A critical security vulnerability in Plantronics Hub software allows attackers to escalate privileges due to an unquoted search path weakness.
This flaw affects versions 3.24.5 through 3.25.2 and becomes particularly dangerous when used alongside OpenScape Fusion for MS Office, a common startup application in corporate environments. The vulnerability exploits Windows’ handling of unquoted paths with spaces, creating an opportunity for privilege escalation.
When OpenScape attempts to launch Plantronics Hub using the registry path:
C:\Program Files (x86)\Plantronics\Spokes3G SDK\PLTHub.exe,
Windows first tries to execute C:\Program.exe before checking the full path. This behavior becomes an attack vector if users have write permissions to the C:\ directory, allowing them to place a malicious Program.exe file that executes with elevated privileges.
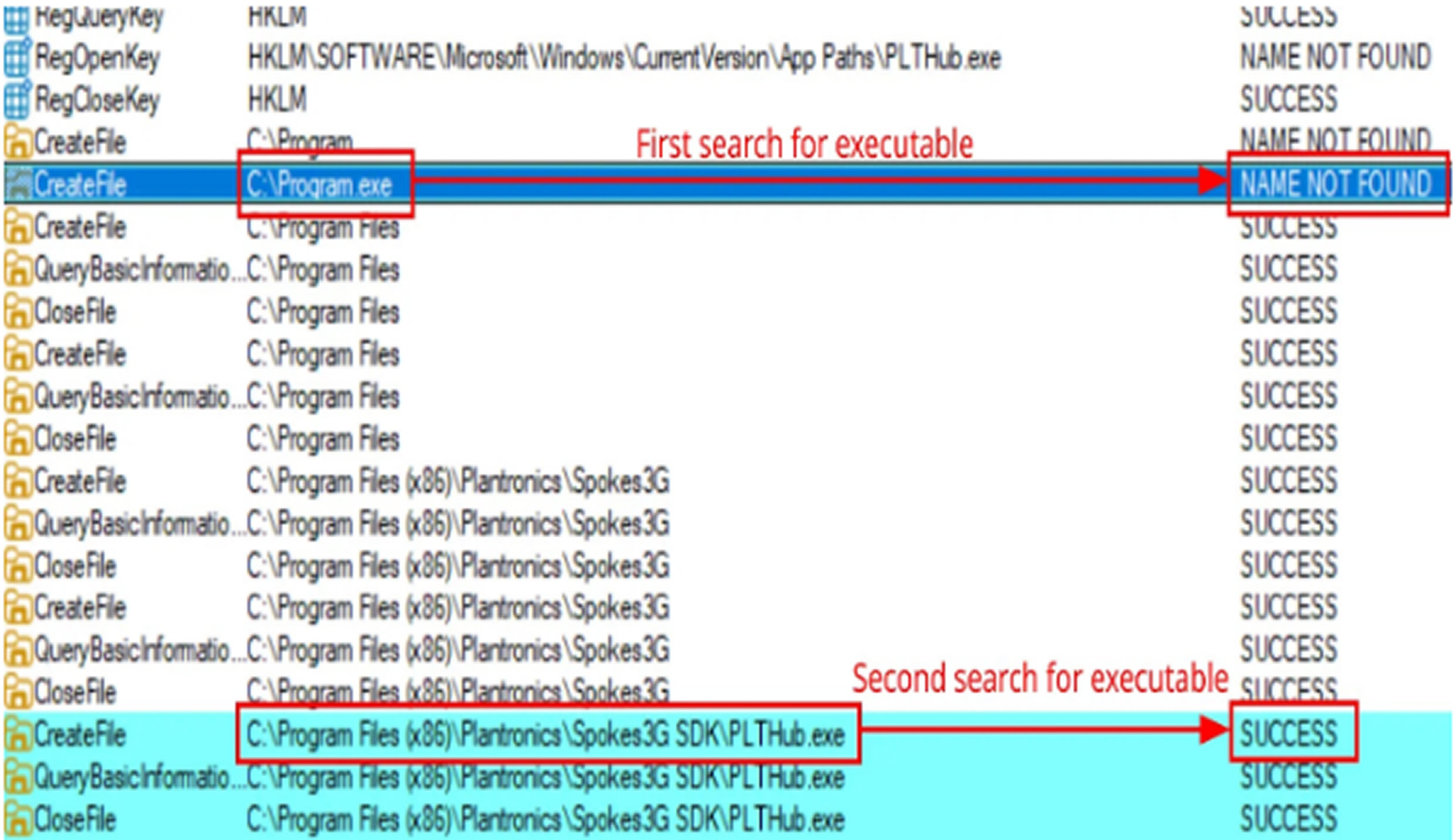
8Com security researchers identified that attackers can exploit this flaw by placing three files in the C:\ directory:
- Program.exe (Entry point)
- aka.exe (UAC bypass)
- ape.exe.lnk (Payload)
Once OpenScape starts at system startup, it triggers the execution chain, launching Program.exe instead of the intended Plantronics Hub executable, leading to privilege escalation. This vulnerability is categorized as CWE-428: Unquoted Search Path or Element, a well-known security weakness where applications fail to correctly quote paths that contain spaces.
Infection Mechanism
The attack relies on the LocalServer32 registry key, which stores the unquoted path to PLTHub.exe.
- When executed, Program.exe calls aka.exe, bypassing User Account Control (UAC) and running the payload (ape.exe.lnk) with administrative privileges.
- The exploit is triggered when an administrator logs in, automatically launching OpenScape Fusion, which in turn starts Plantronics Hub through the vulnerable path.
Mitigation and Response
Currently, no patch is available as Plantronics Hub is no longer officially supported by HP.
To mitigate the risk, security professionals should:
- Manually quote the registry path to prevent Windows from misinterpreting the execution order.
- Restrict write permissions to the C:\ directory, ensuring that only administrators can modify it.
HP has updated its End of Commercial Sale Notice to inform customers about this vulnerability, advising them to take the necessary security precautions.
Found this article interesting? Follow us on X(Twitter) and FaceBook to read more exclusive content we post.


