Cybersecurity experts are warning about a growing wave of phishing attacks using QR codes, a tactic now known as “quishing.” These codes hide malicious links that lead users to fake login pages or malware downloads. Because QR codes must be scanned visually, often on mobile devices, they bypass traditional email security filters.
Early attacks were broad and generic, posing as alerts from popular services. Now, attackers are crafting more targeted messages and embedding QR codes into innocent-looking images. One campaign impersonated a cloud storage provider, tricking users into scanning a code that led to a fake login page.
Researchers at Barracuda noted that these attacks rely more on social engineering than technical complexity. As defenses improved, attackers introduced split QR codes, two image fragments that appear harmless alone but form a malicious code when combined in an email. Victims scanning these codes are redirected to phishing sites or malware.
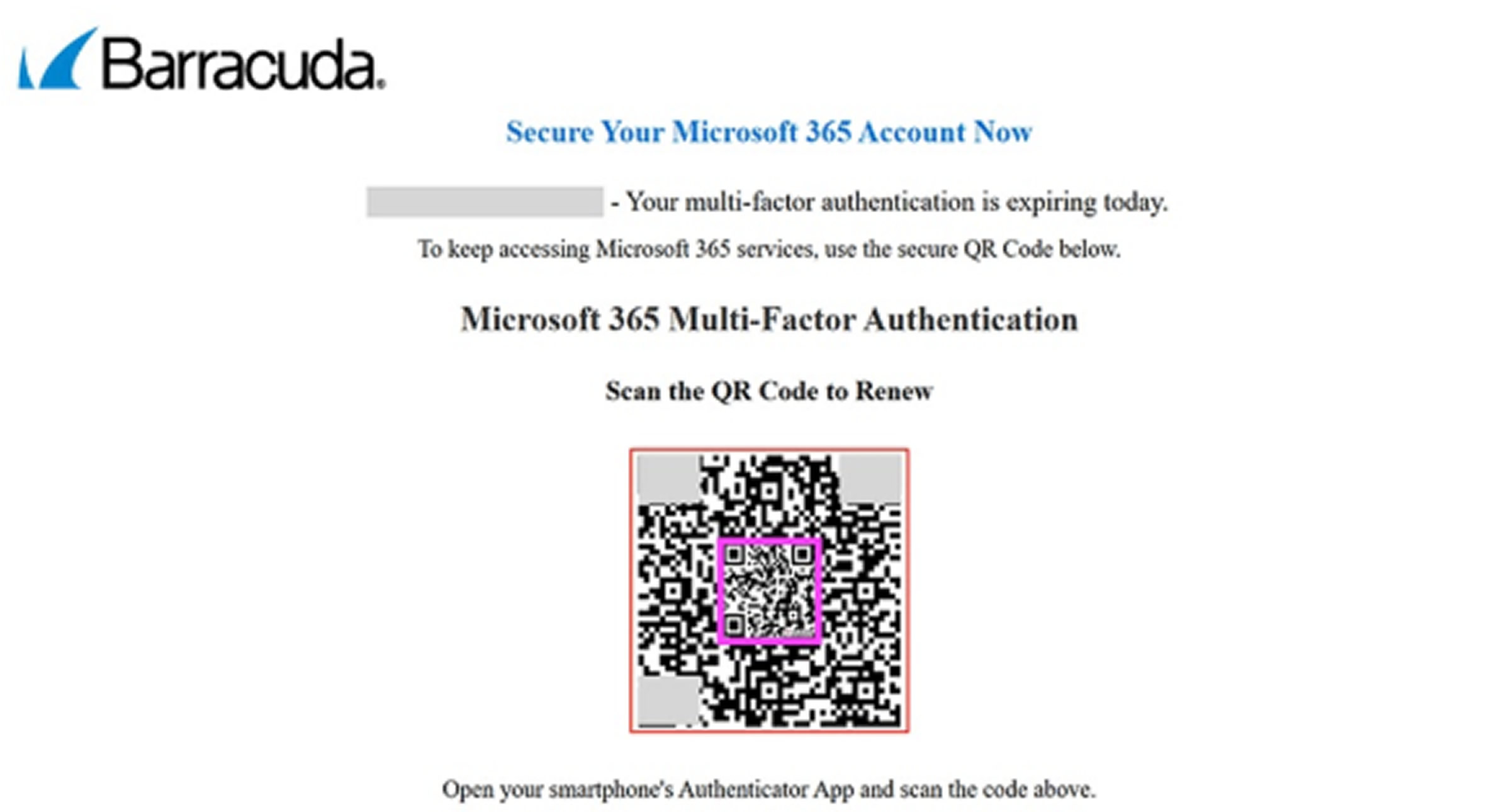
More advanced techniques include nested QR codes, where a benign inner code is surrounded by a malicious outer layer. Basic scanners read the safe link, while advanced tools may detect the hidden threat. This method helps attackers evade detection by QR analysis software.
To stay protected, organizations need layered defenses, AI-powered image analysis, and strong user awareness. As security improves, attackers are expected to keep adapting their methods.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



