functionality, marking a significant advancement in cyberattack strategies.
The Component Object Model (COM) is a binary interface standard introduced in the early 1990s and remains a core component of modern Windows operating systems. It enables different software components to interact across various programming languages, making it a valuable target for cybercriminals. Attackers exploit this functionality to execute malicious code without creating suspicious artifacts on disk.
Expanding on Previous Research
IBM security analysts traced this attack technique to research conducted by James Forshaw of Google Project Zero in February 2025. Forshaw identified a method to exploit Distributed COM (DCOM) remoting technology, allowing trapped COM objects to execute .NET managed code within server-side DCOM processes. This exploitation bypasses security protections such as Protected Process Light (PPL) and can escalate privileges.
Further advancing this research, security experts Dylan Tran and Jimmy Bayne developed a proof-of-concept (PoC) demonstrating how attackers could use DCOM for fileless lateral movement. Their findings revealed that DCOM can be leveraged to manipulate remote registry settings and execute malicious code, all while remaining hidden from traditional detection mechanisms.
Exploiting Windows Processes for Stealthy Execution
One of the key aspects of this attack is its ability to operate within legitimate Windows processes, particularly targeting the WaaSMedicSvc service, which runs under the SYSTEM account inside a protected svchost.exe process. This makes detection exceptionally difficult because the malware is executed entirely in memory and does not rely on disk-based files that antivirus software typically scans.
Infection Mechanism
The attack begins by manipulating remote registry settings to enable .NET reflection over DCOM. This is achieved by modifying the values AllowDCOMReflection and OnlyUseLatestCLR within the HKLM\Software\Microsoft.NetFramework registry path.
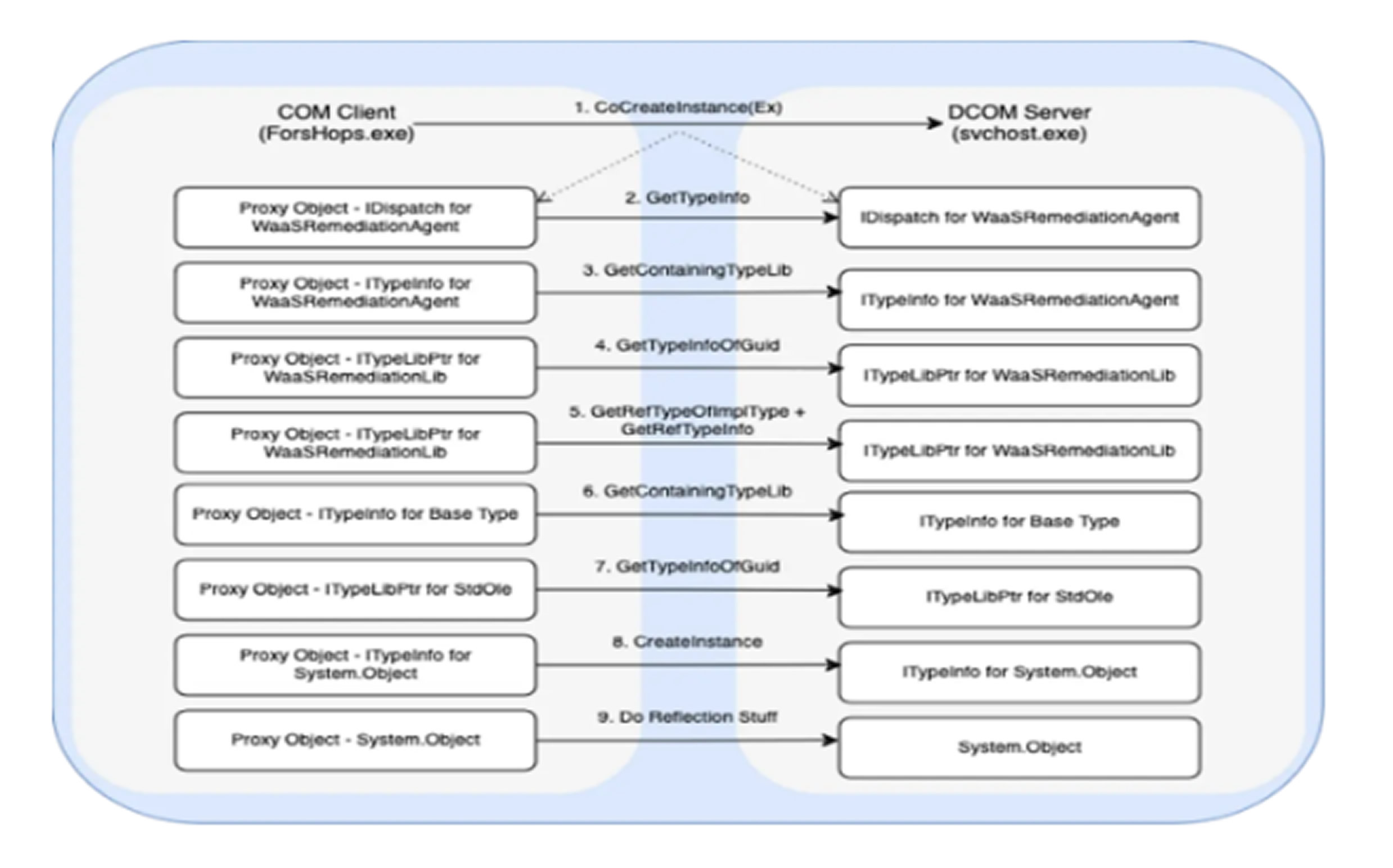
Next, attackers exploit COM hijacking by altering the TreatAs key of the StandardFont CLSID, effectively redirecting execution flow. This technique allows them to dynamically load malicious .NET assemblies via Assembly.Load over DCOM, ensuring execution occurs entirely in memory within a Protected Process Light svchost.exe context.
Since the malware never touches disk storage, traditional file-based antivirus solutions cannot detect or remove it.
Mitigation and Security Recommendations
To counter this threat, security professionals suggest:
Monitoring for CLR load events within svchost.exe processes.
Detecting unauthorized registry modifications, especially those targeting COM-related keys. Implementing host-based firewall restrictions to limit DCOM communication.
As attackers continue refining fileless malware techniques, organizations must stay vigilant by adopting advanced detection methods that go beyond traditional signature-based antivirus solutions.
Found this article interesting? Follow us on X(Twitter) and FaceBook to read more exclusive content we post.


