Russia-Linked Hackers Launch Sophisticated Cyberattack on Ukraine
Russia-backed cyber actors are once again targeting Ukraine, this time using upgraded tools and more discreet tactics aimed at infiltrating government systems.
Ukraine’s national Computer Emergency Response Team (CERT-UA) has linked a recent cyberattack on a government information and communication system to UAC-0001, also known as APT28 or Fancy Bear. This group is widely believed to operate under Russia’s GRU military intelligence agency. Between March and May 2024, investigators uncovered two new strains of malware named BEARDSHELL and SLIMAGENT, embedded in Ukrainian government systems. The attackers also used a component from the well-known COVENANT command and control framework, hidden inside a file titled “Act.doc” and shared through the encrypted messaging platform Signal.
Although the exact method of infection was unclear at first, further analysis revealed that the malware was delivered through a Word document containing macros. Once opened and enabled by the user, the document installed several hidden payloads designed to avoid detection, exploit trusted services, and maintain persistence using registry modifications and scheduled tasks.
Details of the Attack
The malware was disguised in a harmless-looking Word file sent over Signal. When a user enabled macros, the file executed code that saved two files on the system and created a registry modification to hijack explorer.exe.
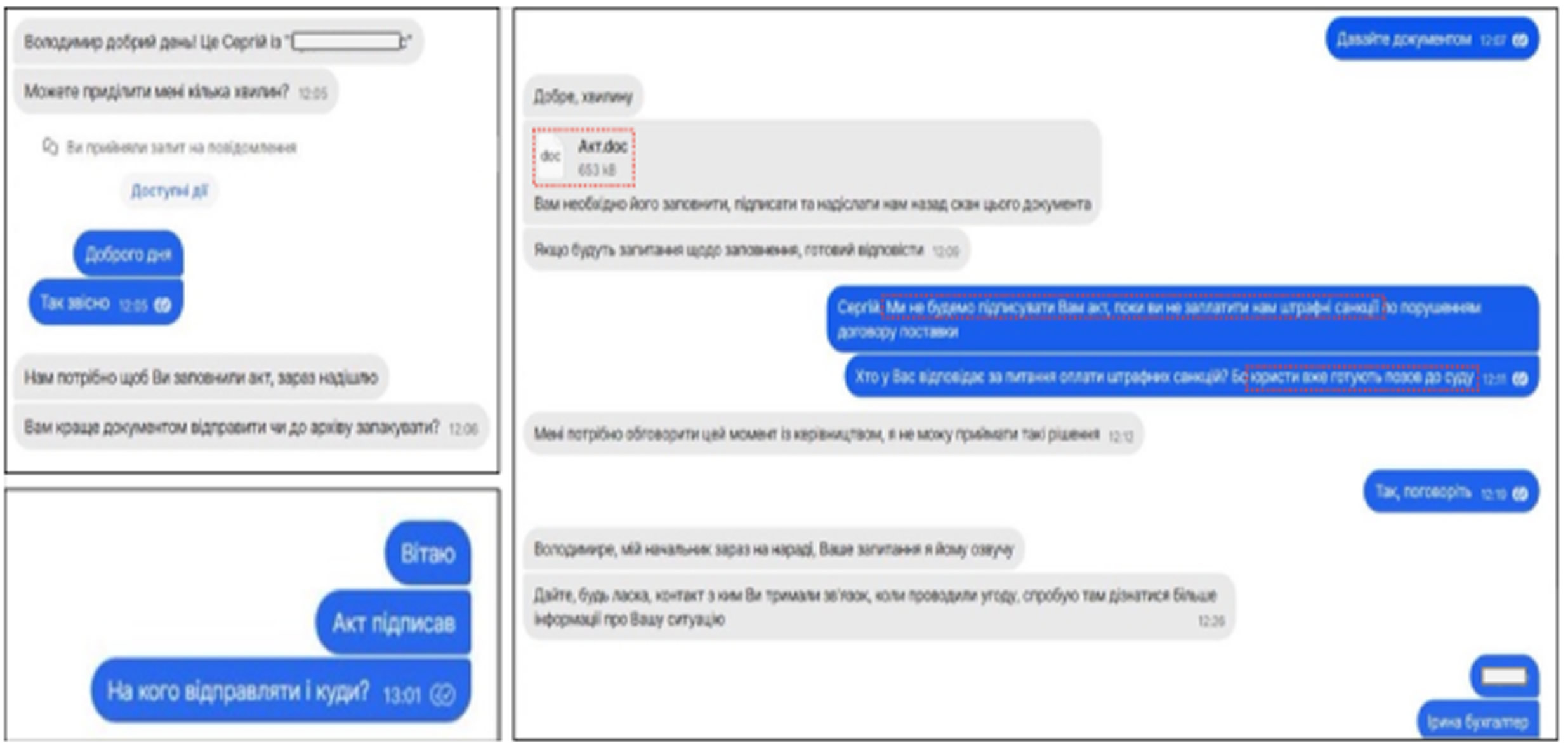
This change silently loaded a malicious DLL, which then decrypted another file named windows.png. That file contained shellcode that activated the COVENANT framework without displaying any visible signs to the user.
COVENANT, a red team tool built with .NET and commonly used during post-exploitation phases, was used to download PlaySndSrv.dll and a WAV file called sample-03.wav. This audio file carried encoded instructions that triggered the launch of BEARDSHELL, a custom-built backdoor.
What the Malware Can Do
Both BEARDSHELL and SLIMAGENT were written in C++ and serve different surveillance functions.
BEARDSHELL communicates with attackers using the API of Icedrive, a legitimate cloud storage service. It receives encrypted PowerShell commands and sends stolen data without alerting traditional security tools. Each infected system is assigned a unique directory based on a hash of its hardware and system identifiers.
SLIMAGENT captures screenshots at intervals, encrypts them with AES and RSA, and stores them locally with time-stamped file names. This tool quietly records on-screen activity without alerting the user.
One of the most concerning aspects of both tools is their use of legitimate services such as Icedrive and Koofr for communication. These services help the malware avoid detection because they do not raise suspicion in the same way as suspicious domains or IP addresses.
Why This Matters
This incident is not just another cyberattack. It reflects Russia’s ongoing hybrid warfare strategy that combines traditional conflict with cyber operations. Since the start of its invasion of Ukraine, Russia has repeatedly used cyberattacks to target national infrastructure. APT28 has been linked to several high-profile operations including the 2016 Democratic National Committee email leaks, the Olympic Destroyer attack in 2018, and cyber campaigns against NATO and European Union institutions.
The group’s approach has become more refined. Rather than forcing their way into systems, they now rely on phishing documents, encrypted messaging apps, and legitimate APIs to deliver and control malware. Their targets continue to be critical institutions within government systems.
CERT-UA confirmed that the malware was discovered inside the network of a central government executive body, suggesting that attackers are focused on high-level government targets.
How to Respond
CERT-UA is urging security teams, especially those working within government and critical infrastructure, to monitor network traffic to app.koofr.net and api.icedrive.net. These domains are being used as command-and-control channels by the attackers.
The agency also pointed out several key issues that contributed to the success of the attack:
- Users enabled macros in Office documents
- Endpoint protection tools failed to detect payloads delivered through Signal
- Attackers used legitimate platforms such as Icedrive and Koofr as covert communication channels
This incident serves as another reminder that modern malware is designed to hide in plain sight. It uses common applications, cloud services, and system settings to avoid detection. Organizations must move beyond static defenses and adapt their security strategies to handle these advanced threats
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



