Crocodilus Android Banking Trojan Expands to Europe and South America
A new Android banking trojan known as Crocodilus is rapidly gaining traction in cybercriminal campaigns targeting users in Europe and South America. Initially observed in limited test runs, the malware has now been deployed in full-scale attacks, leveraging social media ads and advanced stealth features to compromise devices.
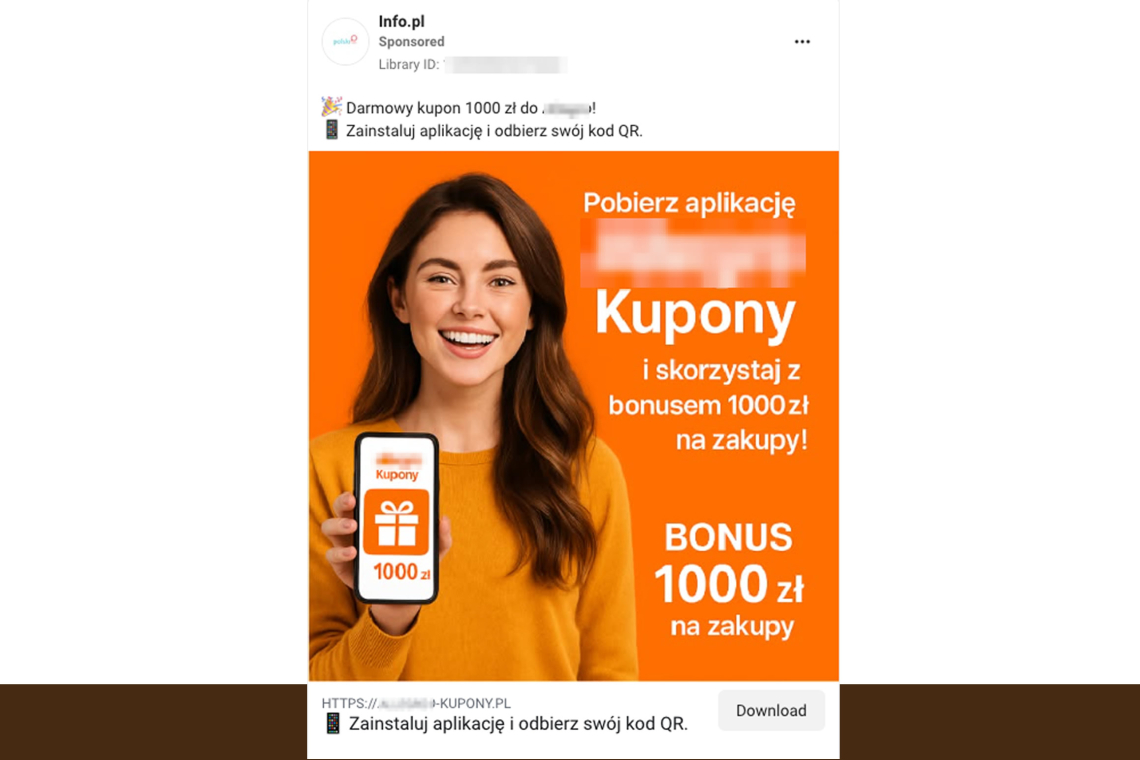
According to cybersecurity researchers at ThreatFabric, Crocodilus spreads via malicious ads, primarily on platforms like Facebook. These ads promote fake reward points or software updates, which redirect users to compromised websites that deliver the malware. In one notable campaign, Polish users were lured through bogus banking and shopping apps, while another targeted Spanish users by posing as a browser update aimed at nearly all major Spanish banks.
Crocodilus was first detected in Turkey but has since expanded into countries such as Argentina, Brazil, the United States, Indonesia, and India. This expansion highlights its evolution into a global threat with a growing list of impersonated apps.
The malware includes a number of dangerous features:
- Seed phrase and crypto key theft: New variants now include a parser that extracts seed phrases and private keys from cryptocurrency wallets, enabling direct asset theft.
- Fake contact injection: A key update allows attackers to modify a victim's contact list. Upon receiving a specific command, the malware adds a fake contact such as “Bank Support,” which attackers can use for social engineering and phishing calls.
- Enhanced obfuscation: Crocodilus uses techniques like code packing and XOR encryption to avoid detection. It also uses AccessibilityLogging and regex-based screen parsing to extract high-value data cleanly and efficiently.
These capabilities make the malware particularly effective at bypassing security measures and fraud detection systems.
“Crocodilus is no longer regionally confined,” ThreatFabric notes. “It has become a global threat with increasingly sophisticated tactics.”
The report, which includes indicators of compromise (IoCs), concludes that the threat actor behind Crocodilus is likely organized and adaptive, emphasizing the need for constant vigilance. Users and organizations are urged to adopt proactive mobile security measures, avoid downloading apps from unknown sources, and be cautious of links and offers on social media.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.