Cybercriminal Groups Exploit Fake Celebrity Endorsements and Cloaking Systems to Run Investment Scams
Cybersecurity researchers have uncovered two malicious threat actor groups named dubbed Reckless Rabbit and Ruthless Rabbit that are orchestrating sophisticated investment scams using fake celebrity endorsements and traffic distribution systems (TDS) to mask their operations.
According to DNS threat intelligence firm Infoblox, these threat actors lure victims through fraudulent platforms including counterfeit cryptocurrency exchanges, which are heavily promoted on social media. A key tactic involves harvesting victims’ personal data via embedded web forms.
Fake Ads, Celebrity Endorsements, and Data Harvesting
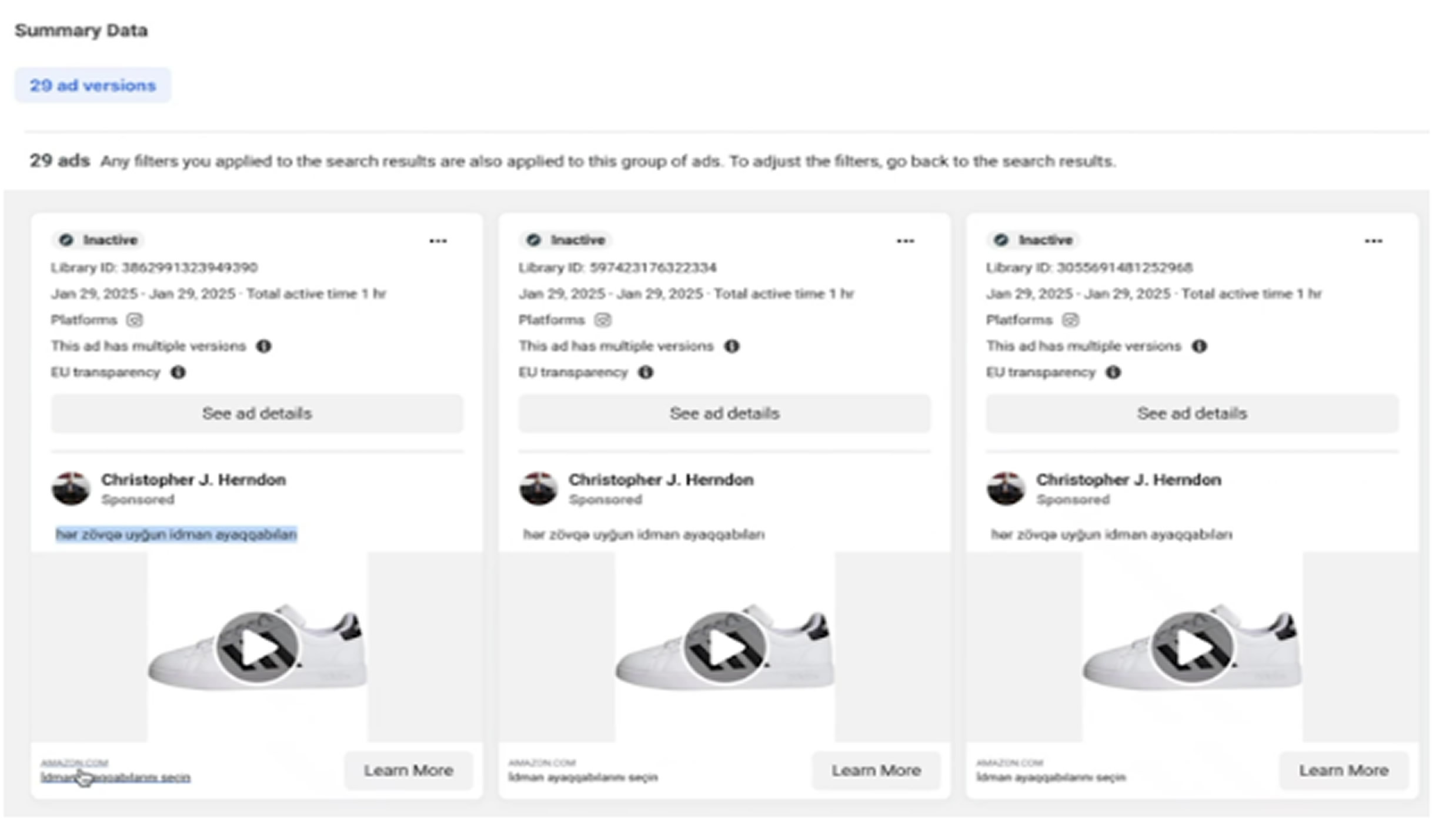
Reckless Rabbit is known for creating deceptive Facebook ads that link to fake news articles featuring fabricated celebrity endorsements. These articles encourage users to click through to fake investment platforms, where embedded forms collect personal details like names, email addresses, and phone numbers. Some even suggest auto-generating passwords, which are used in later stages of the scam.
To avoid wasting resources on ineligible targets, the scammers use IP validation services like ipinfo.io and ipgeolocation.io to filter out unwanted geographic locations. Only users who pass these validation checks are redirected via a TDS to scam sites or pages prompting them to await a follow-up call. Some campaigns utilize call centers to further convince victims to deposit funds.
TDS and Domain Tricks Enhance Evasion
The groups use a registered domain generation algorithm (RDGA) to systematically create domain names for their schemes. Unlike traditional domain generation algorithms, RDGAs employ secret logic for domain registration, making it harder to track. Reckless Rabbit has used this approach since at least April 2024, targeting users in Russia, Poland, and Romania while excluding traffic from various African and Asian nations.
To evade Facebook’s detection mechanisms, the ads mix scam links with innocuous content such as Amazon marketplace items and use of decoy display domains (like “amazon[.]pl”) that redirect to unrelated scam domains.
Ruthless Rabbit: Running Its Own Cloaking Service
Ruthless Rabbit has been linked to investment fraud campaigns dating back to November 2022, mainly focused on Eastern Europe. What distinguishes this group is its use of an in-house cloaking system, “mcraftdb[.]tech”, to perform validation before redirecting victims to fake investment sites where they are prompted to enter sensitive financial data.
According to Infoblox, TDS technology enables cybercriminals to build resilient infrastructures, effectively hiding their operations from security researchers and automated bots.
Scams Continue to Evolve and Multiply
This isn’t the first wave of such fraud. In December 2024, security firm ESET exposed a similar scam called Nomani, which used social media ads, AI-generated celebrity videos, and fake company branding to mislead users.
In another instance, Spanish authorities arrested six individuals in April 2025 for running a large-scale crypto scam using AI to produce deepfake celebrity endorsements.
Despite differences in execution, the tactics all rely on social engineering, deception, and the promise of financial gain to exploit victims.
Mystery Box Scams Also on the Rise
Separately, Bitdefender has raised the alarm over a surge in subscription-based “mystery box” scams. These campaigns involve fake websites and Facebook ads promoting seemingly legitimate deals from brands like Zara or Apple. Users are lured into entering credit card details for what appears to be a small one-time payment, only to be enrolled in hidden recurring subscriptions.
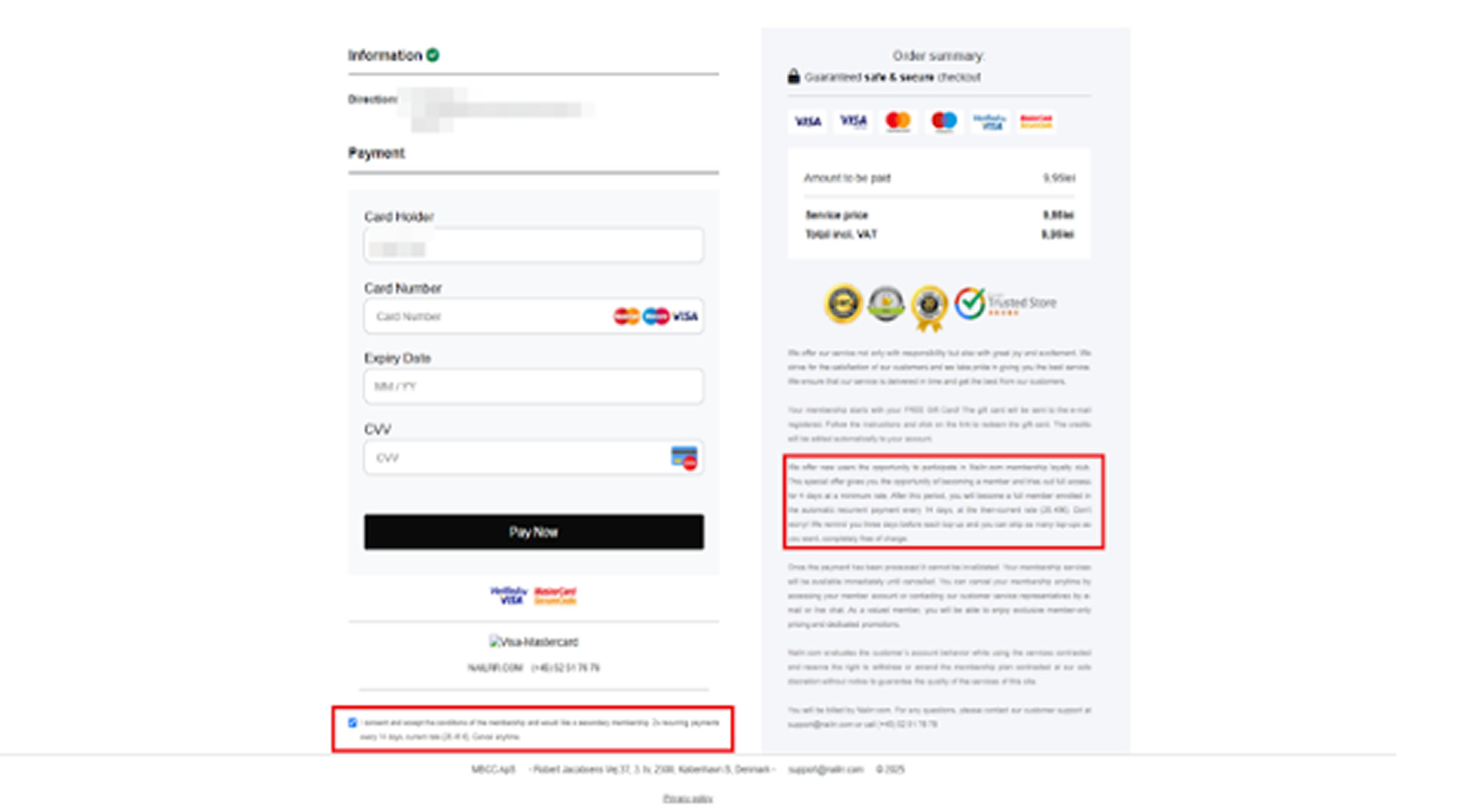
These scams also use multiple ad variations only one of which is harmful to evade detection. Victims are tricked with surveys to validate their identities before payment, mirroring tactics used by the Rabbit groups.
U.S. Sanctions Criminal Group Behind Scam Compounds
In a related crackdown, the U.S. Treasury has sanctioned the Myanmar-based Karen National Army (KNA) for facilitating multi-billion-dollar scam compounds linked to human trafficking and cross-border crime. The KNA allegedly profits by leasing land and providing support to scam operators, including security, smuggling routes, and utility services.
These compounds are reportedly run on an industrial scale, with trafficked workers forced to engage in “romance baiting” scams building online relationships with victims and persuading them to invest in bogus platforms.
Despite law enforcement efforts, the United Nations Office on Drugs and Crime estimates that these scam centers continue to thrive, generating as much as $40 billion annually.
The continued evolution and profitability of these scams indicate that cybercriminals like Reckless Rabbit and Ruthless Rabbit that are unlikely to stop. Their methods are becoming increasingly complex, blending social engineering, technical obfuscation, and targeted victim profiling to maximize financial gain while evading detection.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.


