PoisonSeed Campaign Exploits CRM Credentials to Launch Crypto Wallet Attacks
A new malicious campaign known as PoisonSeed is exploiting compromised login credentials from customer relationship management (CRM) platforms and bulk email service providers to distribute spam messages designed to steal cryptocurrency from victims.
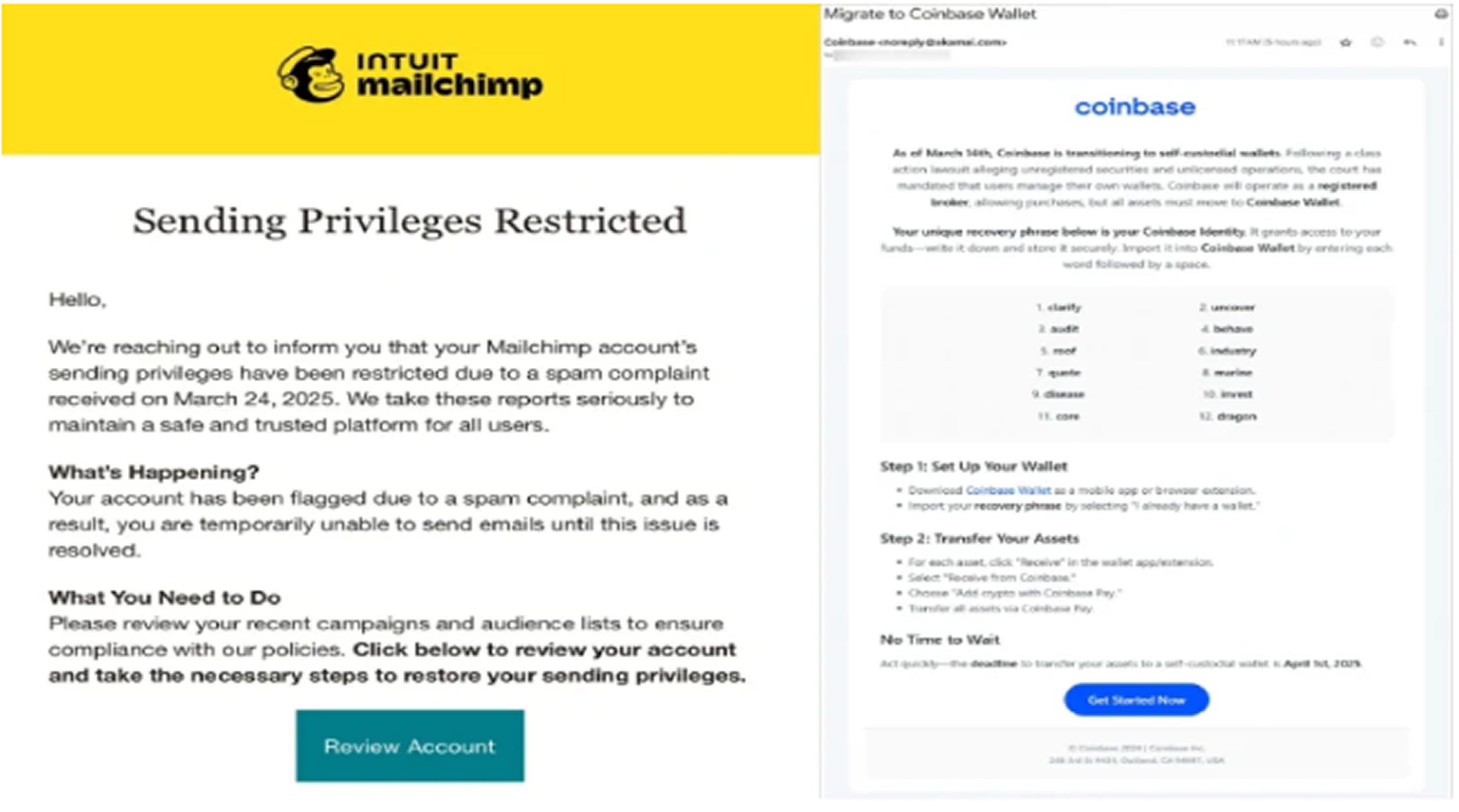
According to an analysis by Silent Push, the attackers target recipients with a seed phrase poisoning tactic. Victims are lured into copying and pasting fake cryptocurrency seed phrases into newly created wallets, unwittingly giving the attackers access to them.
The campaign does not limit itself to crypto-savvy users; both individuals and organizations outside the crypto industry are being targeted. High-profile companies such as Coinbase, Ledger, Mailchimp, SendGrid, Hubspot, Mailgun, and Zoho have been impersonated or targeted through this operation.
While PoisonSeed exhibits some overlap with known cybercrime groups like Scattered Spider and CryptoChameleon, notably through reused infrastructure like the spoofed domain mailchimp-sso[.]com, the phishing toolkit used in this campaign appears distinct, suggesting either a new threat actor or a fresh tool developed by an existing one.
How the Attack Works
- Phishing for CRM Credentials: Attackers deploy fake login pages mimicking trusted CRM and email platforms to steal login credentials.
- Persistence via API Keys: After gaining access, they generate API keys to maintain control, even if passwords are later changed.
- Bulk Email Abuse: Compromised accounts are used to export mailing lists and send spam emails embedded with fraudulent seed phrases.
- Crypto Wallet Hijack: Victims who set up wallets using the provided seed phrases end up losing their funds to the attackers.
Broader Threat Landscape
This campaign is part of a larger cybercrime ecosystem and coincides with other active threats. For instance, a Russian-speaking threat actor has been seen using Cloudflare-branded phishing pages hosted on Pages.Dev and Workers.Dev to deliver malware. These attacks disguise malicious LNK files as PDFs using double extensions. When executed, the malware communicates with a Telegram bot and later connects to Pyramid C2, allowing remote control of the infected system.
According to Hunt.io, this newer campaign leverages fake DMCA takedown notices as a phishing lure, further broadening the range of deception tactics currently in circulation.


