Threat intelligence company GreyNoise has reported a sharp increase in scanning activity targeting Progress MOVEit Transfer systems beginning May 27, 2025. This spike suggests
that threat actors may be preparing for another large-scale exploitation effort or searching for systems that remain unpatched.
MOVEit Transfer is a widely used managed file transfer tool that allows businesses and government agencies to securely share sensitive data. Due to its high-value data handling, it remains an attractive target for attackers.
Before May 27, scanning activity was minimal, typically involving fewer than 10 IP addresses per day. However, GreyNoise observed a jump to over 100 unique IPs on May 27, followed by 319 the next day. Since then, the number has fluctuated between 200 and 300 IPs daily, indicating a clear departure from the usual pattern.
Over the past 90 days, GreyNoise identified 682 unique IPs connected to this activity, with 449 detected in just the past 24 hours. Among those, 344 were labeled suspicious and 77 were flagged as malicious. Most of these IPs are based in the United States, followed by Germany, Japan, Singapore, Brazil, the Netherlands, South Korea, Hong Kong, and Indonesia.
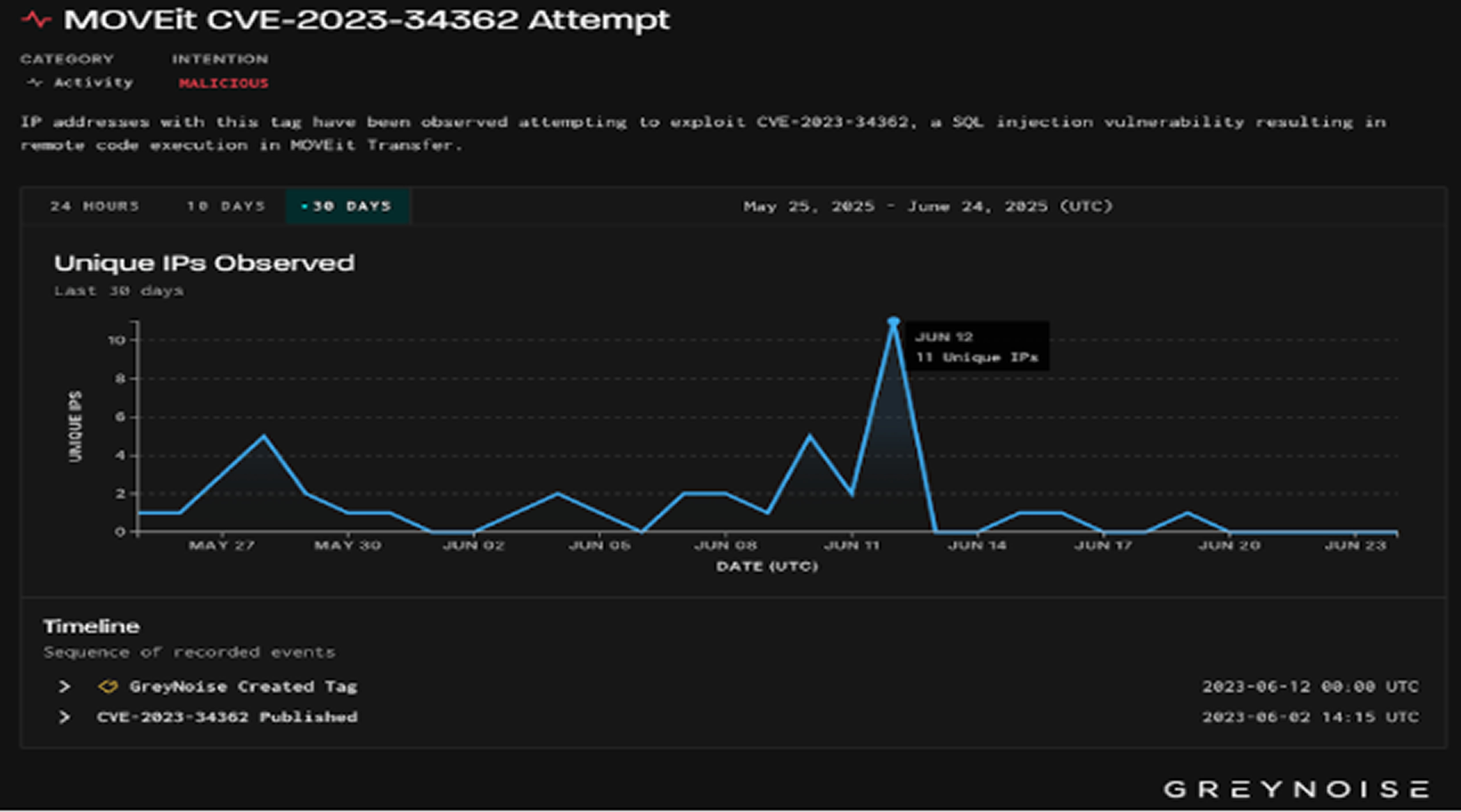
GreyNoise also noted a small number of attempts to exploit two known MOVEit Transfer vulnerabilities CVE-2023-34362 and CVE-2023-36934 on June 12, 2025. The CVE-2023-34362 flaw was previously used by the Cl0p ransomware group in 2023 to launch a widespread attack that affected over 2,770 organizations.
The recent surge in scanning is a strong signal that MOVEit Transfer systems are once again being targeted. Users are urged to block suspicious IP addresses, update their software, and ensure the systems are not exposed to the public internet.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



