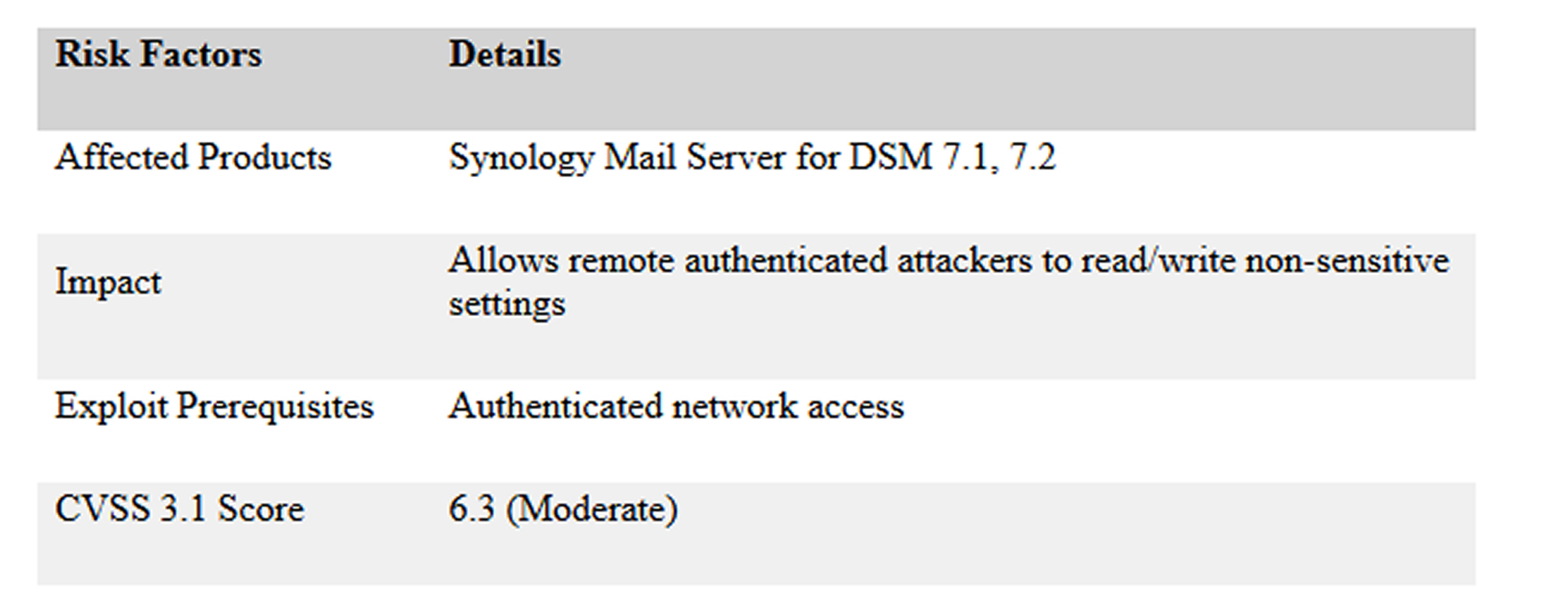
Synology Mail Server, allowing remote authenticated attackers to modify non-sensitive settings
A moderate-severity vulnerability has been discovered in Synology Mail Server, allowing remote authenticated attackers to modify non-sensitive settings and disable certain non-critical functions. Tracked as , the flaw affects multiple versions of the widely used mail server software. In response, Synology has released security patches to address the issue.
With a CVSS Base Score of 6.3, the vulnerability has been classified as moderate, posing risks to confidentiality, integrity, and availability. It enables remote authenticated users to manipulate system configurations without requiring user interaction. The flaw was identified by security researcher Chanin Kim and reported to Synology through their responsible disclosure program.
While full technical details remain undisclosed until patches are widely implemented, the vulnerability likely stems from insufficient access controls, allowing authenticated users to access or modify settings beyond their intended permissions.
The summary of the vulnerability is given below:
Affected Products and Remediation
The vulnerability impacts the following Synology Mail Server versions:
- DSM 7.2 – Fixed in version 1.7.6-20676 or later.
- DSM 7.1 – Fixed in version 1.7.6-10676 or later.
Users are strongly advised to update their mail server installations immediately, as no alternative mitigation strategies are available. The software update remains the only effective protection against potential exploitation.
This security flaw arises amidst broader cybersecurity concerns surrounding network-attached storage (NAS) devices and related services.
Synology’s Security Response
In 2024, Synology addressed 13 security vulnerabilities across its product line. Earlier this year, the company also patched multiple flaws in Synology Router Manager (SRM) software, which previously allowed authenticated users to read or modify non-sensitive files.
Taiwanese security firm QI-ANXIN Group’s Codesafe Team has also identified multiple vulnerabilities in Synology products, highlighting the continued scrutiny these systems receive from security researchers.
Recommended Security Measures
To enhance security, Synology users should:
- Update to the patched versions specified in the advisory.
- Implement geo-blocking to restrict access to authorized regions.
- Enable two-factor authentication (2FA) for all administrator accounts.
- Configure automatic security notifications to track failed login attempts or unusual activity.
Synology follows a responsible disclosure policy, ensuring security vulnerabilities are not publicly disclosed until patches are available.
As with all critical updates, administrators are advised to test patched versions in non-production environments before deploying them to live systems.


