Phishing campaign has recently shifted its focus to Mac users
A sophisticated phishing campaign has recently shifted its focus to Mac users, highlighting the evolving nature of cyber threats in response to enhanced security measures. This shift demonstrates how cybercriminals continuously adapt their tactics to bypass new defenses.
Previously, the attack targeted Windows users by impersonating Microsoft security alerts. Now, the same deceptive techniques are being used against Apple’s ecosystem. The campaign aims to steal user credentials by convincing victims that their computers have been compromised and locked. Simultaneously, malicious code freezes the webpage, creating the illusion that the entire system is unresponsive.
This trick pressures users into entering their credentials, which are then captured by the attackers. Researchers at LayerX Labs discovered this strategic pivot within just two weeks of Microsoft introducing new anti-phishing defenses in February 2025.
The security team noted a drastic 90% decline in Windows-focused attacks following the introduction of new “anti-scareware” features in Edge, Chrome, and Firefox browsers. As a result, hackers redirected their efforts toward Mac users, who lacked similar protections.
“This attack campaign underscores two critical points: Mac and Safari users are now prime targets, and cybercriminals are highly adaptable,” stated the LayerX research team. The persistence of this campaign reinforces the ongoing battle in cybersecurity, where attackers continuously refine their strategies to outmaneuver new defenses.
Infection Mechanism
The infection begins when victims attempt to visit legitimate websites but mistype URLs, unknowingly landing on compromised domain parking pages. These pages then redirect users to phishing sites hosted on Microsoft’s Windows.net platform, adding a layer of credibility to the attack.
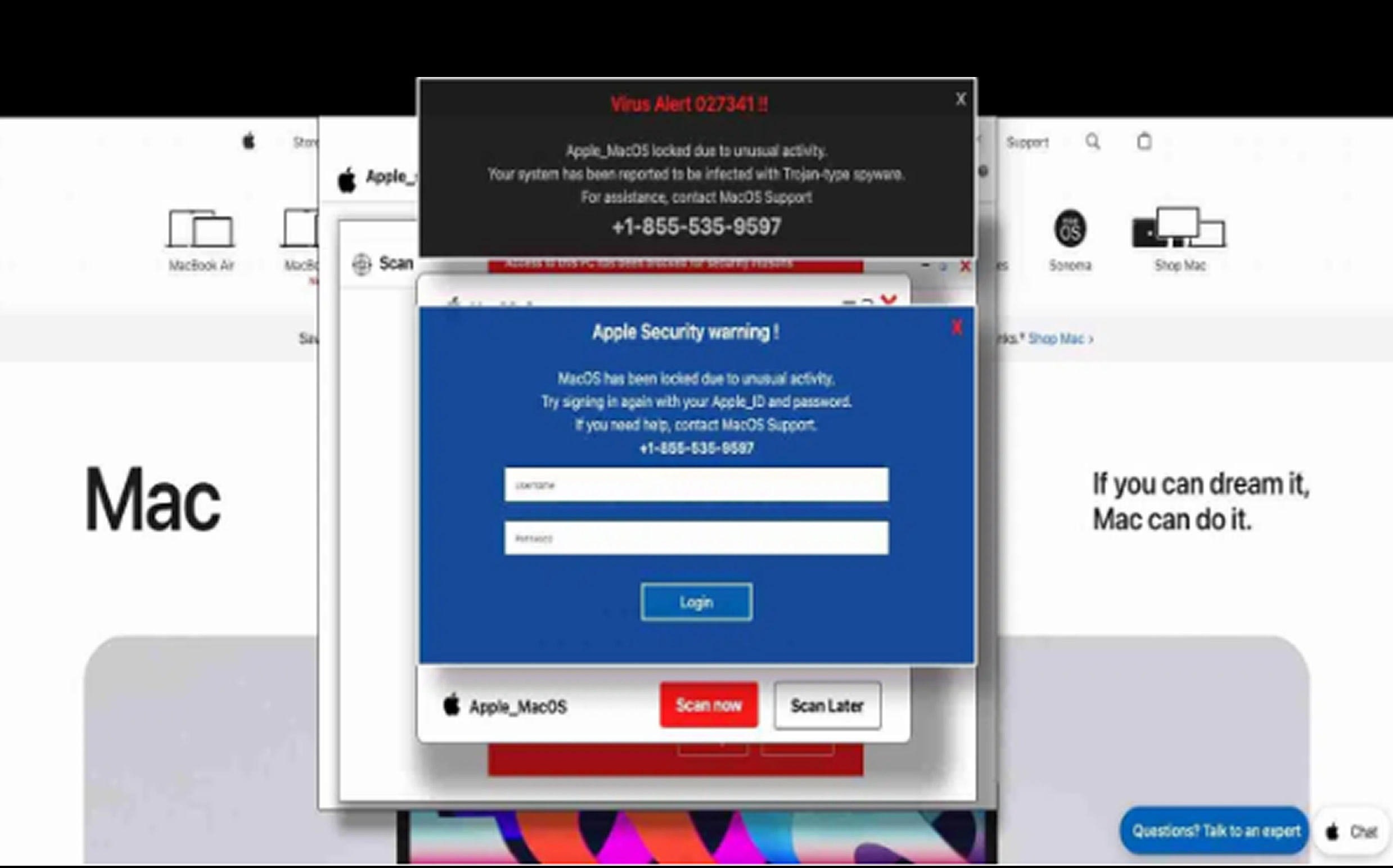
To effectively deceive Mac users, the phishing pages have been redesigned with code adjustments that specifically target macOS and Safari by leveraging HTTP OS and user agent parameters.
A key factor contributing to this campaign’s success is its use of randomized, frequently changing subdomains under the reputable Windows.net domain. This technique helps bypass traditional security mechanisms, such as Secure Web Gateways (SWGs), which assess website risk based on domain reputation.
Despite enterprise security measures, this attack has managed to evade conventional defenses, emphasizing the need for advanced browser-level security solutions capable of analyzing web page behavior in real time. The attack follows a familiar pattern, with compromised websites displaying fake security alerts that falsely claim the user’s system has been compromised.
Found this article interesting? Follow us on X(Twitter) and FaceBook to read more exclusive content we post.