Medusa ransomware-as-a-service (RaaS) operation have been found deploying a malicious driver named ABYSSWORKER
The operators behind the Medusa ransomware-as-a-service (RaaS) operation have been found deploying a malicious driver named ABYSSWORKER as part of a bring your own vulnerable driver (BYOVD) attack. This technique is used to disable anti-malware tools and evade detection.
According to Elastic Security Labs, a recent Medusa ransomware attack involved delivering the encryptor through a loader packed with HeartCrypt, a packer-as-a-service (PaaS). The attack also deployed a revoked certificate-signed driver from a Chinese vendor, named ABYSSWORKER, which was installed on the victim’s machine to disable endpoint detection and response (EDR) solutions.
The list of some of the I/O control codes is below -
- 0x222080 - Enable the driver by sending a password "7N6bCAoECbItsUR5-h4Rp2nkQxybfKb0F-wgbJGHGh20pWUuN1-ZxfXdiOYps6HTp0X"
- 0x2220c0 - Load necessary kernel APIs
- 0x222184 - Copy file
- 0x222180 - Delete file
- 0x222408 - Kill system threads by module name
- 0x222400 - Remove notification callbacks by module name
- 0x2220c0 - Load API
- 0x222144 - Terminate process by their process ID
- 0x222140 - Terminate thread by their thread ID
- 0x222084 - Disable malware
- 0x222664 - Reboot the machine
The driver, identified as "smuol.sys," mimics the legitimate CrowdStrike Falcon driver ("CSAgent.sys"). Dozens of ABYSSWORKER samples have been found on VirusTotal, dating back to August 8, 2024. All discovered variants were signed using likely stolen, revoked certificates from Chinese companies, allowing them to bypass security systems unnoticed. The same EDR-killing driver was previously reported by ConnectWise in January 2025 under the name "nbwdv.sys."
Once deployed, ABYSSWORKER manipulates system processes by adding the process ID to a global protected process list. It listens for incoming device I/O control requests and executes commands accordingly. These commands allow the malware to manipulate files, terminate processes, disable EDR systems, and even reboot the compromised machine.
One of the most concerning functions, identified as I/O control code 0x222400, removes registered security callbacks, effectively blinding security software. This method is similar to techniques used by other EDR-disabling tools like EDRSandBlast and RealBlindingEDR.
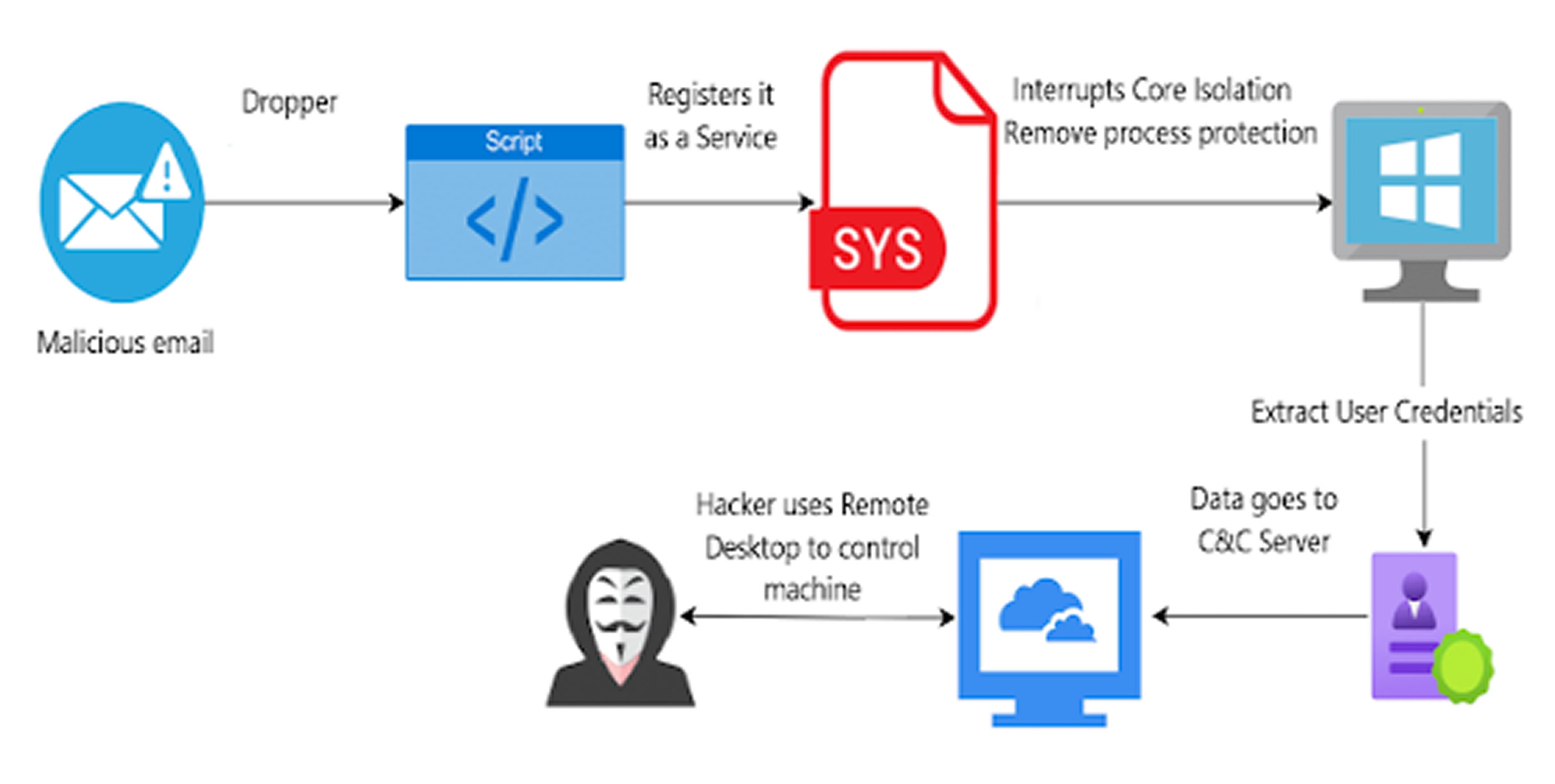
The findings come as Venak Security reported another case of threat actors exploiting a vulnerable kernel driver from Check Point's ZoneAlarm antivirus software. This flaw allowed attackers to gain elevated privileges and disable Windows security features such as Memory Integrity. Using these privileges, the attackers established a persistent Remote Desktop Protocol (RDP) connection, providing long-term access to infected systems. Check Point has since addressed the vulnerability.
"As vsdatant.sys operates with high-level kernel privileges, attackers were able to exploit its vulnerabilities to bypass security protections, gain full control over infected machines, and exfiltrate sensitive user credentials," the company stated.
Additionally, researchers have linked the RansomHub ransomware operation, also known as Greenbottle and Cyclops, to the use of a newly discovered multi-function backdoor named Betruger. This malware possesses features commonly found in pre-ransomware attack tools, including screenshot capturing, keylogging, network scanning, privilege escalation, credential theft, and data exfiltration to remote servers.
Broadcom-owned Symantec noted that Betruger appears designed to reduce the number of external tools needed during an attack. Unlike most ransomware groups that rely on publicly available tools such as Mimikatz and Cobalt Strike, RansomHub's use of a custom-built backdoor marks a shift in ransomware tactics.
Found this article interesting? Follow us on X(Twitter) and Instagram to read more exclusive content we post.


