An Iranian state-sponsored hacking group tied to the Islamic Revolutionary Guard Corps
(IRGC) has been linked to a spear-phishing campaign aimed at journalists, cybersecurity experts, and computer science professors in Israel.
According to a report published by Check Point, attackers in these campaigns posed as fake assistants to tech executives or researchers, reaching out via emails and WhatsApp messages. Once targets responded, they were directed to fake Gmail login pages or fraudulent Google Meet invitations.
The threat activity has been attributed to a cluster called Educated Manticore, which overlaps with groups known as APT35, APT42, Charming Kitten, CharmingCypress, Cobalt Illusion, Magic Hound, Mint Sandstorm (formerly Phosphorus), TA453, and others. This group is known for social engineering tactics that use fake personas on platforms like Facebook and LinkedIn to deceive victims into installing malware.
Check Point observed a new wave of activity beginning in mid-June 2025, after tensions escalated between Iran and Israel. The group used fake meeting invites sent via email or WhatsApp to lure targets. The messages were highly structured and grammatically flawless, suggesting the use of AI tools to draft them. One such message exploited current geopolitical tensions by asking a target to join a meeting under the pretense of needing help with an AI-based threat detection system.
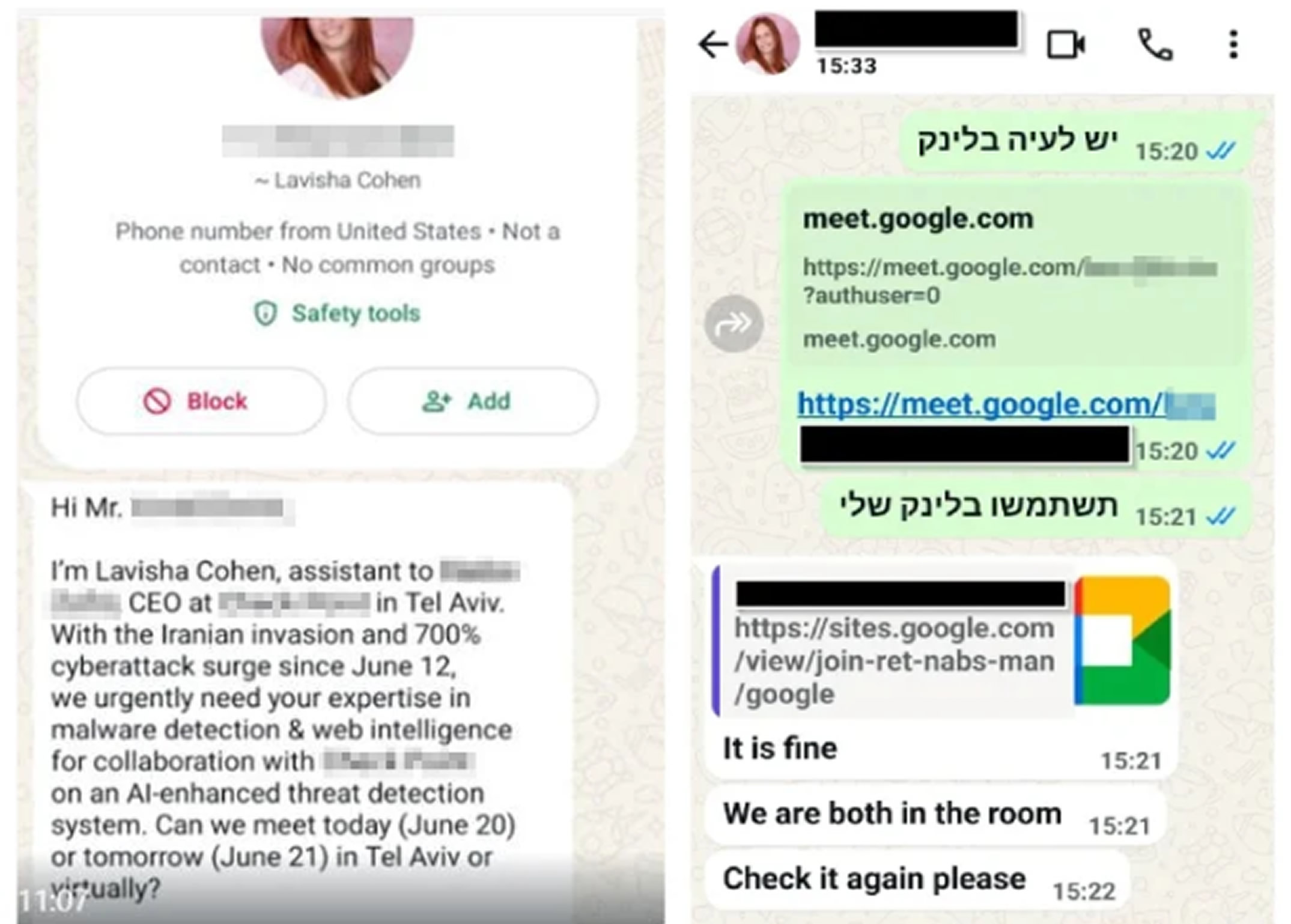
Initial outreach messages are not malicious, aiming first to build trust. Once rapport is established, the attackers send phishing links that lead to fake login pages designed to steal Google credentials. Check Point notes that attackers often ask for the victim’s email address before sending the link, which is then auto-filled on the phishing page to enhance credibility.
The phishing toolkit mimics Google login interfaces using modern technologies such as React-based single-page applications, dynamic routing, and real-time WebSocket connections to transmit stolen data. The toolkit also hides its source code to evade detection.
It captures login credentials and two-factor authentication (2FA) codes to carry out 2FA relay attacks. It also includes a passive keylogger to record keystrokes, even if the user abandons the login process.
Some campaigns also used Google Sites to host fake Google Meet pages, designed to look authentic but redirecting users to phishing sites when clicked.
Check Point warned that Educated Manticore remains a serious and persistent threat, especially to individuals in Israel during this conflict period. The group operates aggressively, rapidly creating and removing domains and infrastructure to stay ahead of detection efforts.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



