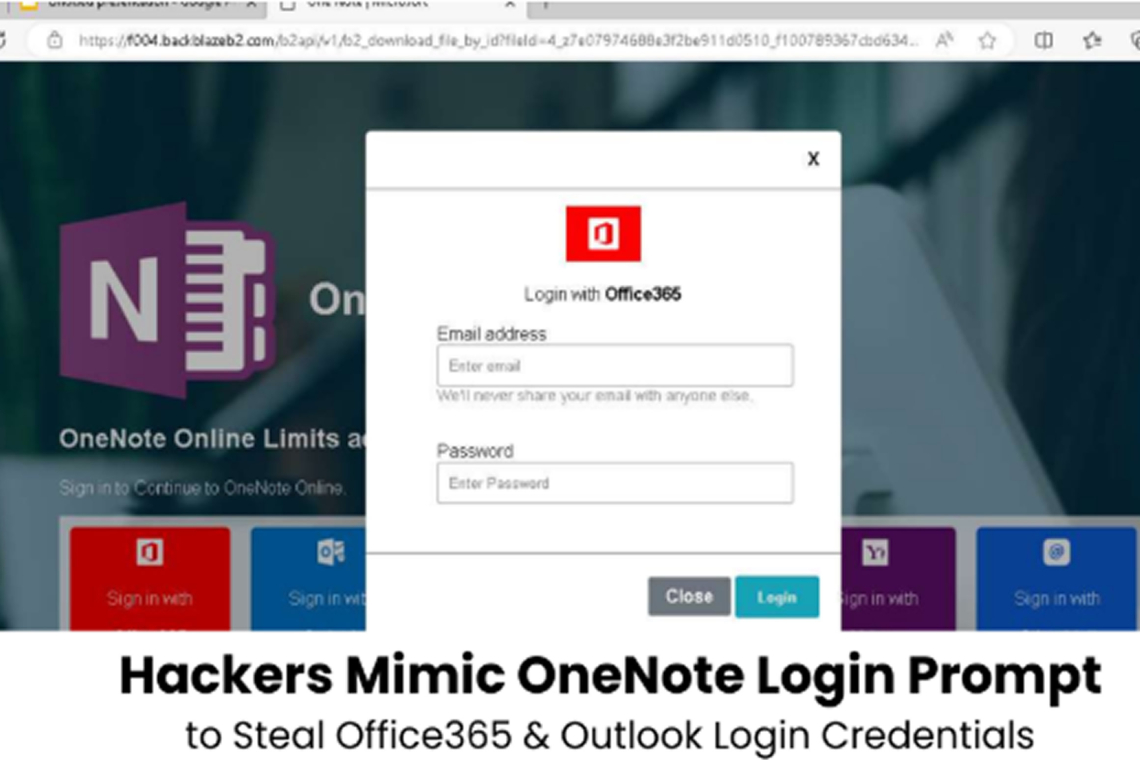
Sophisticated Phishing Campaign Targets Italian and U.S. Users via Fake OneNote Prompts
A highly targeted phishing operation is aiming at users in Italy and the United States using fake Microsoft OneNote login pages to steal Office 365 and Outlook credentials.
The campaign uses legitimate cloud platforms and Telegram bots to exfiltrate data, making it difficult for traditional security systems to detect the malicious activity.
Trusted Services Used to Host Phishing Pages
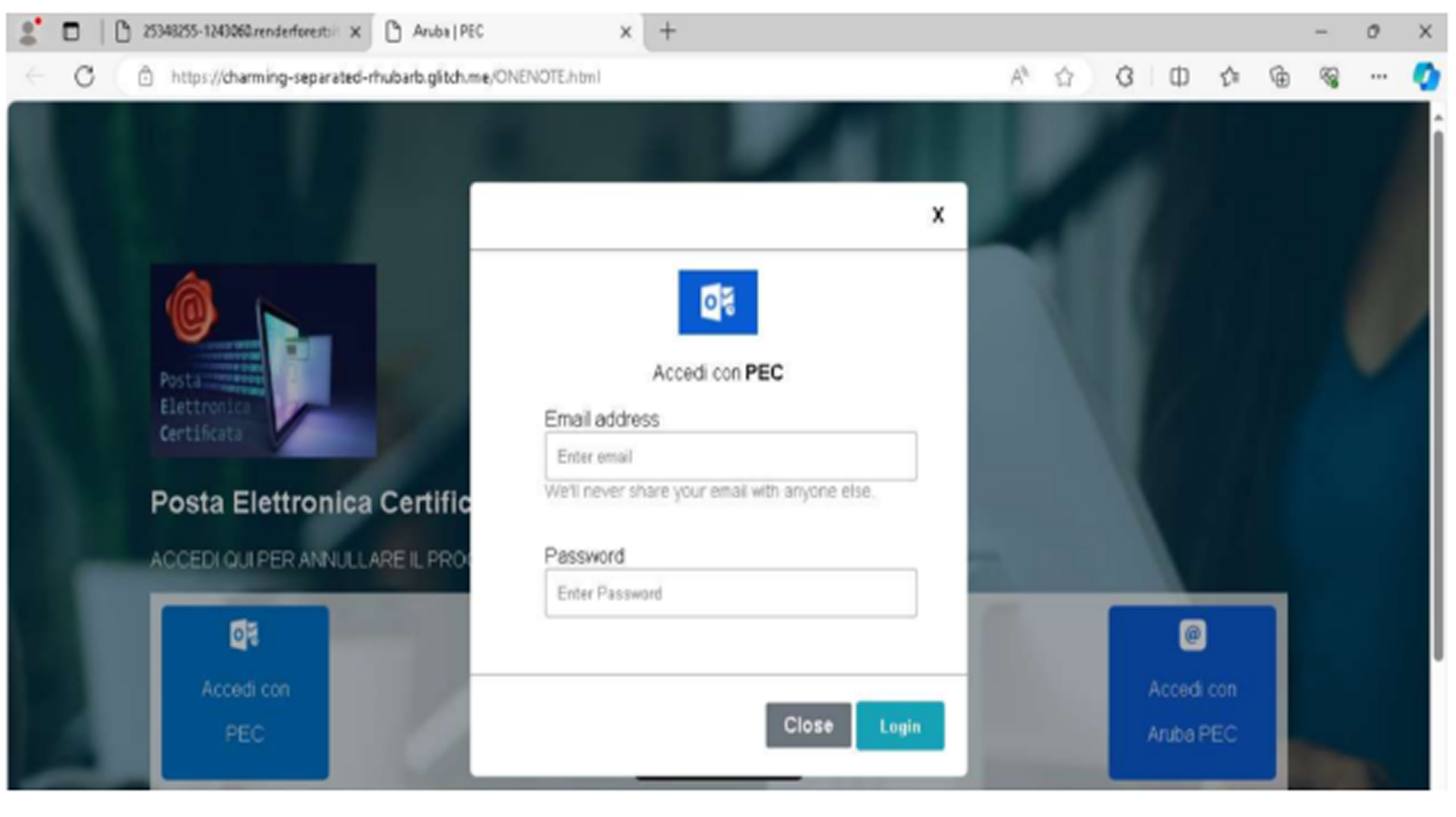
Attackers begin by hosting convincing fake login pages on trusted platforms such as Notion, Glitch, Google Docs, and RenderForest. Victims typically receive phishing emails with subject lines like “New Document Shared with you,” which redirect them to fraudulent OneNote login prompts.

These phishing pages offer several login options, including Office365, Outlook, Rackspace, Aruba Mail, PEC, and other services. According to a report from ANY.RUN, the campaign specifically targets Italian users and organizations, featuring Italian-language content and Italian terms in subdomains. The operation has been active since at least January 2022 and continues to evolve.
Telegram Bots Used for Data Exfiltration
The phishing pages deploy JavaScript to capture credentials and IP addresses. The stolen data is then sent to Telegram bots using hardcoded bot tokens and chat IDs embedded in the scripts. Security researchers identified several bots used over time, including “Sultanna,” “remaxx24,” and “Resultant.”
To maintain the illusion of legitimacy, victims are redirected to actual Microsoft OneNote login pages after their credentials are stolen.
Campaign Shows Technical Adaptation
The operation has evolved considerably since its discovery. Initial variants used basic URL obfuscation and web form data submission. By February 2022, attackers shifted to using Telegram for data exfiltration, layering URLs two to four levels deep.
Between July and December 2024, the group briefly experimented with Base64 encoding but later abandoned it for reasons that remain unclear. Despite the use of Telegram, the attackers avoid more advanced evasion techniques, suggesting they may prioritize credential harvesting over delivering malware payloads.
Experts Urge Heightened Vigilance
Security experts advise organizations to monitor for network traffic involving Telegram’s API, especially requests containing known bot tokens. They also recommend detecting behavioral patterns like domain redirection chains that follow a Notion to Glitch to Telegram API sequence.
The campaign’s targeting of PEC, Italy’s official certified email system, raises concerns that the attackers may aim to carry out business email compromise or sell access on cybercriminal forums.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.