Cybersecurity Researchers Uncover Phishing Attacks Using SVG Files to Deliver Malicious HTML
Cybersecurity experts have uncovered a sophisticated phishing technique that abuses SVG (Scalable Vector Graphics) files to sneak malicious HTML content past security filters and trick users into disclosing sensitive information.
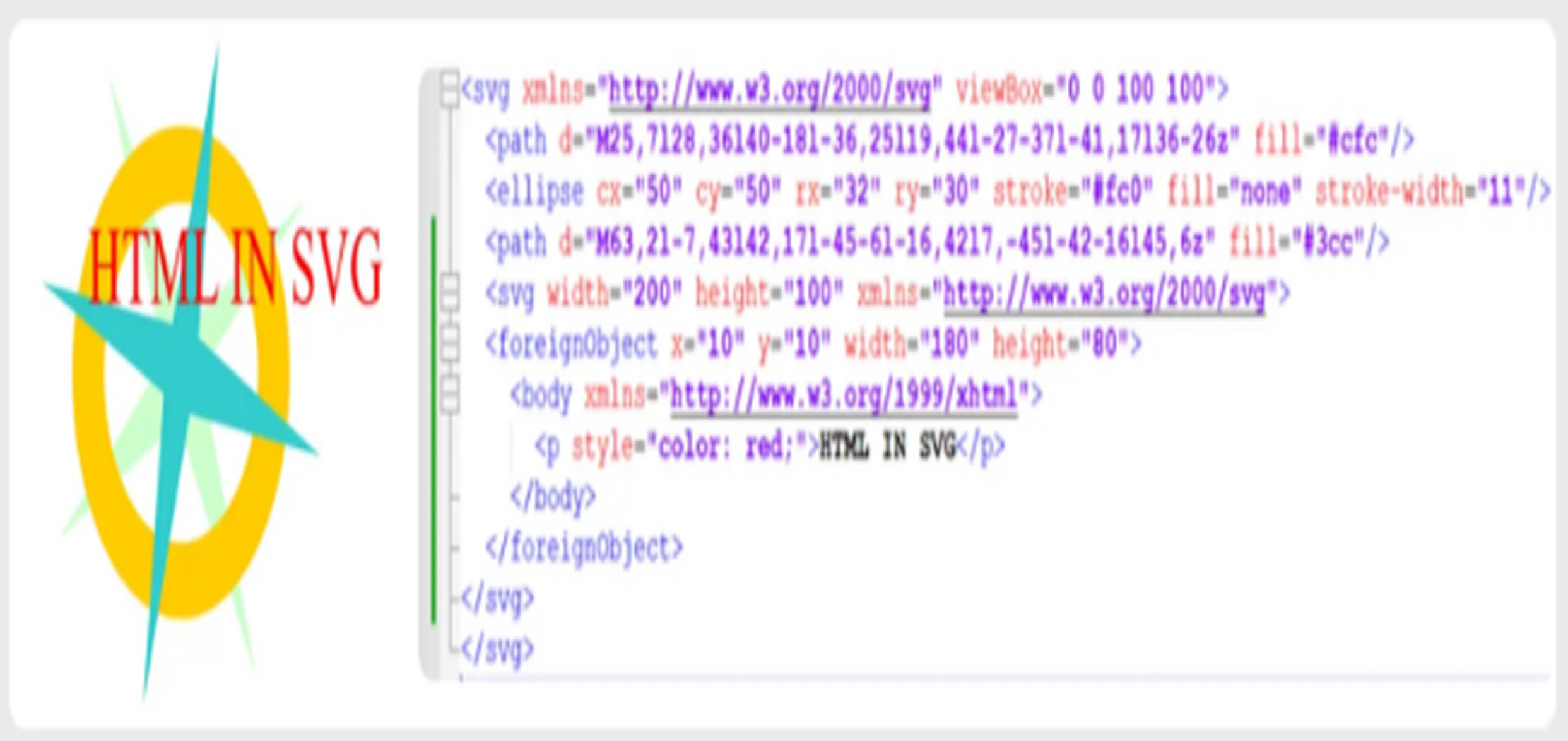
First spotted in early 2025, the tactic marks a shift in phishing strategies by exploiting the dual-purpose nature of SVG files. Unlike standard image formats like JPEG or PNG, SVGs are XML-based and support embedded JavaScript and HTML—features designed for interactivity, but now being turned against users.
Attackers typically send phishing emails with SVG attachments disguised as documents or voice messages. When opened—often in a browser—the SVG executes embedded JavaScript or HTML code, either displaying fake login pages or redirecting users to phishing sites that mimic legitimate services like Google Voice or Microsoft.
Securelist researchers noted a sharp rise in such attacks, identifying 2,825 malicious emails with SVG attachments in Q1 2025, and 1,324 more just in the first two weeks of April—signaling growing adoption of the method.
Deceptive but Effective Technique
Despite their image-like appearance, these malicious SVGs often contain minimal graphic code. Instead, they are loaded with scripts that trigger on opening, displaying fully self-contained phishing pages or connecting to external credential-stealing sites.
What makes this attack especially dangerous is its ability to bypass traditional email security filters. Since SVG files are treated as images and labeled with the MIME type image/svg+xml, they often go undetected by systems that block known executable or HTML file types.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.


