Microsoft has raised alarms over a newly identified cyber threat cluster known as Storm-2372
which has been linked to a series of sophisticated cyberattacks across multiple industries. Since August 2024, this threat group has been actively targeting various sectors, including government agencies, non-governmental organizations (NGOs), IT services, defense, telecommunications, healthcare, higher education, and the energy industry, including oil and gas. These attacks have spanned across different regions, affecting organizations in Europe, North America, Africa, and the Middle East.
Based on its investigation, Microsoft assesses with medium confidence that Storm-2372 is aligned with Russian geopolitical interests, as indicated by its victimology, attack techniques, and operational tradecraft. The threat actors behind these attacks rely on social engineering tactics to deceive users, particularly through popular messaging applications like WhatsApp, Signal, and Microsoft Teams. The attackers impersonate influential figures relevant to their targets, establishing trust before launching their malicious activities.
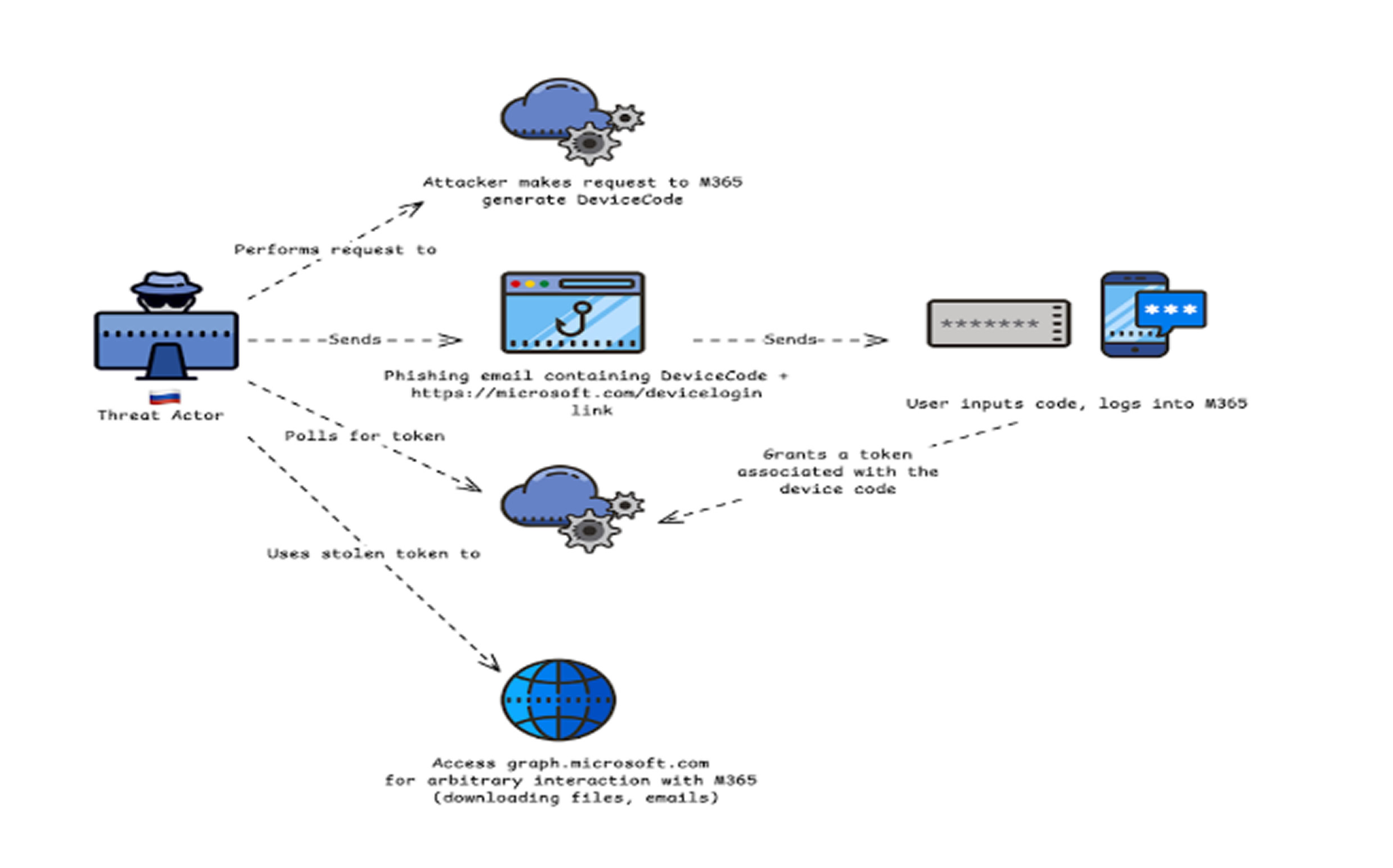
Storm-2372 employs an advanced phishing technique known as "device code phishing," which enables them to steal authentication tokens and hijack user sessions. The attackers trick victims into logging into Microsoft productivity applications under the guise of verifying their credentials or joining a meeting. However, the authentication process is actually compromised, allowing the attackers to intercept the tokens generated during login. These stolen tokens grant persistent access to the victim's account, enabling Storm-2372 to bypass password authentication and multi-factor authentication (MFA) in some cases.
A common attack method involves sending phishing emails disguised as Microsoft Teams meeting invitations. When the recipient clicks the link, they are redirected to a page that prompts them to authenticate using a device code generated by the threat actor. Once the victim enters this code into the legitimate Microsoft sign-in page, Storm-2372 gains full control over the authenticated session by capturing the access and refresh tokens.
Once inside a compromised account, Storm-2372 leverages the stolen session tokens to move laterally within the organization. The attackers use their access to send phishing emails from the compromised account to other employees, increasing the attack’s impact while making it more difficult to detect. By exploiting Microsoft's Graph API services, they conduct keyword-based searches within emails and internal messages to identify sensitive information.
Their search queries often include terms like “username,” “password,” “admin,” “credentials,” “TeamViewer,” “AnyDesk,” “ministry,” and “gov”, indicating their focus on extracting confidential government and corporate data. Once the relevant emails are identified, the attackers exfiltrate the information, potentially using it for further cyber espionage, financial gain, or disruptive operations.
UPDATES
In a security update on February 14, 2025, Microsoft reported that Storm-2372 has modified its tactics to strengthen persistence within compromised environments. The attackers have started exploiting a specific client ID associated with the Microsoft Authentication Broker, which allows them to:
- Obtain refresh tokens, granting extended access without requiring repeated logins.
- Register an attacker-controlled device within Entra ID (formerly Azure Active Directory), embedding their presence inside the organization’s infrastructure.
- Harvest emails and other sensitive data from Microsoft 365 environments.
- Utilize regional proxy servers to mask their login attempts and avoid triggering security alerts based on location.
These new tactics demonstrate Storm-2372’s adaptability and operational sophistication, allowing them to evade detection and maintain long-term access to compromised systems.
Cybersecurity firm Volexity has linked the device code phishing technique to at least three separate Russian-affiliated cyber espionage groups conducting spear-phishing attacks on Microsoft 365 accounts since mid-January 2025. These groups include:
APT29 (also known as BlueBravo, Cozy Bear, Midnight Blizzard, and The Dukes) – A highly advanced Russian intelligence-linked group specializing in nation-state cyber espionage.
UTA0304 – A separate Russian threat actor known for targeting government agencies and research institutions through deceptive spear-phishing tactics.
UTA0307 – Another Russian-linked cyber group using Microsoft Teams-based phishing campaigns to breach organizations.
One notable attack analyzed by Volexity involved UTA0304 impersonating an official from the Ukrainian Ministry of Defence. The attackers first approached their target via Signal, posing as a trusted government representative. They then persuaded the victim to move the conversation to a different secure messaging app called Element, where they sent a carefully crafted spear-phishing email.
The email contained a link, supposedly inviting the target to join a confidential discussion, but in reality, the link redirected them to a Microsoft sign-in page requesting a device code. Once the victim entered the code, the attackers gained full access to their Microsoft 365 account, exfiltrating sensitive emails and documents.
Similar tactics have been observed with CozyLarch and UTA0307, where attackers lured victims into Microsoft Teams meetings as a pretext to steal their login credentials and gain unauthorized access.
Volexity researchers suspect that these Russian cyber groups may be part of a single coordinated operation running multiple attack campaigns simultaneously. The goal appears to be rapid exploitation of the device code phishing method before widespread countermeasures are implemented. This suggests a high level of planning and coordination among Russian-linked threat actors targeting government agencies, financial institutions, think tanks, and research organizations worldwide.
To combat the growing threat posed by Storm-2372, Microsoft and other cybersecurity experts recommend organizations take the following precautions:
- Disable device code authentication flows wherever possible to prevent exploitation.
- Enforce phishing-resistant MFA, such as hardware-based security keys (FIDO2 tokens) or certificate-based authentication.
- Apply the principle of least privilege, ensuring that users only have access to the resources necessary for their role.
- Monitor login activity for unusual sign-ins, particularly from unfamiliar devices or locations.
- Implement strict email filtering and anti-phishing defenses to detect and block deceptive emails.
- Educate employees on social engineering tactics to recognize and report phishing attempts.