The Russian-speaking cybercriminal group RedCurl has been linked to a ransomware campaign
for the first time, marking a significant shift in its tactics. This new activity, uncovered by Romanian cybersecurity firm Bitdefender, involves the deployment of a previously unseen ransomware strain named QWCrypt.
RedCurl, also known as Earth Kapre and Red Wolf, has historically focused on corporate espionage, targeting organizations in Canada, Germany, Norway, Russia, Slovenia, Ukraine, the United Kingdom, and the United States. Active since at least November 2018, the group was previously known for using spear-phishing emails with Human Resources (HR)-themed lures to initiate malware infections. Earlier this year, Huntress reported attacks in Canada where RedCurl deployed a loader known as RedLoader, which had simple backdoor capabilities.
More recently, eSentire revealed that RedCurl had been using phishing emails with malicious PDF attachments disguised as CVs and cover letters. These emails exploited the legitimate Adobe executable “ADNotificationManager.exe” to sideload their loader malware. Bitdefender’s latest findings indicate that the attackers have continued this approach, now using mountable ISO files masquerading as CVs to initiate a multi-stage infection process. These files contain a Windows screensaver (SCR) file that, in reality, is the ADNotificationManager.exe binary. Once executed, it triggers DLL side-loading to deploy the loader (“netutils.dll”).
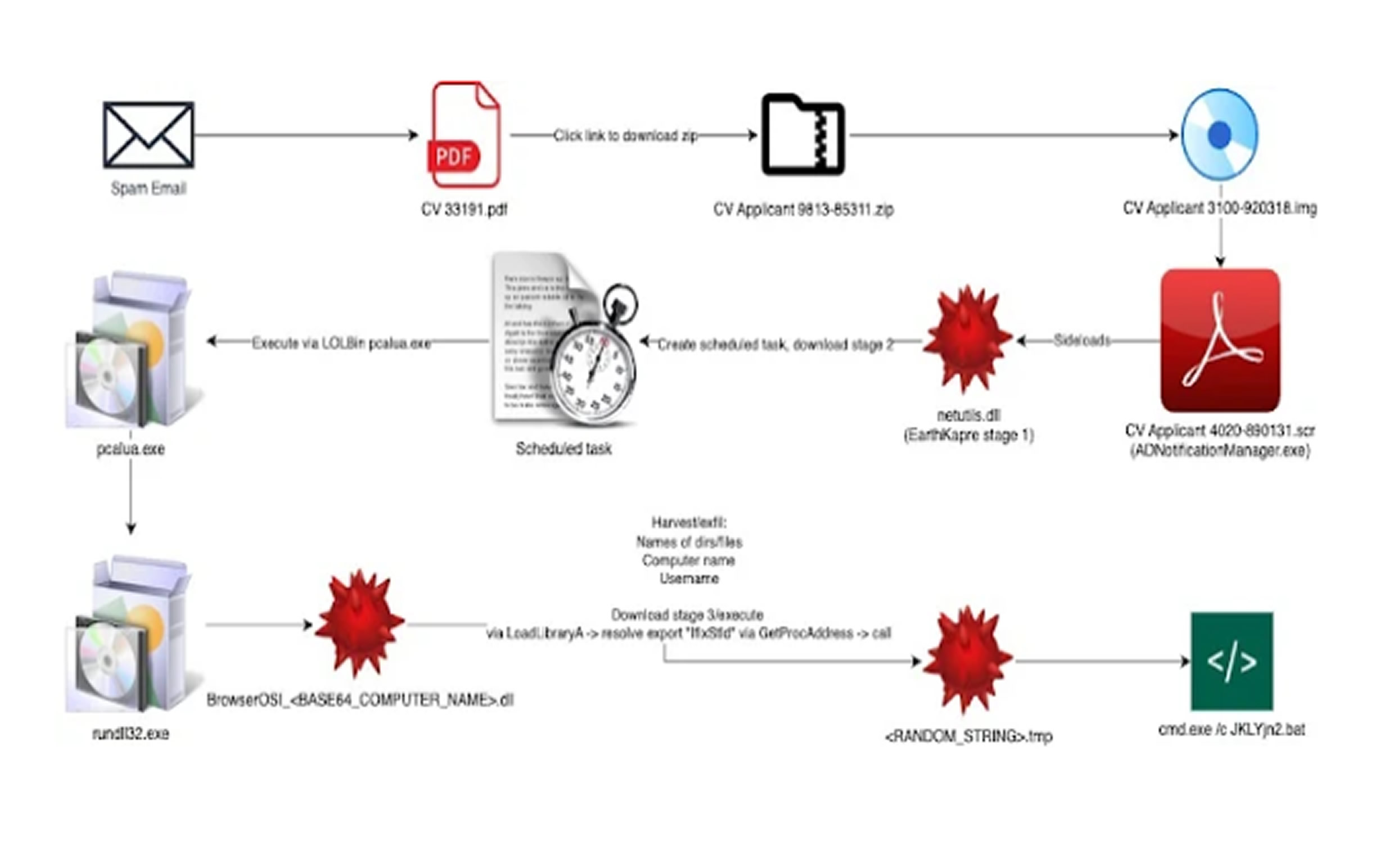
The malware then launches the victim’s web browser to a legitimate Indeed login page, creating a distraction while the malicious code operates in the background undetected. The loader also downloads a next-stage backdoor DLL and establishes persistence through a scheduled task. Once installed, this backdoor facilitates lateral movement, enabling the attackers to navigate networks, gather intelligence, and escalate their access privileges.
In a significant departure from its usual espionage-focused activities, RedCurl was observed deploying ransomware in at least one attack. The group appears to have strategically targeted virtual machines on hypervisors, encrypting them to render the entire virtualized infrastructure unbootable, thereby disrupting all hosted services. This tactic suggests an intent to cause maximum operational damage with minimal effort.
The ransomware executable also employs the "bring your own vulnerable driver" (BYOVD) technique to disable endpoint security software. Before launching the encryption process, it gathers system information, ensuring a more effective attack. The ransom note left behind draws inspiration from multiple ransomware groups, including LockBit, HardBit, and Mimic.
Interestingly, RedCurl has not been linked to any dedicated leak site (DLS), leaving it unclear whether the ransom demands are genuine or merely a diversion. The repurposing of existing ransom note text further raises questions about the group's evolving motivations and potential collaboration with other cybercriminal entities.
Found this article interesting? Follow us on X(Twitter) and FaceBook to read more exclusive content we post.