Misconfigured Docker API instances have become the target of a new malware campaign that transforms them into a cryptocurrency mining botnet. The attacks, designed to mine
for Dero currency, are notable for their worm-like capabilities to propagate the malware to other exposed Docker instances and rope them into an ever-growing horde of mining bots.
Kaspersky reported that an unidentified threat actor gained initial access to running containerized infrastructure by exploiting insecurely published Docker APIs. This access was then weaponized to create an illicit cryptojacking network. According to security researcher Amged Wageh, the compromise led to existing containers being hijacked and new containers being created not only to mine cryptocurrency but also to launch attacks that spread the malware to other networks.
The attack consists of two main components: a propagation malware disguised as “nginx” that scans the internet for exposed Docker APIs, and the “cloud” Dero cryptocurrency miner. Both payloads are developed in Golang. The use of the name “nginx” is deliberate to masquerade as the legitimate web server and avoid detection.
The propagation malware is designed to monitor its activities, launch the miner, and then enter an infinite loop where it generates random IPv4 subnets to identify more vulnerable Docker instances with the default API port 2375 open. It checks if the remote Docker daemon on these hosts is running and responsive. If it finds a responsive Docker daemon, it creates a new malicious container with a randomly generated name, prepares it by updating packages, and installs necessary tools such as masscan and docker.io to facilitate further spreading.
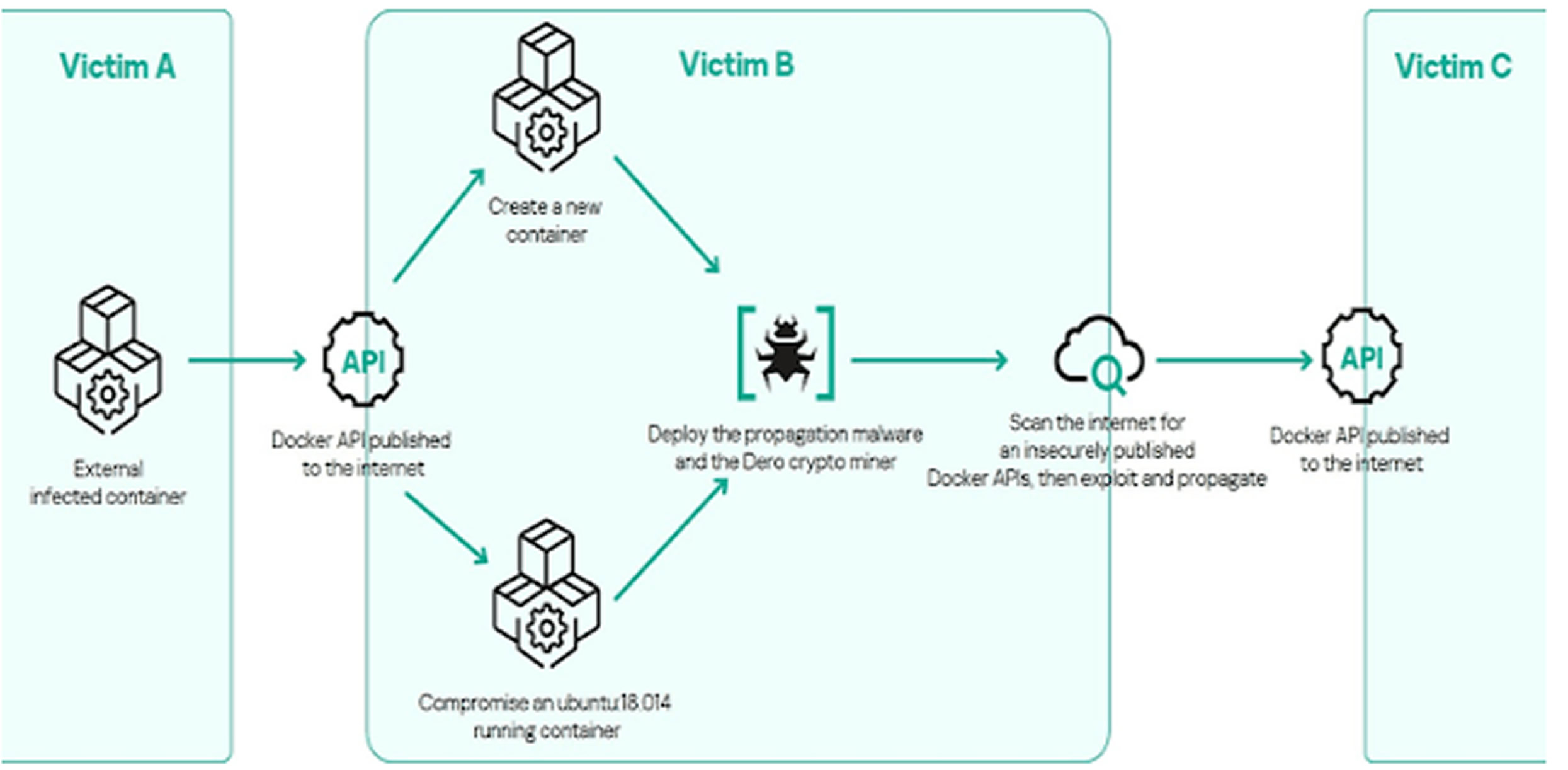
The malware then copies the two payloads “nginx” and “cloud” into the new container and establishes persistence by adding the “nginx” binary to the shell login aliases, ensuring it runs automatically. Notably, the malware is engineered to specifically target Ubuntu-based running containers on vulnerable remote hosts.
This campaign exemplifies the growing threat posed by misconfigured Docker APIs, highlighting the importance of securing container environments and limiting exposed management interfaces to prevent such cryptojacking botnets from spreading and consuming valuable resources.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



