Sophisticated cyberattack campaign linked to the North Korean Advanced Persistent Threat (APT)
A sophisticated cyberattack campaign linked to the North Korean Advanced Persistent Threat (APT) group Kimsuky has been observed employing new tactics and malicious scripts to enhance stealth and efficiency.
The attack is centered around a ZIP file containing multiple components designed to steal sensitive information while evading detection. It begins with obfuscated scripts that eventually deploy a keylogger and a cryptocurrency information stealer.
The initial payload consists of four files: a heavily obfuscated VBScript (1.vbs), a PowerShell script (1.ps1), and two encoded text files (1.log and 2.log) containing the actual malware components. These files work together to establish persistence, avoid detection, and exfiltrate stolen data to a command-and-control server located at “hxxp://srvdown[.]ddns.net/service3/.”
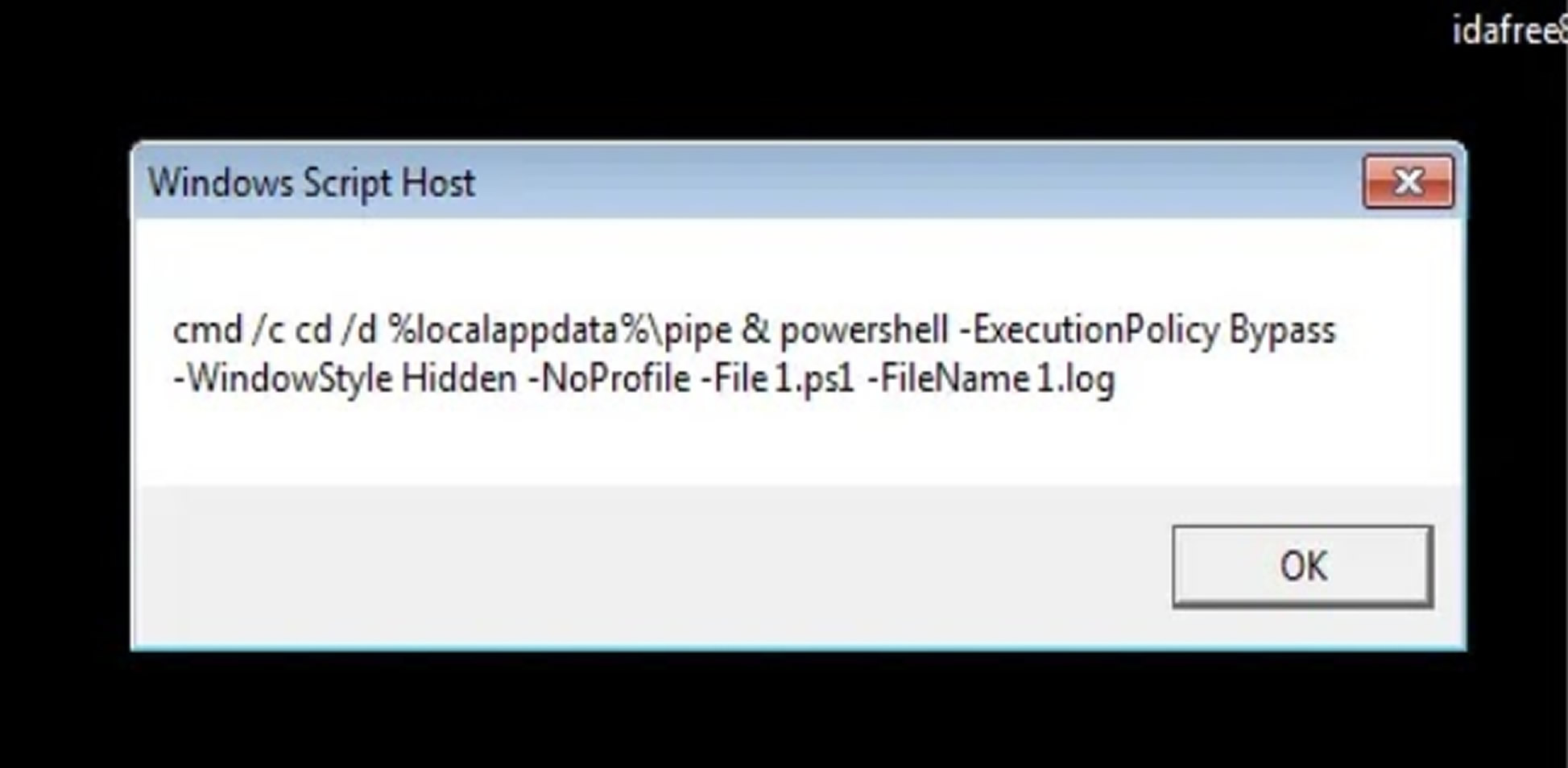
Researchers at K7 Security Labs found that the VBScript employs advanced obfuscation techniques, using the chr() and CLng() functions to dynamically generate characters and execute commands. This approach helps the script bypass signature-based detection methods before launching the PowerShell component.
Once executed, the malware collects the BIOS serial number of the compromised system and creates a dedicated directory within the system’s temp folder. It also checks for the presence of a VMware environment, terminating execution if detected—demonstrating its built-in anti-analysis capabilities.
The malware specifically targets browser data from Edge, Firefox, Chrome, and Naver Whale, focusing on cryptocurrency wallets. It establishes persistence through task scheduling and continuously monitors keystrokes and clipboard content to capture sensitive information, such as passwords and crypto keys.
The keylogger component records special key presses and window titles, providing attackers with contextual insights into the victim’s activities. Periodically, all collected data is transmitted to the attacker’s server, enabling Kimsuky operators to maintain surveillance over their targets while stealing valuable credentials and cryptocurrency assets.
Found this article interesting? Follow us on X(Twitter) and FaceBook to read more exclusive content we post.


