Security Flaws in Appsmith Expose Critical Vulnerabilities, Including Remote Code Execution
Security researchers have identified multiple critical vulnerabilities in Appsmith, a widely used open-source developer platform for building internal applications.
The most severe flaw, tracked as CVE-2024-55963, enables unauthenticated attackers to execute arbitrary system commands on servers running default installations of Appsmith versions 1.20 through 1.51.
CVE-2024-55963 – Remote Code Execution via PostgreSQL
Appsmith provides organizations with tools to develop dashboards, admin panels, and customer support applications. By default, it includes a local PostgreSQL database for testing and learning purposes.
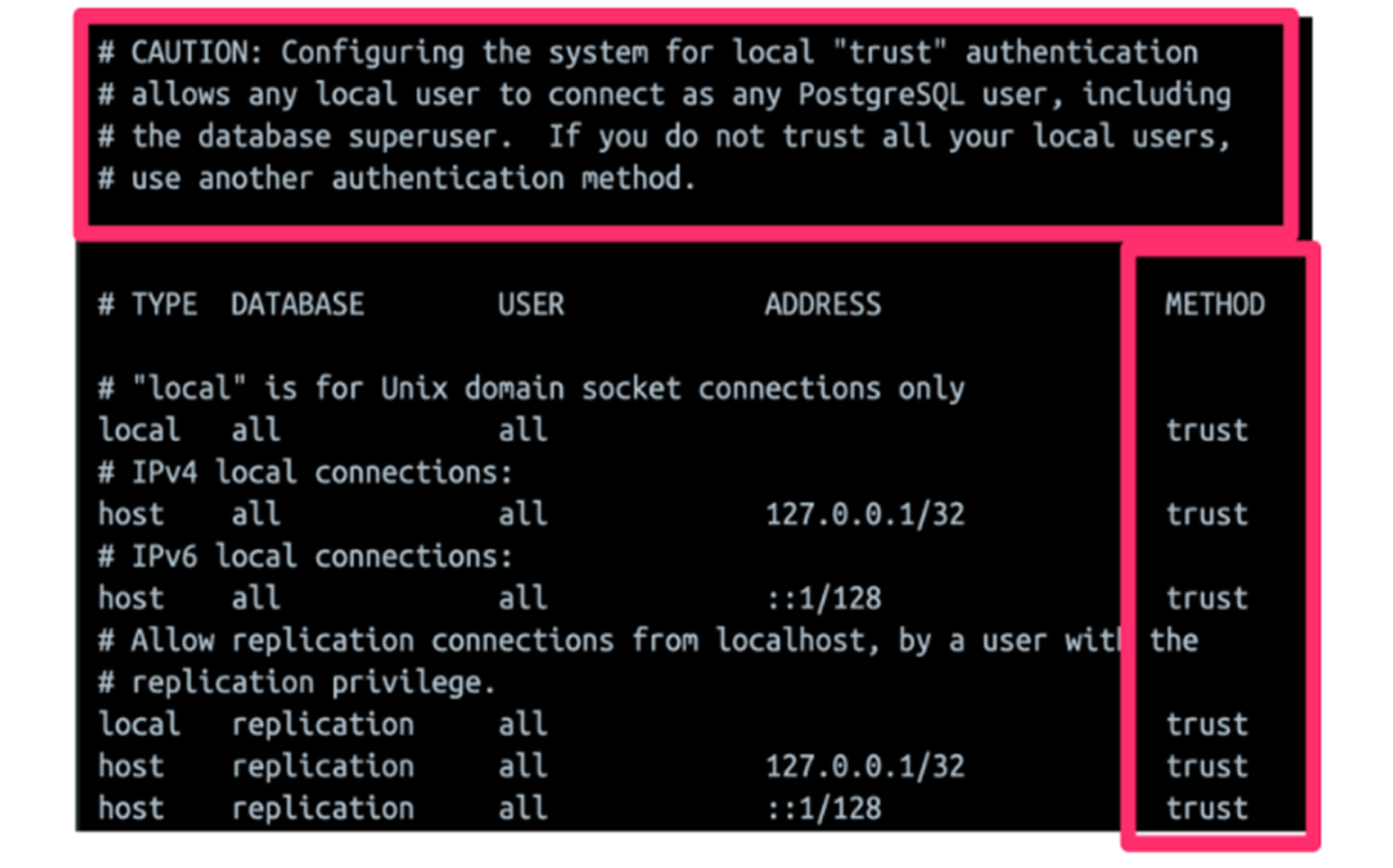
However, researchers at Rhino Security Labs found a critical misconfiguration in this default installation. The pg_hba.conf file—responsible for managing authentication in PostgreSQL—was set up in a way that allowed any local user to connect as any PostgreSQL user without requiring authentication.
This misconfiguration became an exploitable vulnerability because Appsmith’s default settings permit new user registrations. An attacker could:
- Sign up for an account
- Create a workspace and a new application
- Connect to the insecure local PostgreSQL database
- Use PostgreSQL’s COPY FROM PROGRAM function to execute system commands with PostgreSQL user privileges
Technical Exploitation Path
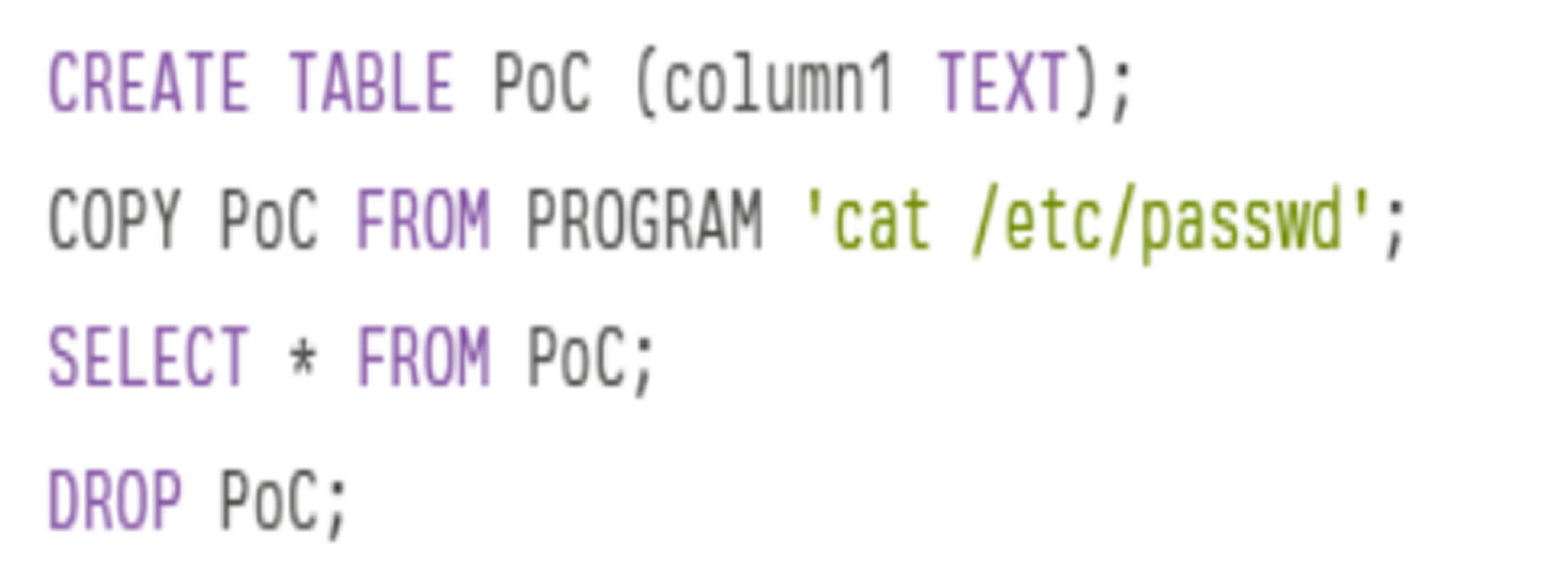
Researchers demonstrated a proof-of-concept attack where a simple SQL command sequence allowed them to:
- Create a temporary table
- Run the Unix cat command to read system files
- Retrieve the output
- Erase traces by dropping the table
Additional Security Vulnerabilities
Beyond CVE-2024-55963, the security audit uncovered two other serious vulnerabilities:
CVE-2024-55964 – Insecure Direct Object Reference (IDOR)
- Allowed users with minimal App Viewer permissions to access SQL databases
- Attackers could exploit predictable datasource IDs via the /api/v1/datasources/[datasource-id]/schema-preview API endpoint
CVE-2024-55965 – Denial of Service (DoS)
- Enabled low-privilege users to force application restarts repeatedly
- Exploited broken access controls in the restart API
Security Risks and Potential Impact
The combination of these vulnerabilities posed a major security threat to organizations using Appsmith. The most critical flaw, CVE-2024-55963, could allow an unauthenticated attacker to:
- Register a new user account
- Create a workspace and an application
- Connect to the local PostgreSQL database
- Execute arbitrary system commands
- Maintain persistent access to the server
Patches and Mitigation
Appsmith collaborated with Rhino Security Labs to fix all three vulnerabilities:
- CVE-2024-55963 (Remote Code Execution) – Fixed in version 1.52 (PR #37068), which reinforced PostgreSQL security and implemented password-based authentication.
- CVE-2024-55964 (IDOR) – Resolved in version 1.49 (PR #37308), adding stricter role-based access controls.
- CVE-2024-55965 (Denial of Service) – Addressed in version 1.48 (PR #37227), implementing proper access control checks.
Organizations using Appsmith should immediately update to version 1.52 or later to mitigate these risks.
Security researchers have also released detection tools, including Nuclei templates, to help identify vulnerable instances.
Found this article interesting? Follow us on X(Twitter) and FaceBook to read more exclusive content we post.


