New APT Group "Earth Kurma" Targets Southeast Asian Governments and Telecom Firms
Since June 2024, a newly identified advanced persistent threat (APT) group known as Earth Kurma has been targeting government and telecommunications sectors across Southeast Asia, according to Trend Micro researchers.
The group’s sophisticated campaign employs custom malware, kernel-level rootkits, and trusted cloud storage platforms like Dropbox and Microsoft OneDrive to exfiltrate sensitive data. Notable targets include organizations in the Philippines, Vietnam, Thailand, and Malaysia.
“This campaign presents a significant business threat due to its targeted espionage, credential theft, persistent access via rootkits, and covert data exfiltration through legitimate cloud services,” noted security researchers Nick Dai and Sunny Lu.
Earth Kurma's activity traces back to November 2020. Tools like TESDAT and SIMPOBOXSPY have been used for data theft, while rootkits such as KRNRAT and Moriya—previously seen in the TunnelSnake espionage campaign—bolster their toolkit. Although some overlaps have been found with another APT group, ToddyCat, conclusive attribution remains uncertain.
The method of initial access remains unclear, but once inside a network, Earth Kurma conducts lateral movement using tools like NBTSCAN, Ladon, FRPC, WMIHACKER, and ICMPinger. A custom keylogger called KMLOG is deployed to steal credentials.
The group maintains persistence through three distinct loaders—DUNLOADER, TESDAT, and DMLOADER—which load follow-up payloads directly into memory. These payloads include Cobalt Strike Beacons, rootkits, and data theft tools. Uniquely, the group uses living-off-the-land (LotL) techniques, leveraging legitimate system files like syssetup.dll to stealthily install rootkits.
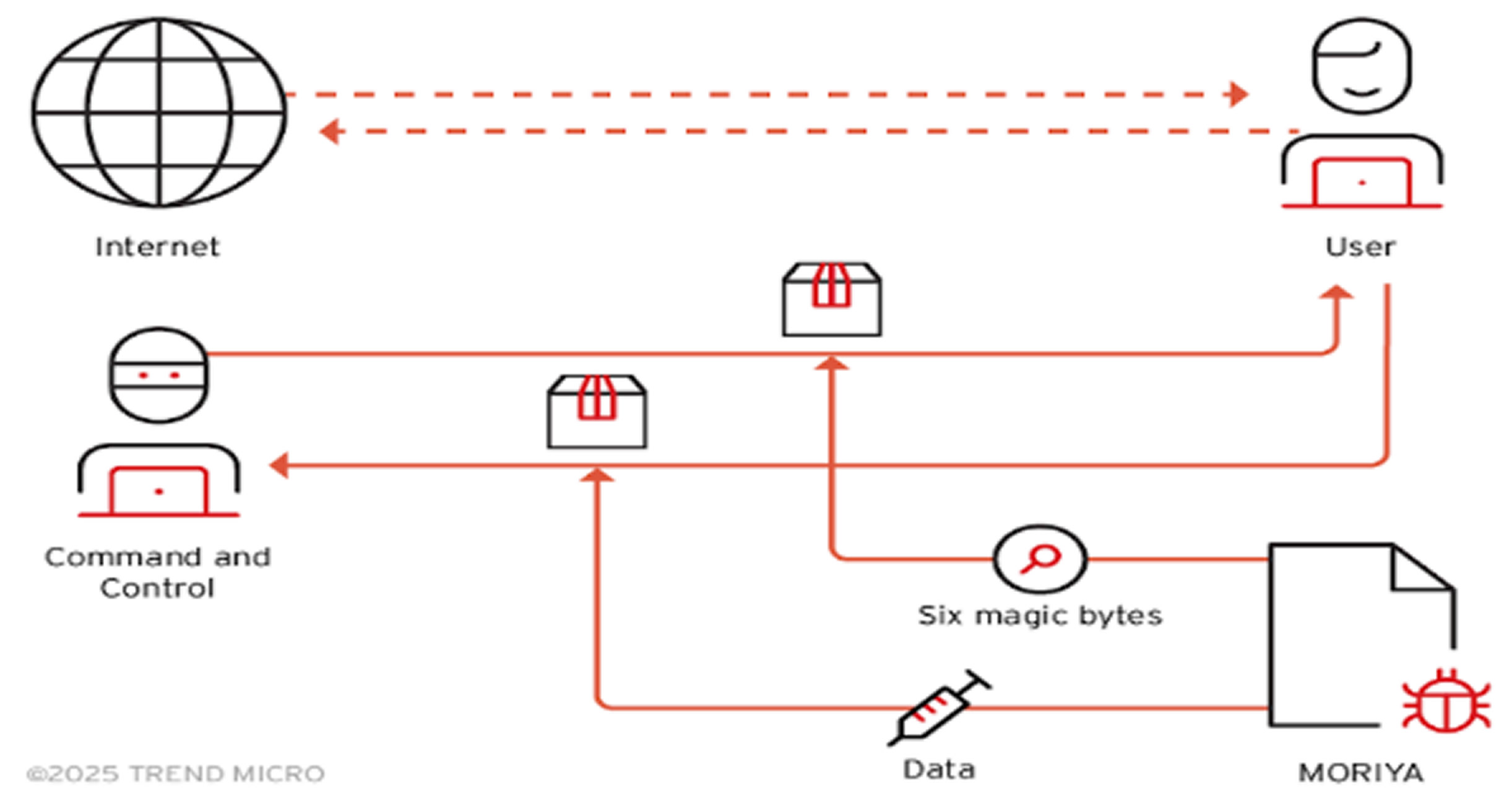
Moriya monitors incoming TCP packets for malicious data, injecting shellcode into processes like svchost.exe. Meanwhile, KRNRAT, built from five open-source projects, offers functions like file hiding, process manipulation, and encrypted C2 communications. KRNRAT also uses a user-mode agent injected into svchost.exe to maintain access.
Before exfiltrating files, TESDAT gathers sensitive document types (.pdf, .doc, .xls, .ppt, etc.), places them in a “tmp” folder, and compresses them with WinRAR using a specific password.
For data exfiltration, Earth Kurma relies on custom tools like SIMPOBOXSPY, which uploads archives to Dropbox, and ODRIZ, which sends them to OneDrive using a refresh token.
Trend Micro emphasizes that Earth Kurma remains highly active, continuously adapting its tools and even exploiting victim infrastructure to maintain a stealthy presence.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.


