Fake CAPTCHA Pages Used to Spread Lumma Stealer Malware
Cybercriminals are leveraging fake CAPTCHA pages to spread Lumma Stealer, a powerful information-stealing malware that has gained popularity in underground markets since its launch in 2022. By March 2025, the malware-as-a-service (MaaS) platform had attracted over 1,000 active subscribers, with subscriptions starting at $250.
How the Attack Works
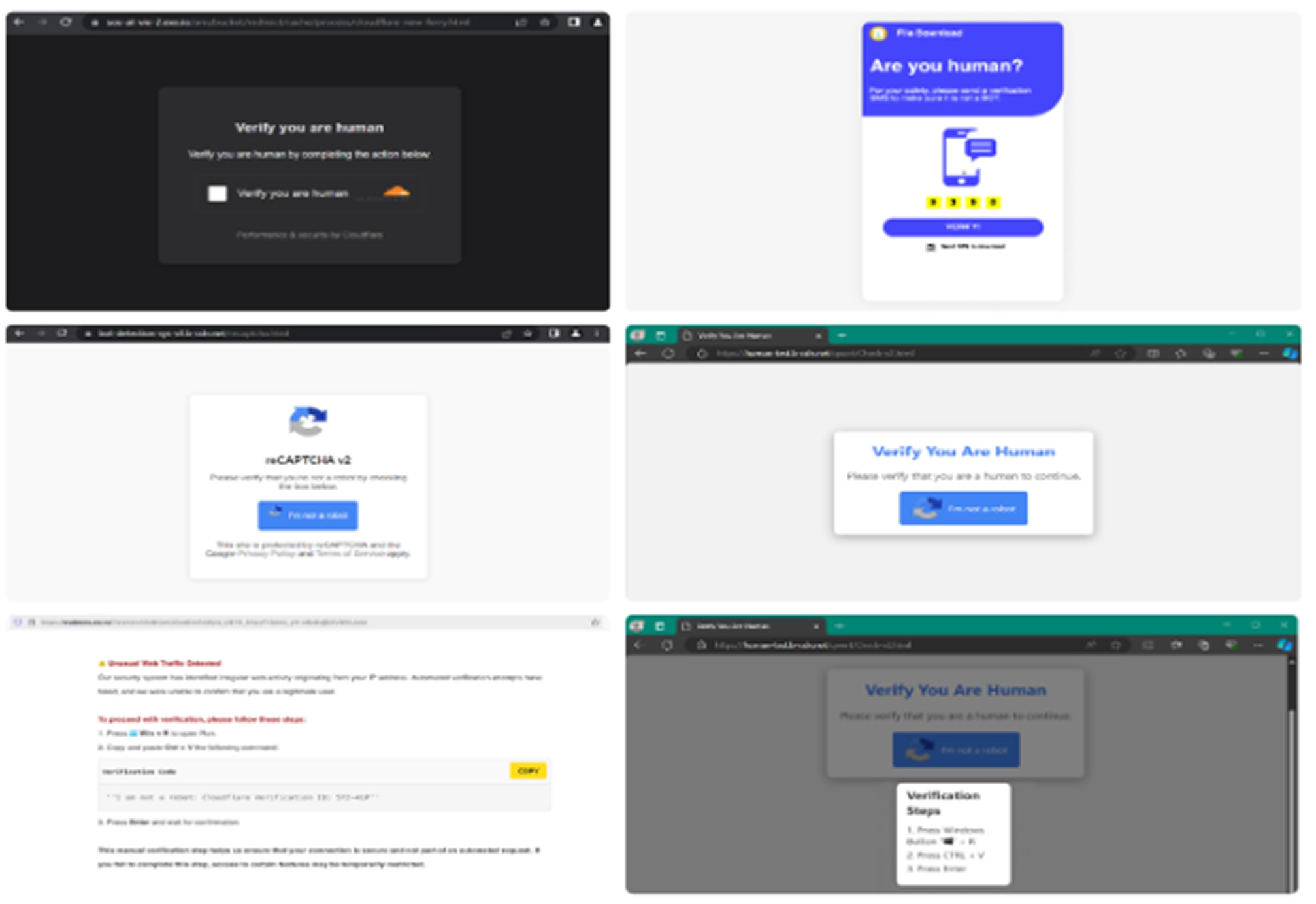
According to Kaspersky, the campaign tricks users with familiar-looking CAPTCHA prompts, mimicking Google reCAPTCHA or Cloudflare's verification systems. Victims encounter these fakes on cloned pirated media sites and fraudulent Telegram channels posing as crypto or piracy communities.
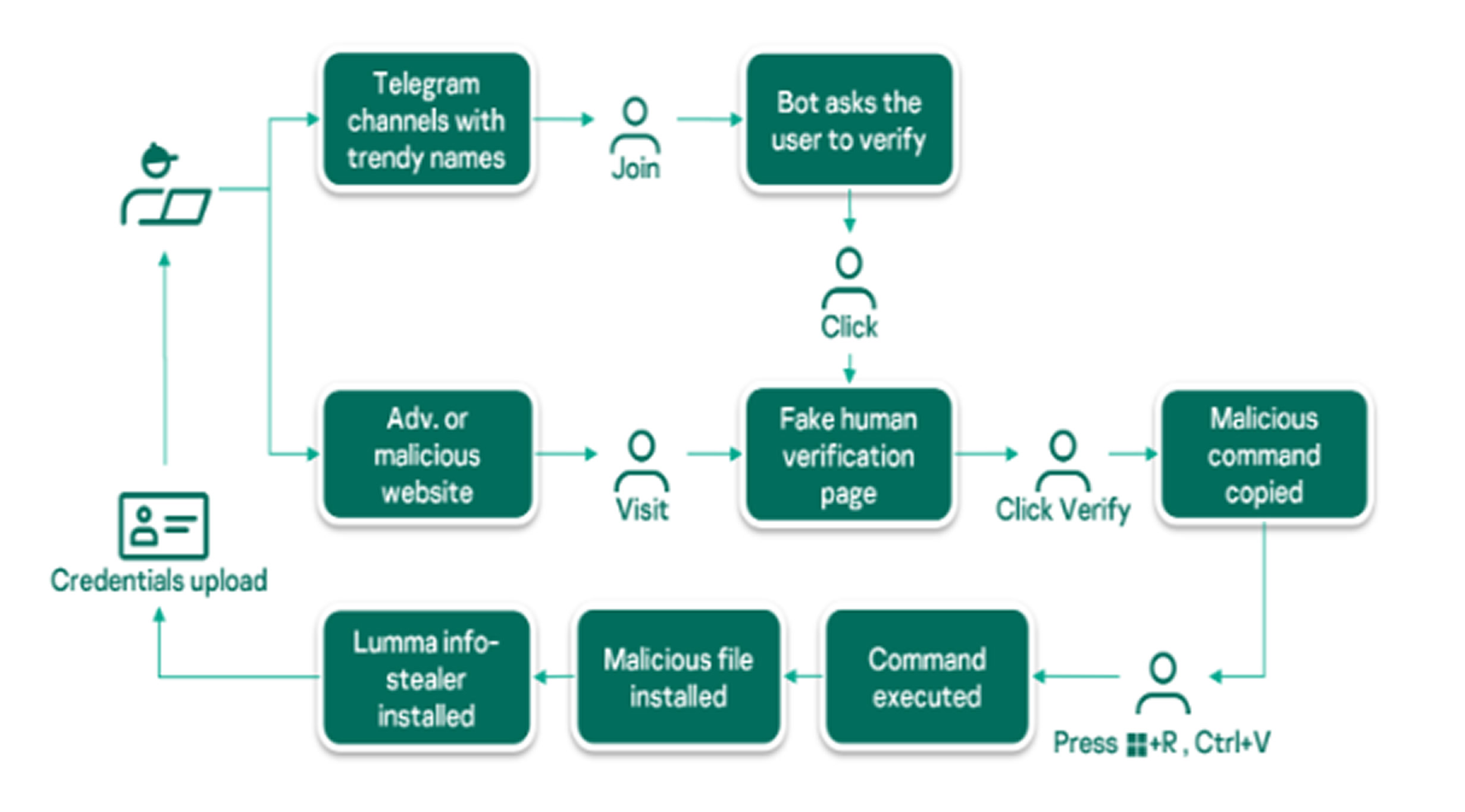
Clicking the fake "I'm not a robot" or "Verify" button secretly copies a malicious PowerShell command to the clipboard. Users are then instructed to run this command via Win+R, unknowingly triggering a Base64-encoded script that initiates the malware’s infection process.
Technical Infection Details
Lumma uses multiple advanced tactics to avoid detection:
- It downloads a ZIP file to %AppData%\Roaming\, extracts it to a hidden folder, and ensures persistence by modifying the Windows Registry.
- In more complex attacks, malicious JavaScript hidden in media files is executed using Microsoft's mshta.exe to deploy the payload.
- It employs DLL sideloading and code injection into trusted apps to slip past defenses.
- The malware checks for antivirus tools like Avast, AVG, McAfee, and Bitdefender before activating.
Data Theft Capabilities
Once installed, Lumma Stealer harvests:
- Crypto wallet credentials and extensions (e.g., MetaMask)
- Two-factor authentication data
- Browser cookies and saved logins
- Remote access tool credentials (e.g., AnyDesk)
- Password manager data (e.g., KeePass)
- Credit card and financial info
Stolen data is exfiltrated to command-and-control servers via encrypted HTTP POST requests to domains like reinforcenh[.]shop.
Security Advice
Experts urge users to be cautious around unexpected CAPTCHA prompts, especially on piracy or crypto-related sites. Avoid executing clipboard content unless you're sure of its purpose.
Organizations should prioritize endpoint protection, enforce user training, and monitor for suspicious activity to defend against Lumma, which has already been linked to corporate breaches and potential ransomware entry points
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.