New SparkKitty Malware Targets Crypto Wallets on Android and iOS
A new form of mobile malware known as SparkKitty has been discovered in apps available on both Google Play and the Apple App Store. This malware targets Android and iOS users with the aim of stealing cryptocurrency-related data.
SparkKitty appears to be a more advanced version of SparkCat, which Kaspersky identified in January. SparkCat was known for using optical character recognition (OCR) to capture recovery phrases from images stored on compromised devices.
When setting up a cryptocurrency wallet, users are typically advised to write down their recovery phrase and keep it in a safe, offline location. These phrases are essential for restoring access to the wallet and its contents, which makes them a valuable target for cybercriminals.
Although taking a screenshot of a recovery phrase is strongly discouraged, some users still do it for convenience. Kaspersky’s latest report explains that SparkKitty collects all images from a device’s photo gallery, without filtering for specific types of content.
While the malware is believed to focus on stealing crypto wallet seed phrases, any sensitive images found could be misused for other purposes, including blackmail or extortion.
How SparkKitty Spreads
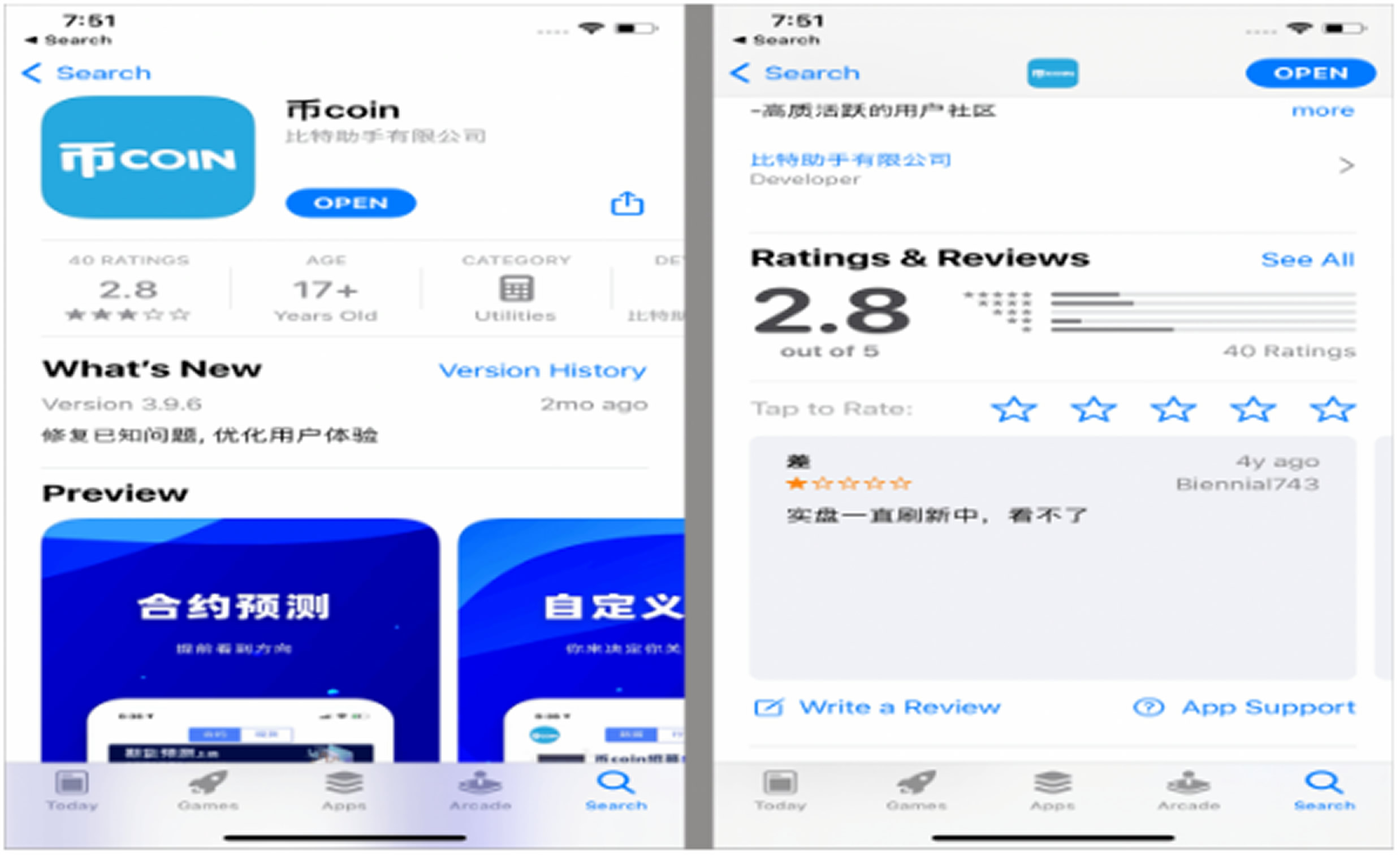
SparkKitty has been active since at least February 2024. It has spread through official app stores as well as third-party platforms. Kaspersky identified two malicious apps: 币coin on the Apple App Store and SOEX on Google Play. Both have since been removed.
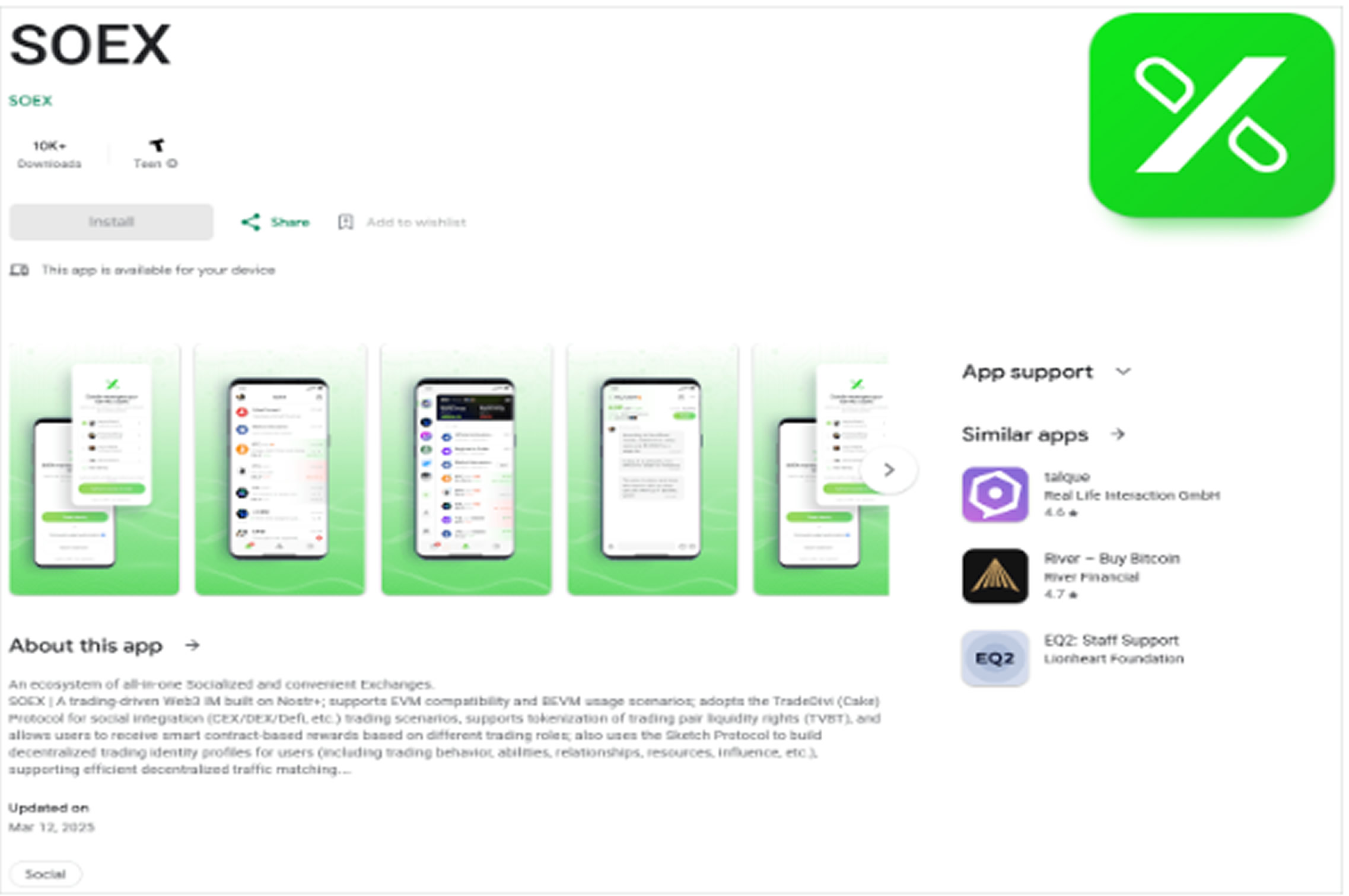
SOEX functioned as a messaging app with cryptocurrency exchange capabilities and had over 10,000 downloads before its removal. Kaspersky also found modified TikTok clones and apps related to gambling, adult content, and fake cryptocurrency services, all distributing SparkKitty through unofficial channels.
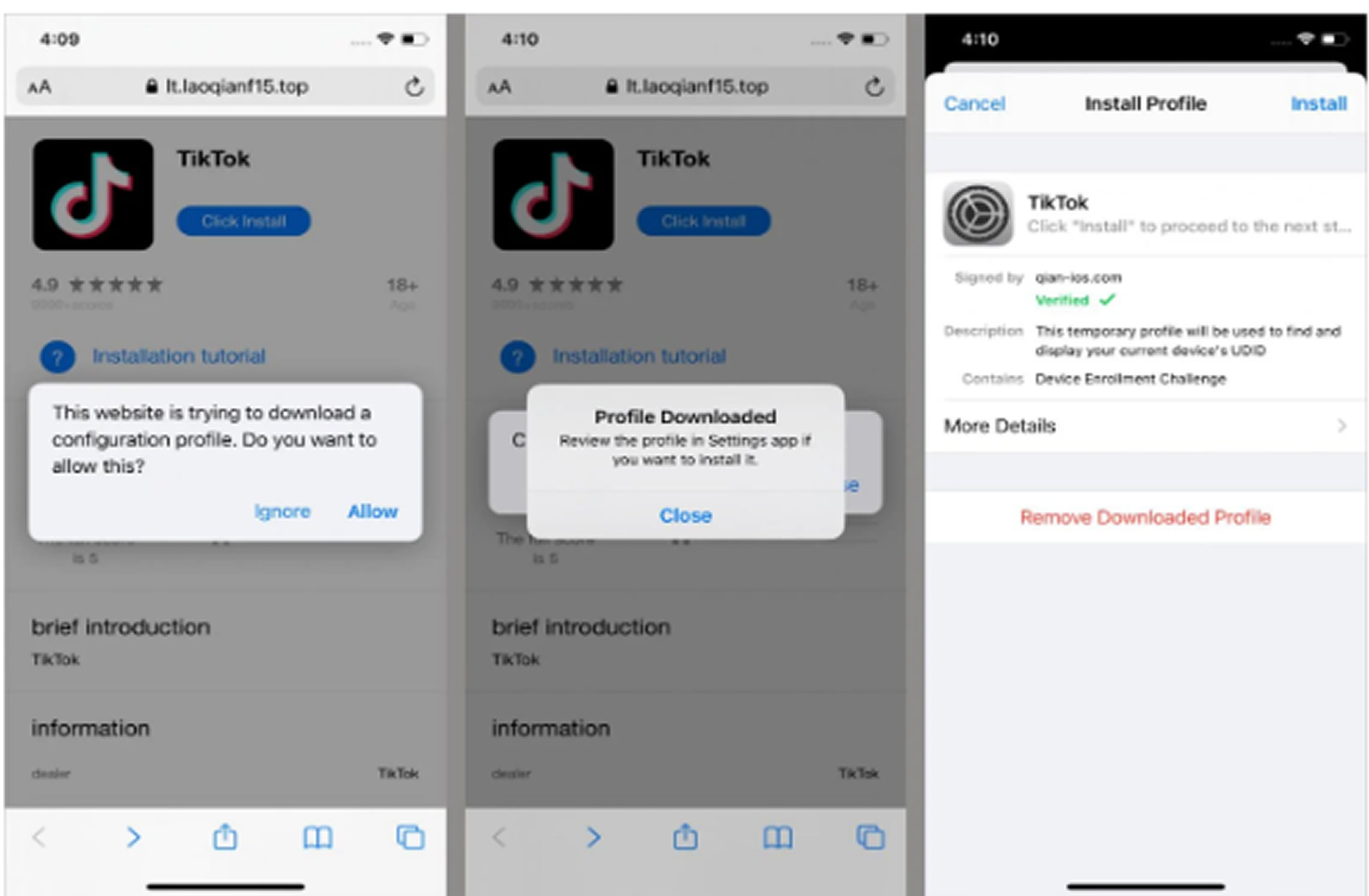
On iOS, SparkKitty is hidden within fake frameworks like AFNetworking.framework and libswiftDarwin.dylib, and sometimes delivered using enterprise provisioning profiles. On Android, the malware is bundled in Java or Kotlin apps, with some versions using harmful Xposed or LSPosed modules.
The iOS variant uses the Objective-C '+load' method to automatically run its code when the app is launched. It checks a configuration file within the app to determine whether it should activate.
On Android, SparkKitty activates either when the app starts or when a specific screen is accessed. Once active, it retrieves and decrypts a configuration file using AES-256 encryption in ECB mode to find command-and-control server addresses.
On iOS, the malware asks for access to the photo gallery. On Android, it requests storage permissions. If the user grants these permissions, SparkKitty proceeds to collect and upload images from the device’s gallery. Some versions use Google’s ML Kit OCR tool to identify and upload only images that contain text. The Android version also collects device identifiers and image metadata.
Protecting Against SparkKitty
SparkKitty is yet another example of malware reaching users through official app stores. This highlights the need for caution, even when downloading apps from trusted sources.
Users should be on the lookout for signs of fraudulent apps, such as unrealistic positive reviews, publishers with little or no reputation, or apps with few downloads but high ratings.
During installation, any requests for access to device storage or the photo gallery should be carefully reviewed. If the access is not essential for the app’s main features, it should be denied.
iOS users should avoid installing configuration profiles or certificates unless they are provided by a trusted source. Android users are encouraged to keep Google Play Protect enabled and to run regular full-device scans.
Cryptocurrency holders should never save photos of wallet seed phrases on their mobile devices. These phrases should always be stored offline in a secure location.
Google stated that the malicious app had been removed from the Play Store and that the developer has been banned. The company also noted that Android users are automatically protected by Google Play Protect, which is active by default on all devices with Google Play Services.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



