Cybersecurity experts have revealed the operations of an initial access broker (IAB) known as ToyMaker
who has been providing system access to double extortion ransomware groups like CACTUS. Believed to be financially motivated, ToyMaker scans for vulnerable systems and uses a custom malware called LAGTOY (also referred to as HOLERUN).
"LAGTOY enables the creation of reverse shells and the execution of commands on compromised systems," said Cisco Talos researchers Joey Chen, Asheer Malhotra, Ashley Shen, Vitor Ventura, and Brandon White. This malware was initially reported by Mandiant, a Google-owned company, in March 2023 and attributed to a group tracked as UNC961, also known as Gold Melody or Prophet Spider.
ToyMaker exploits a range of known vulnerabilities in internet-facing applications to gain initial access. Within a week, they carry out reconnaissance, harvest credentials, and deploy LAGTOY. They also establish SSH connections to download a forensic tool called Magnet RAM Capture, likely to extract memory dumps and steal credentials.
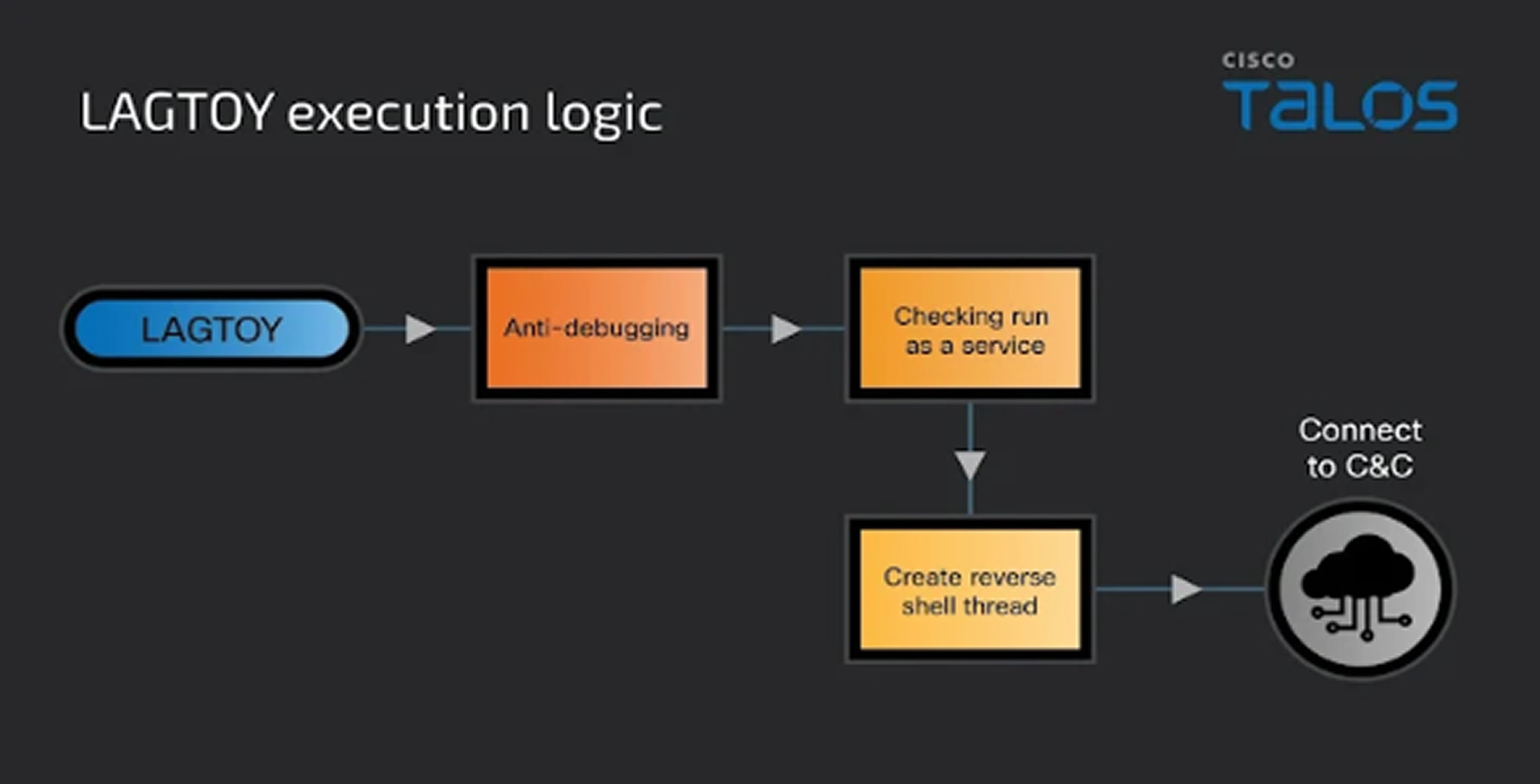
LAGTOY communicates with a hardcoded command-and-control (C2) server to receive further instructions, including creating processes and executing commands with specific user privileges. It handles three commands at a time with a sleep interval of 11 seconds between each.
"After a three-week pause, we observed CACTUS ransomware actors infiltrate the victim’s network using credentials stolen by ToyMaker," Talos noted. Due to the brief dwell time, absence of data theft, and the rapid handover to CACTUS, researchers believe ToyMaker was purely financially driven, with no espionage intent.
In the case analyzed, CACTUS affiliates conducted additional reconnaissance and persistence tactics before stealing data and encrypting systems. They used multiple tools to maintain long-term access, including OpenSSH, AnyDesk, and eHorus Agent.
Ultimately, Cisco Talos concludes, "ToyMaker is a financially motivated initial access broker who breaches high-value targets and sells that access to other attackers, typically leading to ransomware deployment and double extortion attacks."
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.


