Cybercriminals Exploit Google Sites Flaw to Launch Stealthy Phishing Attacks
Threat actors are exploiting a vulnerability in Google Sites to send phishing emails that can bypass standard email authentication protocols.
In this campaign, attackers send emails that appear to come from legitimate Google no-reply addresses, directing victims to Google Sites pages that closely resemble official Google login pages.
Ethereum Foundation developer Nick Johnson and EasyDMARC CEO Gerasim Hovhannisyan flagged the attacks, which abuse weaknesses in Google Sites—a legacy service that lets users create custom pages under the trusted sites.google.com domain.
Because the phishing pages are hosted on a Google-owned domain, they inherit Google’s SSL certificates and brand credibility, making the scams appear legitimate and capable of bypassing validation and trust checks.
The attackers initiate the scheme by registering a website and creating an associated account. They then forward a genuine Google email without altering content or headers protected by DomainKeys Identified Mail (DKIM) signatures, allowing the email to evade authentication filters.
In Johnson's case, the phishing attempt came from an account named me@[attacker domain] and used a Google OAuth app where the app name was the phishing message itself. The forwarded security alert email retained its DKIM validation, making it appear authentic and even placing it in the same conversation thread as real alerts.
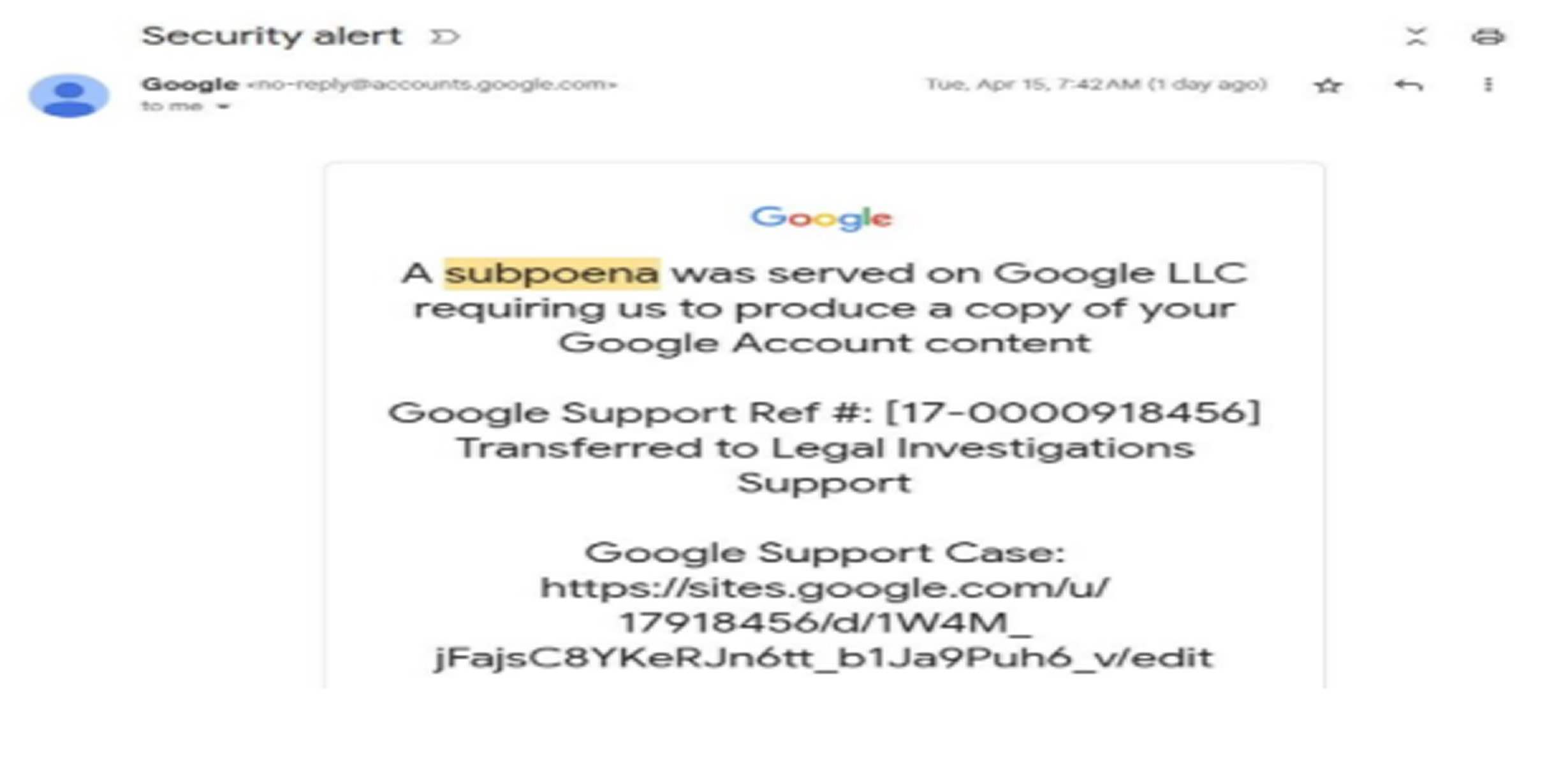
Because Gmail recognized the sender’s name as “me@”, it misleadingly displayed the email as sent “to me”, mimicking Google’s usual email display for personal alerts.
Johnson noted that Google initially labeled the OAuth misuse as “working as intended” but later agreed to address the issue following further reports.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.


