Cybersecurity researchers have uncovered an "auto-propagating" cryptocurrency mining botnet known as Outlaw (or Dota),
which targets SSH servers with weak security. This malware, active since at least late 2018, is used by a hacking group also called Outlaw and believed to be of Romanian origin, to gain control over systems. Other groups involved in cryptojacking include 8220, Keksec, Kinsing, and TeamTNT.
The Outlaw malware infects Linux systems using SSH brute-force attacks and spreads like a worm to maintain control. The attackers gain access, conduct reconnaissance, and ensure continued access by adding their own SSH keys. The infection process involves a dropper script to download and unpack a file that launches the miner, while also removing traces of previous intrusions and competing miners.
This malware uses an initial access component (BLITZ) to self-propagate by scanning for vulnerable SSH services. The brute-force module retrieves target lists from a command-and-control (C2) server. Some attacks have exploited vulnerabilities in Linux and Unix systems (CVE-2016-8655, CVE-2016-5195) and targeted systems with weak Telnet credentials. After gaining access, SHELLBOT is deployed for remote control via a C2 server, enabling command execution, payload downloads, DDoS attacks, credential theft, and data exfiltration.
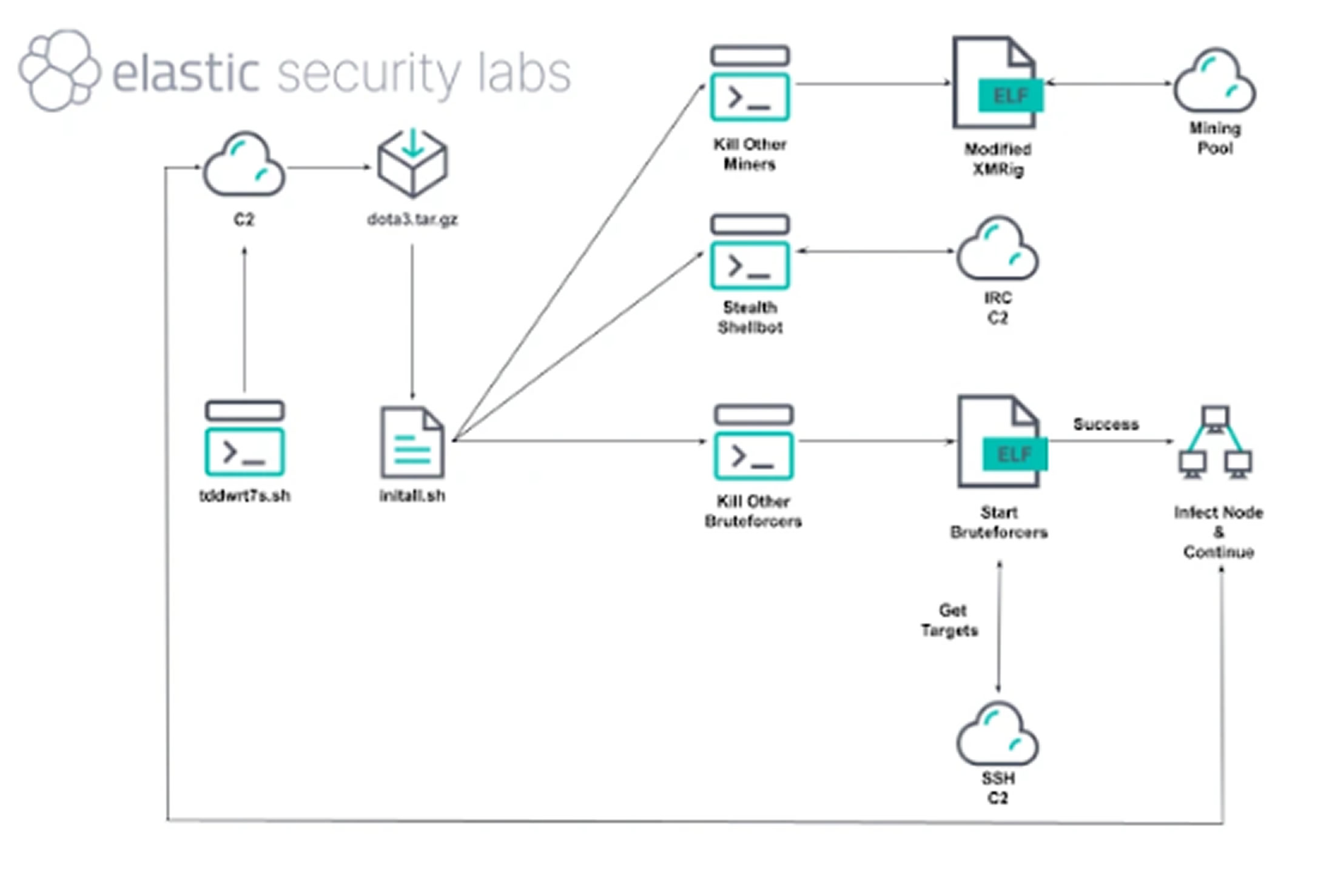
For mining, the malware identifies the system's CPU and uses hugepages to improve memory access. It also uses a binary called kswap01 for persistent communication with the attacker's infrastructure. Despite using basic techniques, Outlaw remains active, employing modified XMRig miners, IRC for C2, and publicly available scripts for persistence and defense evasion.
Found this article interesting? Follow us on X(Twitter) and FaceBook to read more exclusive content we post.


