Cybercriminals are exploiting Cascading Style Sheets (CSS) to evade spam filters and track user activities
Cybercriminals are exploiting Cascading Style Sheets (CSS) to evade spam filters and track user activities, posing significant security and privacy risks, according to new research from Cisco Talos.
"CSS features allow attackers and spammers to monitor user actions and preferences, even though email clients restrict certain dynamic content, like JavaScript," said Talos researcher Omid Mirzaei in a recent report.
Building on previous findings about a surge in email threats using hidden text salting in late 2024, researchers found that attackers manipulate legitimate HTML and CSS features to insert hidden content that can bypass spam filters. Specifically, threat actors use CSS properties such as text-indent and opacity to conceal malicious content in email bodies, sometimes leading recipients to phishing sites.
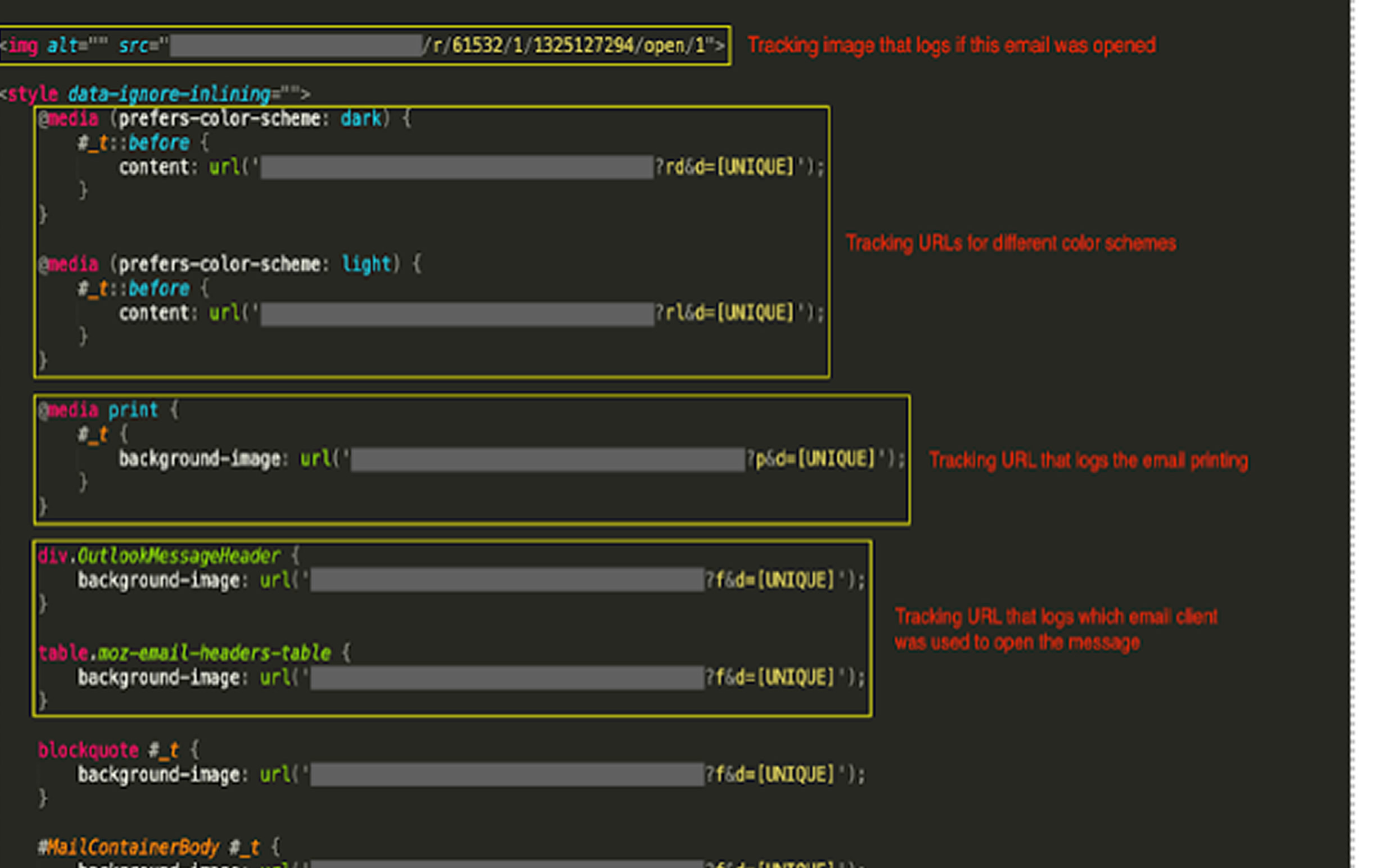
Additionally, CSS enables cybercriminals to track user behavior through spam emails. By embedding properties like the @media at-rule, attackers can conduct fingerprinting attacks, gathering details about recipients’ email clients, system configurations, and actions such as viewing or printing emails.
"This technique allows threat actors to detect users' font and color preferences, language settings, and even screen resolution," Mirzaei noted.
To counter these threats, experts recommend implementing advanced filtering techniques to detect hidden text manipulation and using email privacy proxies to protect users from CSS-based tracking.


