In today’s threat landscape marked by increasingly sophisticated cyberattacks, cloud complexity, expanding identity surfaces, and AI‑driven threats organizations can no longer rely solely on fragmented security tools. They need visibility, correlation, automation, and real‑time insights across their entire digital ecosystem. This is where Security Information and Event Management (SIEM) becomes indispensable.
SIEM has evolved from a log‑collection engine into the central intelligence hub of enterprise cybersecurity, enabling organizations to detect, investigate, and respond to threats with speed and accuracy.
What Is SIEM?
Security Information & Event Management (SIEM) is a security solution that combines:
Security Information Management (SIM)
Long‑term storage, analysis, and reporting of security logs.
Security Event Management (SEM)
Real‑time monitoring, correlation, alerting, and incident response.
Together, SIEM systems provide a unified view of security activity across an organization pulling data from networks, servers, cloud platforms, applications, endpoints, identity providers, firewalls, and threat‑intelligence feeds.
Modern SIEM platforms integrate AI/ML analytics, user/entity behavioral analytics (UEBA), and automated response capabilities, making them a fundamental component of Security Operations Center (SOC) workflows.
Why SIEM Matters: Core Benefits
Centralized Visibility Across the Enterprise
SIEM consolidates logs from thousands of devices, users, and cloud environments into one dashboard. In a world where enterprises operate hybrid and multi‑cloud systems, SIEM offers the visibility required to monitor vast, dynamic infrastructures.
Advanced Threat Detection
By correlating events from different systems, SIEM can detect complex attack patterns such as:
- Credential compromise
- Privilege escalation
- Insider threats
- Lateral movement
- Malicious API usage
- Cloud misconfigurations
- Supply chain abuse
Advanced SIEM platforms use machine learning to identify anomalies and deviations from normal behavior.
Accelerated Incident Response
SIEM systems integrate with SOAR (Security Orchestration, Automation, and Response) platforms to automate triage, enrichment, containment, and remediation—drastically reducing mean time to detect (MTTD) and mean time to respond (MTTR).
Compliance and Audit Readiness
Industries governed by strict regulations (PCI‑DSS, HIPAA, ISO 27001, GDPR, NIST, etc.) rely on SIEM for:
- Log retention
- Compliance reporting
- Evidence collection
- Audit trails
Forensics & Post‑Incident Analysis
With historical log storage and correlation, SIEM helps security teams reconstruct attack timelines, understand root causes, and prevent recurrence.
Key Features of Modern SIEM Solutions
Log Collection & Normalization
Ingesting and structuring data from on‑prem, cloud, and third‑party tools.
Correlation Rules & Threat Models
Detecting patterns to identify threats that single systems might miss.
Real‑Time Alerting & Dashboards
Providing actionable insights for SOC analysts.
UEBA (User and Entity Behavior Analytics)
Detecting unusual behavioral patterns, such as:
- Impossible travel logins
- Excessive data exfiltration
- Privilege misuse
- Insider risk activity
Threat Intelligence Integration
Ingesting known bad IPs, domains, malware signatures, and TTPs from frameworks such as MITRE ATT&CK.
Automated Response (SIEM + SOAR)
Triggering actions like:
- Disabling accounts
- Blocking IPs
- Isolating endpoints
- Enriching alerts with context
Cloud Security Monitoring
Modern SIEM tools support AWS, Azure, GCP, and SaaS platforms, enabling posture detection and cloud threat analytics.
SIEM Architecture: How It Works
Data Sources
Logs from firewalls, endpoints, cloud platforms, identity providers, applications, and databases.
Ingestion Layer
Collectors, agents, or API integrations forward logs.
Normalization & Parsing
Structured into common formats.
Correlation & Analytics Engine
Pattern recognition, anomaly detection, threat modeling.
Alerting & Dashboards
SOC teams receive prioritized alerts.
SOAR & Response Layer
Automated playbooks or analyst-driven response.
Storage & Compliance Archive
Long-term secure log retention for audits.
Traditional SIEM vs. Next‑Gen SIEM
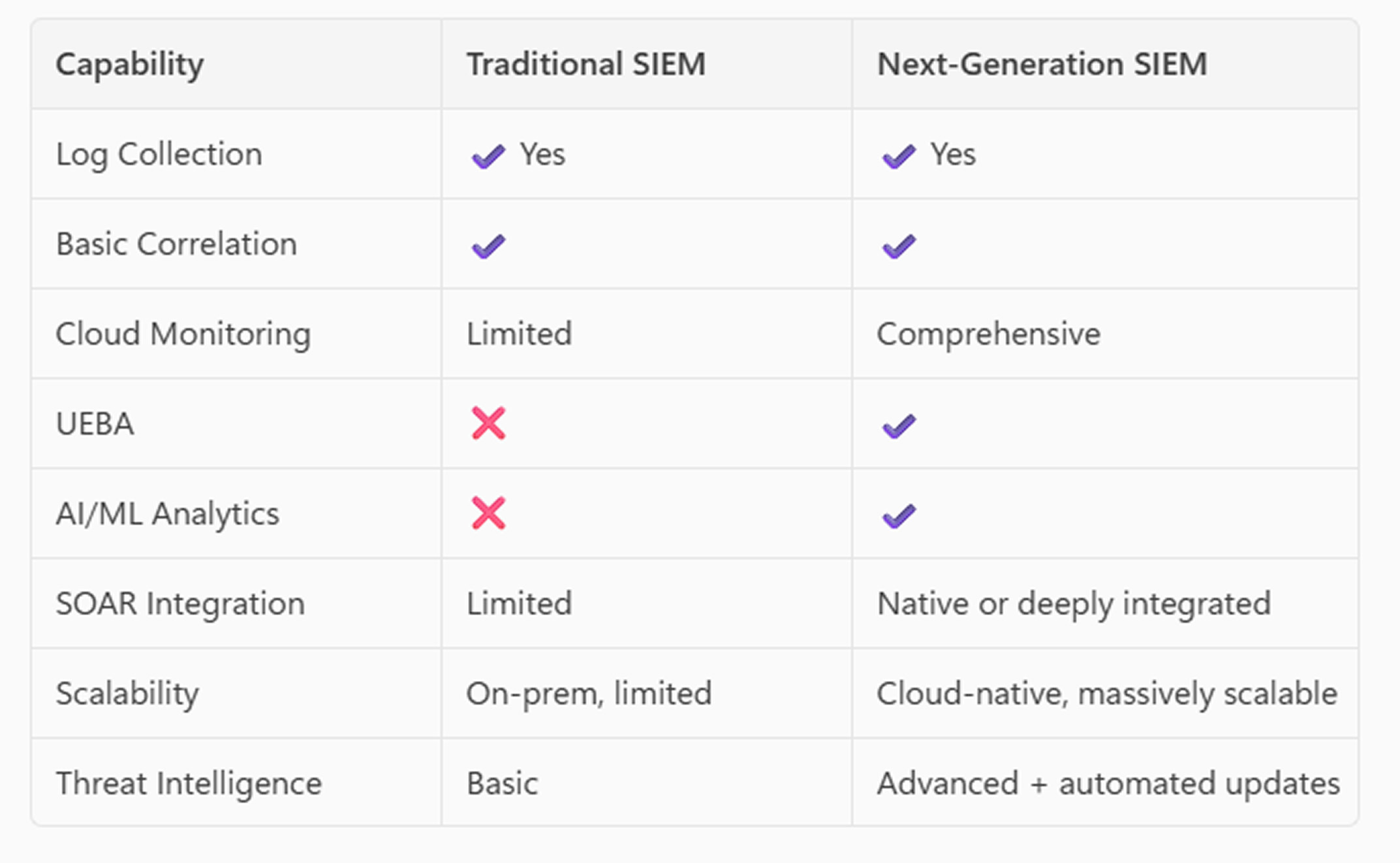
Next‑gen SIEM is purpose‑built for cloud, APIs, and modern attack chains.
Common SIEM Platforms in the Market
Modern enterprises often adopt one of the following:
- Splunk Enterprise Security
- Microsoft Sentinel (Cloud-native SIEM/SOAR)
- IBM QRadar
- Elastic SIEM
- LogRhythm
- ArcSight
- Google Chronicle
- Securonix (UEBA-first SIEM)
The choice depends on business size, cloud posture, budget, and SOC maturity.
Challenges of SIEM Implementation
Despite its advantages, organizations face challenges such as:
High Cost & Licensing Complexity
Log ingestion fees can skyrocket, especially for large environments.
Skill Shortage
SOC analysts and SIEM engineers require specialized expertise.
Alert Fatigue
Poorly tuned correlation rules overwhelm SOC teams with noise.
Log Quality Issues
Incomplete, noisy, or improperly parsed logs reduce SIEM effectiveness.
Integration Complexity
Enterprises often struggle with connecting legacy systems or hybrid environments.
Best Practices for SIEM Success
Implementing SIEM effectively requires:
- Define clear use cases before ingestion.
- Start small, expand gradually.
- Tune correlation rules to reduce false positives.
- Integrate threat intelligence feeds.
- Adopt MITRE ATT&CK as a detection framework.
- Pair SIEM with SOAR for automated response.
- Ensure continuous log quality auditing.
- Invest in analyst training and runbooks.
- Leverage UEBA for contextual user behavior insights.
The Future of SIEM
The next evolution of SIEM will be shaped by:
✓ AI‑Native Analytics
✓ Autonomous SOC Operations
✓ Deeper Cloud and SaaS Visibility
✓ Identity‑centric Detection Models
✓ Full integration with XDR ecosystems
✓ Zero Trust‑aligned detection & response
As threat actors leverage automation, LLMs, and AI‑powered offensive tools, SIEM platforms will increasingly rely on machine learning, predictive modeling, and adaptive threat intelligence to maintain a defensive edge.
Conclusion
Security Information & Event Management (SIEM) is the backbone of modern cybersecurity operations. It empowers organizations with visibility, threat detection, compliance readiness, and coordinated response across increasingly complex environments. While SIEM deployment can be challenging, the benefits when implemented correctly are substantial and foundational to building a resilient cybersecurity posture. As cyber threats evolve in speed and sophistication, SIEM solutions will continue to serve as the central nervous system of enterprise security, aligning people, processes, and technology for real‑time, intelligence‑driven defense.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



