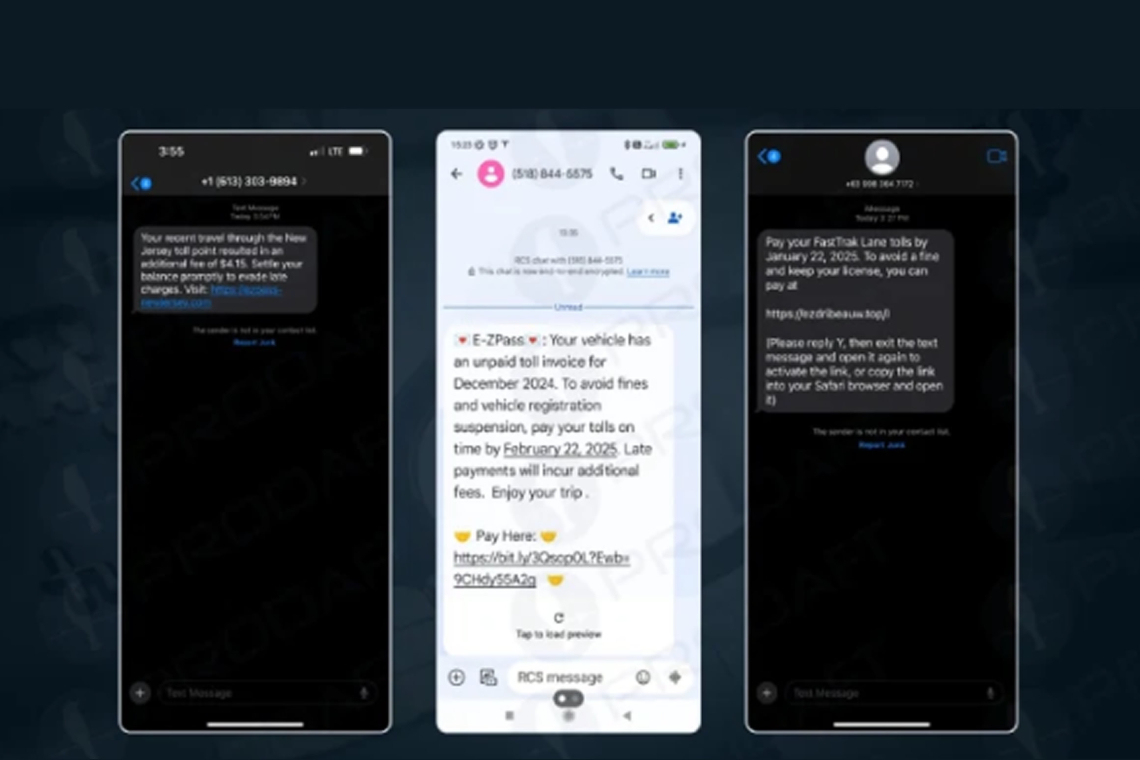
A newly discovered phishing-as-a-service (PhaaS) platform called Lucid has been identified targeting 169 entities across 88 countries using smishing (SMS phishing)
attacks via Apple iMessage and Rich Communication Services (RCS) for Android. This sophisticated attack method enables cybercriminals to bypass traditional SMS spam filters, significantly increasing the reach and success rate of their phishing campaigns. By leveraging legitimate communication platforms, Lucid makes it more difficult for security systems to detect and block malicious messages.
Lucid operates as a subscription-based service, allowing cybercriminals to conduct large-scale phishing campaigns aimed at harvesting credit card details and personally identifiable information (PII) for financial fraud. A key feature of the platform is its ability to clone official websites of postal services, courier companies, toll systems, and tax agencies, tricking victims into providing sensitive data. Additionally, it incorporates advanced anti-detection measures, including IP blocking, user-agent filtering, and time-limited single-use phishing URLs, making it even harder to track and take down phishing operations.

The platform is linked to a Chinese-speaking hacking group called XinXin, which is also responsible for developing other PhaaS services such as Lighthouse and Darcula. These services are marketed through Telegram, forming a lucrative underground cybercrime economy. The developer of Lucid, known as LARVA-242, is believed to play a key role in XinXin’s operations. Investigations suggest that multiple PhaaS services share common phishing templates, target lists, and operational tactics, pointing to a highly organized and interconnected cybercrime ecosystem.
Lucid’s phishing campaigns are executed through a large-scale, automated backend infrastructure. Attackers use iPhone device farms and Windows-based mobile emulators to send hundreds of thousands of scam messages containing phishing links. The targeted phone numbers are obtained through data breaches and cybercrime forums. To bypass iMessage’s security filters, attackers create temporary Apple IDs with impersonated display names and use the "reply with Y" technique to establish two-way communication. Meanwhile, RCS filtering is evaded by frequently rotating sending domains and numbers to prevent detection.
One of Lucid’s most concerning features is its real-time phishing panel, which allows attackers to monitor victim interactions with phishing links in real-time. This panel, built using the Webman PHP framework, enables cybercriminals to track and extract sensitive information, including credit card details, which are further subjected to verification steps before being used or sold on dark web marketplaces.
The rise of phishing-as-a-service platforms like Lucid is part of a growing trend where cybercriminals can easily access advanced phishing tools without needing technical expertise. Recent research from Barracuda has identified a massive spike in PhaaS attacks in early 2025, with services like Tycoon 2FA, EvilProxy, and Sneaky 2FA leading the majority of incidents. Cybersecurity experts warn that phishing emails remain a major entry point for cyber threats, including ransomware, credential theft, and financial fraud. As PhaaS platforms become more advanced and evasive, traditional security tools face increasing challenges in detecting and mitigating these sophisticated phishing attacks.
Found this article interesting? Follow us on X(Twitter) and FaceBook to read more exclusive content we post.